Implementing the Robust Technique for Verifying the Neighbor Positions in MANET
Full text
Figure
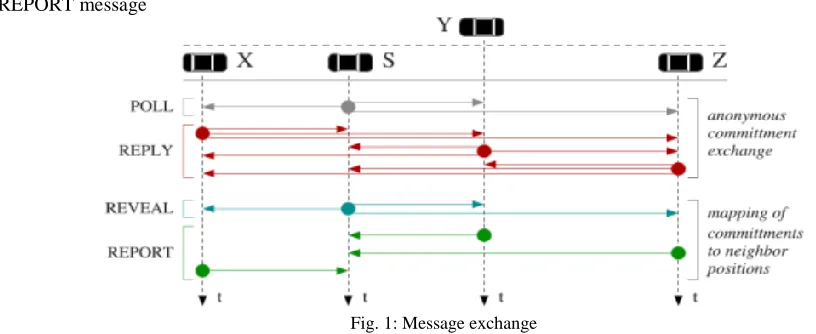
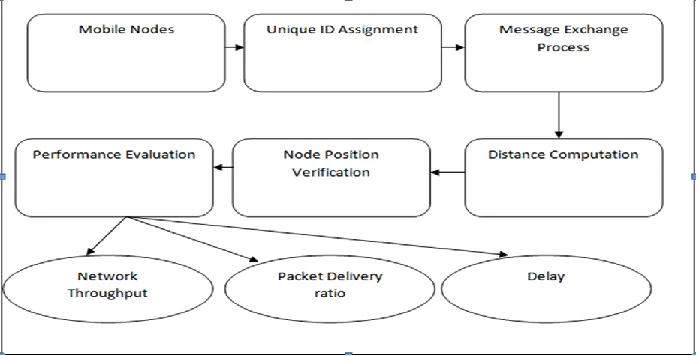
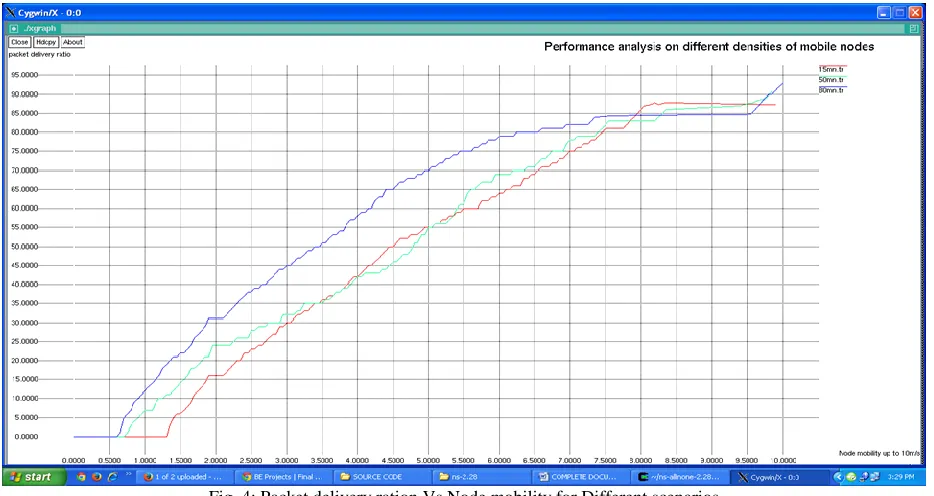
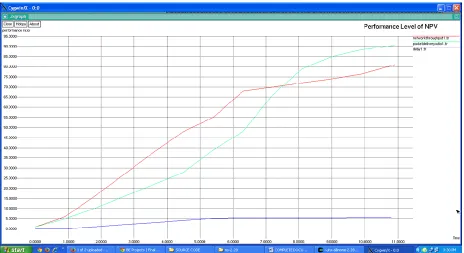
Related documents
Other readings (not required): Pearson, Neil D., 2002, Risk Budgeting: Portfolio Problem Solving With Value-at-Risk (New York: John Wiley & Sons), Chapters 11, 12, and 13;
This can confirm the supposition suggested before about the areas around the ball, enhanced also by Kim & Lee (2006) who found that elite goalkeepers, fixed their gaze on
6 Article 4: «States Parties condemn all propaganda and all organizations which are based on ideas or theories of superiority of one race or group of persons of one
Nevertheless, this work has clearly documented that natural selection for a clearly adaptive trait (copper tolerance) has caused a gene for post-zygotic isola- tion to spread
What types of information do the rice farmers need in Anyiin, Logo Local Government Area of Benue State, were do the rice farmers go to satisfy their information needs,
Furthermore, while symbolic execution systems often avoid reasoning precisely about symbolic memory accesses (e.g., access- ing a symbolic offset in an array), C OMMUTER ’s test
In the longer first period of 17 months (high salinity, low DIN/SRP), Cabras Lagoon was characterized by cyanobacteria of functional group Z.. This state abruptly changed