On the performance of group key management protocols in MANETs
Full text
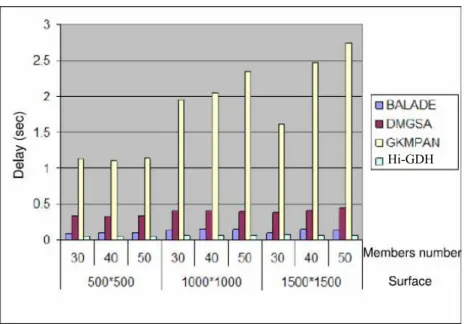
Figure



Related documents
Yaacob, A New Fifth Order Five-stage Runge-Kutta Method for Initial Value Type Problems in ODEs, Laporan Teknik Matematik M/LT No.. Yaacob, A Nonlinear Multistep Method for Second
of the Late Roman Fortification and belonged to the monument on the axis of the Stoa had at the left edge of its face an inscription consisting of one or two
In summary, the concepts of vocation and calling have many implications for the work of coaches, 385. applied sport psychologists, and career counsellors working with
Total Freight & Insurance Charges (4x5) Unit Erection Charges Total Erection Charges (4x7) Price Break-down for individual items for Tower Package (Package-A3). (Bidder
Tip for families: Like the Massachusetts Behavioral Health Partnership (see the section above on Public Health Insurance Programs), private insurance companies may also offer
Establishing rules are effective preventative strategies in class discipline control and management practices since they form a behavioral setting in class that entails what
Some countries are experiencing decreases in street crime where perpetrators need to
Input-dependent synaptic targeting of alpha(2)-subunit-containing GABA(A) receptors in synapses of hippocampal pyramidal cells of the rat. GABAB and CB1 cannabinoid

