United States Air Force Defense Suppression Doctrine, 1968-1972
Full text
Figure
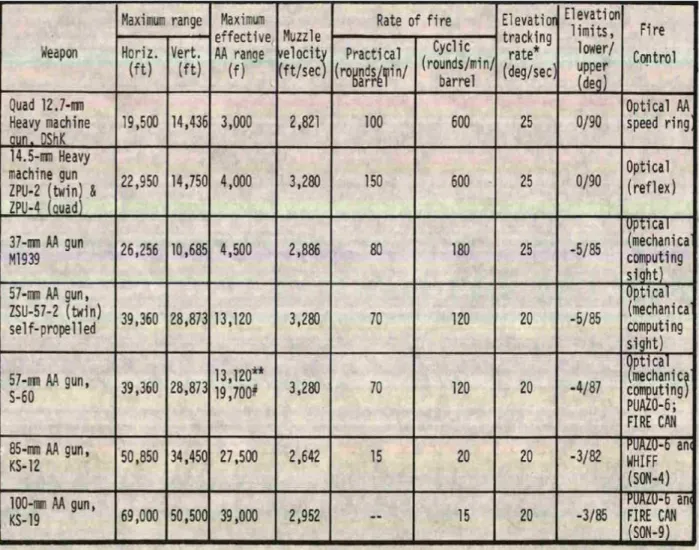



Related documents
During the last decade there have been proposals from development agencies and others to address small-scale (including artisinal) mining as part of the
active shunt filter, which is most widely used to eliminate current harmonics, reactive power compensation (also known as STATCOM, and balancing unbalanced currents.. It is
Chapter 1: Operating the TI-84 Plus Silver Edition 24 Note: Regardless of which graphing mode is selected, the TI-84 Plus will sequentially graph all stat plots before it graphs
Netmagic currently hosts the application on a robust and reliable infrastructure with 99.99% availability, manages the infrastructure, provides back up services, and manages
The assumption of our study is if managers and employees are aware or convinced of the business value of social media for their organization, they are more motivated to use
Speeds of the VANET nodes are constant between 5m/s and 25 m/s in discr this proposed model, cluster creation time election time and cluster head switchin estimated and
Note: If you are using FileMaker Pro Advanced, you will be able to copy and paste the table definitions from FileMaker Pro into FmPro Migrator via the Clipboard. FmPro Migrator
This procedure can be used directly to “tag” individuals on short time inter- val in the test video sequence. Figure 6 shows a selected set of atypical behavior, according to





