Social Graph Based Suspicious Chat Log Identification Using Apriori Algorithm and Support Vector Machine
Full text
Figure
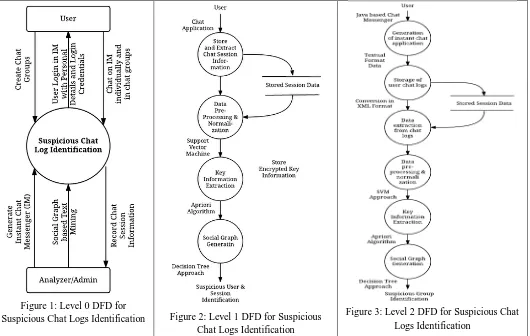
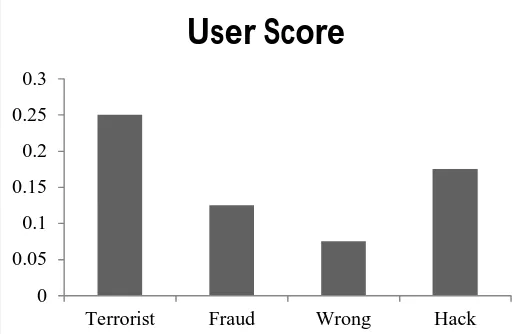
Related documents
We will be using Blackboard Collaborate Web Conferencing for Chat. This is an audio, video, and text-based Chat tool. I will be using all three features. To access the Chat
Two experiments were conducted to evaluate producer management decisions that may impact beef cattle reproductive efficiency. The over-arching hypothesis was that critical breeding
How can the principles of restorative justice be applied in the primary school setting to enhance relationships and facilitate deeper personalized
– Adopt policies that imply resource requirements consistent with the available national means;.. – Develop well structured public private
She is afraid to tell Lonnie since he might think she is a freak, but Lonnie assures her that he doesn’t feel this
Regional sales managers and business development managers in Asia Pacific are in high demand, targeted by global OEM’s to drive new business by capitalising on the development of
From this preliminary analysis cross-walking from N-SSATS data to key elements for quality adolescent substance abuse treatment facilities, significant adolescent volume substance
If an I/O expansion option is installed on any blade server, switch modules for that network interface must be installed in I/O module bays 3 or 4 on the MAXDATA PLATINUM