International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 12, December 2014)
88
Performance Enhancement of Transmission Control Protocol
over Wireless Ad-hoc Networks
Salah Zaher
Lecturer at Modern Academy in Maadi
For Computer Science and Management Technology, Computer Science Dept., Cairo, Egypt
Abstract—Mobile Ad Hoc Network (MANET) is a multi-hop wireless network in which any node can connect to any other node other node without a centralized infrastructure. The nodes participating in a MANET operate both as hosts and as routers. TCP is mainly developed for wired networks and it is required to adapt the famous protocol to work perfectly in wireless networks.TCP implements both flow control and congestion control. Flow control prevents the TCP receiver’s buffer from being overflowed while congestion control avoids congestion collapse within the network. The congestion control continuously probes the network for resources. Some versions of TCP use the additive increase multiplicative decrease algorithm (AIMD), to speed up loss recovery and ensure network stability. An alternative algorithm to AIMD is the equation-based congestion control. The latter attempts to reproduce TCP behaviour analytically, but an accurate modelling is too hard to achieve. This is a subject of great interest in the research community nowadays. In MANET the standard TCP when works on multi-hop faces many problems related to nature of wireless media like performance degradation and unstable connectivity. This research presents a study for a modified TCP protocol in order to enhance the behaviour of the protocol in Ad-hoc wireless networks. In this paper two modifications to the standard TCP were proposed by adjusting TCP's behaviour during slow start and congestion avoidance phases. The throughput of the proposed protocols has increased over the throughput of the standard TCP protocol. Glomosim simulator was used which is one of known simulators for Ad-hoc wireless networks.
Keywords— TCP, Ad-hoc, MANET, AIMD.
I. INTRODUCTION
Nodes in are distributed and can be statics or mobile. The main advantage of Ad-hoc Networks is that its nodes can be self-organize allowing nodes to connect to each other. The connections between the nodes do not need to establish pre existing infrastructure like other networks. Each node can work as a router to route data to its neighbour nodes. Ad – hoc networks can be used in places that can be difficult to prepare it with infrastructures like open areas.
In battles for example soldiers need to transfer data among themselves or to their leaders while their moving so, no server is established to manage the nodes connections. In these cases we need the nodes itself to do the role of the server to manage routing of data between itself and other nodes. The nodes can connect automatically to its neighbours making multi hops connections.
Many protocols like Bluetooth [1] [2] and IEEE 802.11[3] can support the ideas of Ad hoc networks and make it available for commercial purposes. Many research efforts have been put on this new challenging wireless environment. MANETs is used as a short cut stands for mobile Ad hoc networks, and SANETs stands for Ad hoc networks. The term Ad hoc networks used for both mobile Ad hoc networks (MANETs) and static Ad hoc networks (SANETs). Mobile Multi-hop Ad- hoc networks [4][5] are collections of mobile nodes connected together over a wireless medium. These nodes can freely and dynamically self-organize into arbitrary and temporary [6], “Ad-hoc” network topologies, allowing people and devices to seamlessly internetwork in areas with no pre-existing communication infrastructure. Bluetooth is considered an example of a single-hop Ad- hoc networks. The protocol 802.11 can also be used to implement the same ideas. A group of laptops can communicate sending and receiving data without the need of an access point. Single-hop Ad-hoc networks just interconnect devices that are within the same transmission range. This limitation can be overcome by exploiting the multi-hop Ad-hoc paradigm. In this new networking paradigm, the users' devices are the network, and they must cooperatively provide the functionalities that are usually provided by the network infrastructure. Nearby nodes can communicate directly by exploiting a single-hop wireless technology (e.g., Bluetooth, 802.11, etc.), while devices that are not directly connected communicate by forwarding their traffic via a sequence of intermediate devices. As, generally, the users’ devices are mobile, these networks are often referred to as Mobile Ad-hoc networks (MANETs).
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 12, December 2014)
89
MANETs can be used attractive in case of vehicle-to-vehicle communications, and home networking. Transmission control protocol (TCP) [7][8] is a transport layer protocol which provides reliable end to - end data delivery between end hosts in traditional wired network environment. In TCP, lost packets should be retransmitted. Thus, each TCP sender maintains a running average of the estimated round trip delay and the average deviation derived from it. If the acknowledgement is not received by the sender in certain time, sender should retransmit the packet again. All losses in wired networks are considered due to congestion.TCP uses congestion control mechanisms after detecting any packet loss. Since TCP is well very stable and well tested so, it has become the transport protocol in the Internet that supports many applications such as web access, file transfer and email. Due to its wide use in the Internet, it is desirable to use it for communications within wireless networks by making some modifications on the protocol to adapt with the nature of wireless networks. Nowadays, many applications use TCP as their transport protocol and hence pass through wireless links, which become common in the Internet. Over these links, packet losses are not due anymore only to overflows but can also be caused by link errors. Standard TCP can not distinguish between packet loss due to congestion or due to link error in communication [9] between nodes so it reduces its rate at each packet loss causing degradation in its performance. This reduction is not justified when there is no congestion and the consequence is that the throughput of TCP over wireless link is lower than what it could be. To increase its throughput, TCP should avoid reacting to a packet loss due to a link error as it does when it faces congestion. In mobile Ad- hoc networks, most packet losses are due to wireless misconnection, as well as radio channel errors. Therefore, although TCP performs well in wired networks, it will suffer from serious performance degradation in wireless networks if it misinterprets such non-congestion related losses as a sign of congestion and consequently invoke congestion control and avoidance procedures.
Consequently, when a packet is detected to be lost, either by timeout or by multiple duplicated ACKs, TCP slows down the sending rate by adjusting its congestion window. Unfortunately, wireless networks suffer from several types of losses that are not related to congestion, making TCP not adapted to this environment [10].
Numerous enhancements and optimizations have been proposed over the last few years to improve TCP performance over one-hop wireless (not necessarily Ad-hoc) networks. These improvements include infrastructure based WLANs [11] [12] [13] [14], mobile cellular networking environments [15][16], and satellite networks[17] [18]. Ad hoc networks inherit several features of these networks, in particular high bit error rates and path asymmetry, and add new problems that come from mobility and multi-hop communications, such as network partitions, route failures, and hidden (or exposed) terminals. The improvements of TCP depend mainly on differentiating between packet losses due to congestion that should activate the congestion control algorithm, and losses due to the specific features of MANETs. In order to do that, it is suggested that as TCP detects packet loss due to routing failures and notify sender to stop sending packets rout path is re-established.
II. PROPOSED TCPENHANCEMENTS
2.1 Slow Start modification (SSTCP)
Slow start phase in TCP commands is increasing exponentially increase (base of 2) in the congestion window (cwnd) size. Specifically, for every ACK received that acknowledges new data, cwnd may be incremented by at most the number of bytes in a full sized segment.
In standard TCP implementations an increment in cwnd by the maximum allowed amount of bytes will ocuur . It is required to to define a smaller increase while still retaining RFC compliance. Mimicking the approach of TCP Vegas in this regard, where the sending rate increase during slow start occurs every other ACK received , we similarly define a delayed increase. A variable SS_increase_thresh is defined which sets the number of ACKs that needed to be received before cwnd increases by a full sized segment
.
For instance, a value of one for SS_increase_thresh precisely emulates the slow start behavior of TCP by increasing the sending rate every other ACK received.
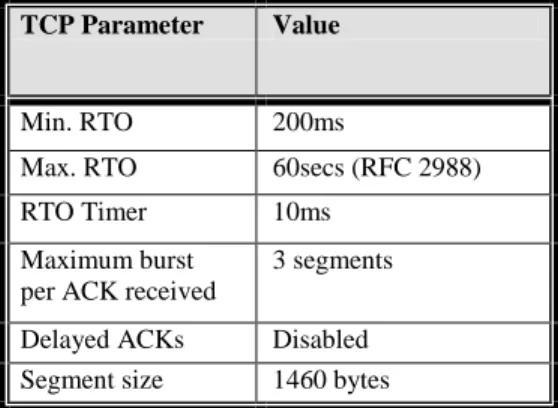
For the simulation runs, the SS_increase_thresh parameter is set to 4 and as such cwnd increases only every 5 ACKs, effectively limiting the increase rate to 1/5 of the original TCP algorithm. This adjustment is titled the slow start modification of TCP (SLOW START TCP). Common TCP parameters are outlined in Table 2.1.International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 12, December 2014)
90
TABLE 2.1:
COMMON TCPOUTLINED PARAMETERS
TCP Parameter Value
Min. RTO 200ms
Max. RTO 60secs (RFC 2988)
RTO Timer 10ms
Maximum burst per ACK received
3 segments
Delayed ACKs Disabled Segment size 1460 bytes
Algorithm 1 Slow start cwnd increase
Require: SS_increase thresh is the number of ACKs between increases, SS_increase is initialized to 0
if SS_increase = 0 then cwnd = cwnd + 1
SS_increase = SS_increase + 1
elseif SS_increase = SS_increase_ thresh then SS_increase= 0
else SS_increase = SS_increase + 1 end if
end if
The routing protocol may, further, include a packet caching mechanism in the event of packet loss due to mobility.
2.2 Congestion avoidance modification (SCA TCP)
The congestion avoidance mechanism of TCP determines a linear increase in the cwnd size per roundtrip time (RTT) as each ACK received acknowledging new data increases cwnd by 1. A delay is required to slow down sending rate during the congestion avoidance phase. A modified algorithm will be introduced for congestion avoidance. The behavior of this modified congestion phase is dictated by the value of the K_increase_ thresh variable, which specifies the level of delay added to the sending rate increase. Specifically, cwnd increases by a full segment's worth every K_increase_ thresh +1 of RTTs.
To evaluate the scope of improvement offered by these changes, we have conducted experiments on string topologies by replicating the simulation setup in the previous section. The K_increase_ thresh parameter was set to 4, which in turn implies that the cwnd would grow only every 5 RTTs.
Algorithm2:
Congestion avoidance cwnd increase
Require: K_increase_ thresh is the no. of ACKs between increases; K_increase is initialized to 0
if K_increase = 0 then cwnd = cwnd + 1/cwnd K_increase = K_increase + 1
Else if K_increase = K_increase _thresh then K_increase= 0
Else K_increase = K_increase + 1 end if
end if
III. SIMULATION MODEL AND RESULTS
Figure 3.1Explains An Example Of Simulation Models That Was Tested
Figure 3.1 A Simulation model
Results from simulations for both default and proposed TCP Protocol versus number of nodes are recorded and graphed as
A comparison between the throughput for default TCP and modified TCP will be explained as results of simulations.
1
0
2
3
4
6
5
7
9
8
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 12, December 2014)
91
TABLE 3.1
DEFAULT THROUGHPUT VS THROUGHPUT AFTER SLOW START MODIFICATION
Throughput has increased for each node numbers in graph. The improvement in throughput varied with number of nodes as shown in Fig 3.2. The maximum improvement achieved when number of nodes was 7. The improvement in throughput will be uniform and nearly constant when number of nodes reaches 11 node. So, the proposed achieved improvement when number of nodes reaches 7 and then begin in decreasing gradually till the increase reached nearly constant value when. The increase also depends on no of nodes and reaches the maximum when number of nodes number of nodes reaches 11 node. So, the proposed modified TCP achieved an improve in the behavior of default TCP after Congestion avoidance modification.
slow start modification
0 2 4 6 8 10 12 14 16 5 6 7 8 9 10 11 12 No of Nodes T h ro u g h p u t K B p S Default TCP Slow Start Mod
Figure 3.2 Default throughput VS throughput after slow start modification
TABLE 3.2
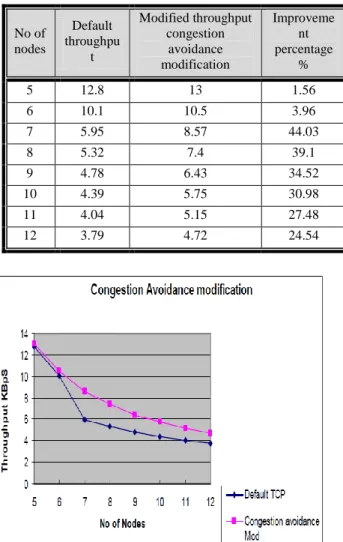
DEFAULT THROUGHPUT VS THROUGHPUT AFTER CONGESTION AVOIDANCE MODIFICATION
Figure 3.3: Default throughput VS throughput after congestion avoidance modification
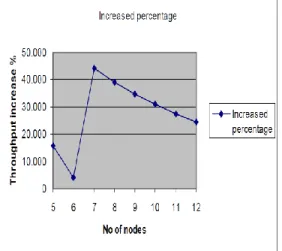
Fig 3.3 shows the increase in throughput as a result of the proposed modification in the default TCP. Fig 3.4 shows the increase ratio versus number of nodes.
No of nodes Default throughput Modified throughput (Slow start modification) Improve ment percentag e % 5 12.8 13.4 4.69 6 10.1 10.7 5.94 7 5.95 9.03 51.77 8 5.32 7.58 42.48 9 4.78 6.6 38.08 10 4.39 5.89 34.17 11 4.04 5.37 32.92 12 3.79 4.84 27.71 No of nodes Default throughpu t Modified throughput congestion avoidance modification Improveme nt percentage % 5 12.8 13 1.56 6 10.1 10.5 3.96 7 5.95 8.57 44.03 8 5.32 7.4 39.1 9 4.78 6.43 34.52 10 4.39 5.75 30.98 11 4.04 5.15 27.48 12 3.79 4.72 24.54
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 12, December 2014)
92
Figure 3.4 Increased throughput percentage after congestion avoidance modification
TCP enhancement using Optimal Window 3
-Optimal window size is a function of the number of hops between the source and destination nodes
Due to the hidden terminal problem, it is derived that there should be only one packet in transit every 4 hops for optimal TCP throughput
W opt = h /(4n)
Using Morris’ formula that links the overall loss rate and the TCP window size and considering the overall loss rate as an equivalent of marking probability. Then we substitute all the previous calculated/estimated values to come up with
However, this is the overall marking probability, NOT per-node. We distribute the overall marking probability uniformly along all nodes.
For Wireless Multi-hop Chain Network h-hop network, we need h+1 nodes (n0 to nh).All TCP flows go from n0 to nh. Fig 5.8 is a model of h+1 node.
The equation that model throughput in TCP [19]
Where r is the transmit rate in bytes/second; s is the packet size in bytes; R is the round-trip time in seconds; p is the loss event rate and assuming there is no delayed acknowledges ( b=1)
Applying the previous formula using optimal window size and compare with the throughput resulting without using optimal window as in the following equation
W = h /n 0.0048 0.005 0.0052 0.0054 0.0056 0.0058 0.006 0.0062 5 6 7 8 9 10 11 12 Number of nodes Th r ou gh pu t default modified
Figure 3.5 Default throughput (without using optimal window) VS after using optimal window
0 2 4 6 8 10 12 14 16 5 6 7 8 9 10 11 12 number of nodes im p ro v e m e n t p e rc e n ta g e i n th ro u g h p u t %
Figure 3.6: Increased throughput percentage after using optimal window
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 12, December 2014)
93
IV. CONCLUSIONS
In this paper two proposed modifications of TCP were presented in order to enhance TCP throughput in MANETs. It has been shown that the throughput has increased for the new proposed TCP. Enhancement in behavior of TCP over ad-hoc wireless network will affect many applications especially in military fields.
Inspired by the conservative sending rate increase of TCP, and motivated by its compelling performance advantage over TCP variants, we have introduced a new mechanism which employs a more conservative sending rate increase and which alleviates some of the intra-flow spatial contention caused by traditional TCP agents. To this effect, the new method employs parameterized delay in the growth of the TCP congestion window, which is implementable in both the slow start and congestion avoidance phases of TCP.
REFERENCES
[1] C.S.R.PRABHU, A.PRATHAP REDDI “BLUETOOTH
TECHNOLOGY: AND ITS APPLICATIONS WITH JAVA AND J2ME” ISBN: 9788120324435,(2004).Ding, W. and Marchionini, G. 1997 A Study on Video Browsing Strategies. Technical Report. University of Maryland at College Park.
[2] http://www.researchgate.net/profile/Shaym_Gumaste/publication/23 6279819_Routing_Algorithm_An_Overview/links/004635178f589a 19e8000000 Tavel, P. 2007 Modeling and Simulation Design. AK Peters Ltd.
[3] Jean-Pierre Le Rouzic “IEEE 802.11ac: “An analysis of the standard ” ISBN :9781492338376,(2013).
[4] Subir Kumar Sarkar, T.G. Basavaraju, C. Puttamadappa “Ad Hoc Mobile Wireless Networks: Principles, Protocols, and Applications”ISBN:9781466514461, (2013).
[5] Marco Conti , Jon Crowcroft and Andrea Passarella "Multi-hop Ad hoc Networks
[6] https://www.novapublishers.com/catalog/product_info.php?products _id=5556
[7] Kevin R. Fall “ TCP/IP Illustrated” ISBN:978 0321336316,(2011). [8] Kevin R. Fall “TCP/IP Protocol Suite”
[9] http://www.shihada.com/F10-244/papers/tcpadhoc.pdf [10] Shttp://www.ipcsit.com/vol5/84-ICCCM2011-C045.pdf.
[11] H. Balakrishnan, V. Padmanabhan, S. Seshan, and R. Katz, “A comparison of mechanisms for improving TCP performance over wireless links,” IEEE Transactions on Networking, vol. 5, no. 6, pp. 756–769, Dec. 1997.
[12] A. V. Bakre and B.R. Badrinath, “Implementation and performance evaluation of indirect TCP,” IEEE Transactions on Networking, vol. 46, no. 3, pp. 260–278, Mar. 1997.
[13] H. Balakrishnan, S. Seshan, and R. Katz, “Improving reliable transport and handoff performance in cellular wireless networks,” ACM Wireless Networks, vol. 1, no. 4, pp. 469 481, Dec. 1995. [14] K. Brown and S. Singh, “M-TCP: TCP for mobile cellular
networks,” ACM SIGCOMM Computer Communication Review, vol. 27, no. 5, pp. 19–43, Oct. 1997.
[15] H. Balakrishnan, S. Seshan, and R. Katz, “Improving reliable transport and handoff performance in cellular wireless networks,” ACM Wireless Networks, vol. 1, no. 4, pp. 469 481, Dec. 1995. [16] R. Durst, G. Miller, and E. Travis, TCP extensions for space
communications,” in Proc. of ACM MOBICOM, Rye, NY, USA, June 2006.
[17] T. Henderson and R. Katz, “Transport protocols for Internet-compatible satellite networks,” IEEE JSAC, vol. 17, no. 2, pp. 345– 359, Feb. 1999.
[18] Liang Yu, Gang Zhou, “A New Transmission Control Protocol for Satellite Networks,” Int. J. Communications, Network and System Sciences, vol. 4, pp. 256–265, April. 2011.
[19] J. Padhye, V. Firoiu, D. Towsley, and J. Kurose. A simple Model and its Empirical Validation. In Proceedings of ACM SIGCOMM’98. Vancouver, Canada, September 1998.