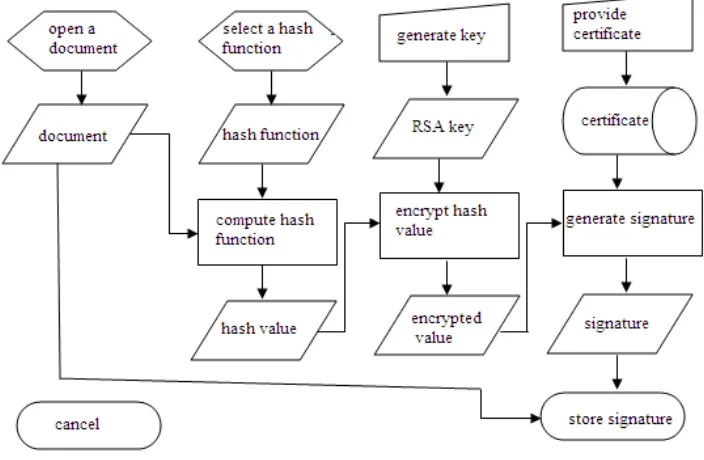
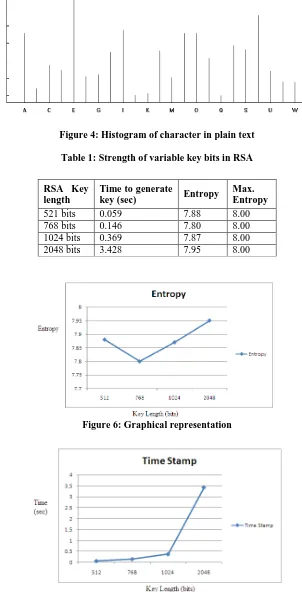
II. ATTACKS ON AUTHENTICATION
Full text
Figure

Related documents
Statutory Auditors’ report prepared in accordance with article L.225-235 of the French Commercial Code (Code de commerce) on the report by the Chairman of the Board of Directors
John’s is a congregation of 1,200 members worshiping in the mother church of the Diocese of Florida.. It was founded as a mission parish in 1829, and the church’s first building
entrepreneurship education of being a vehicle for self-employment awareness creation and skills development among graduates; and develop a strategic framework for
We have modeled these characterizations in what we call a template representation of Pascal programming knowledge that interconnects multiple representations of problem
Although many studies assume that patients experience coercion negatively (Hiday et al., 1997, Lidz et al., 1995; Swartz et al., 2003), the results of Hiday et al.’s (1997)
The primary objective of this study is to achieve continued operation of any multi-terminal HVDC network using relatively slow dc circuit breakers (with minimum
Our experience, and that of colleagues in other firms representing personal injury victims, is that the judgment of the House of Lords in Summers is sound and that outright fraud
Regarding the features which in- creased after T cypionate administration, the use of Q Orbitrap revealed the presence of only one marker in each ionization