Software Protection with Code Mobility
Full text
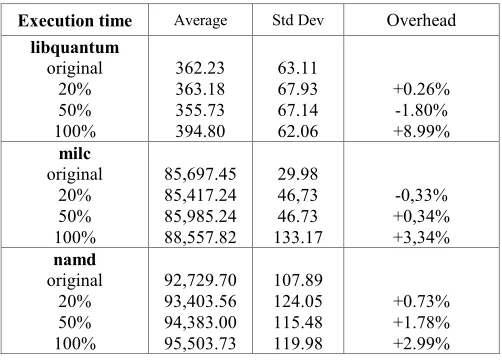
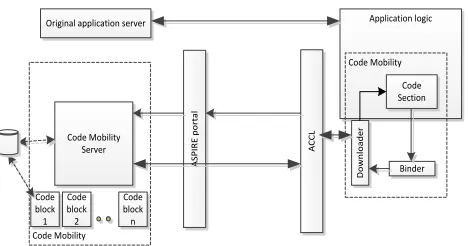
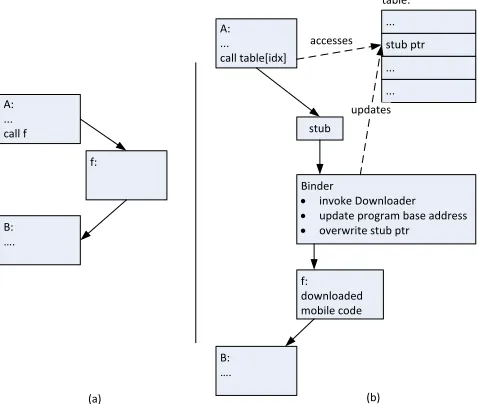
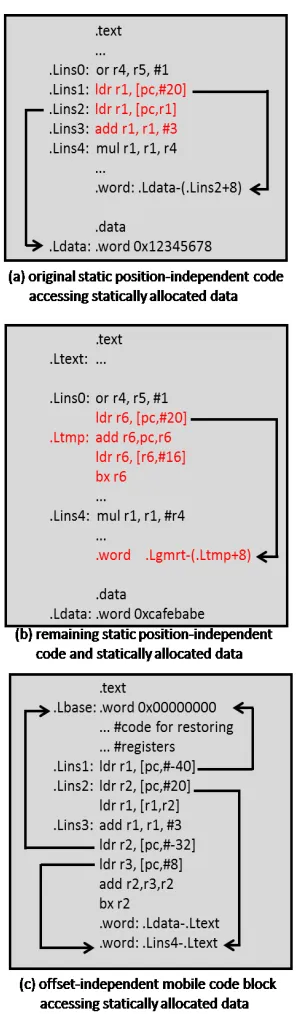
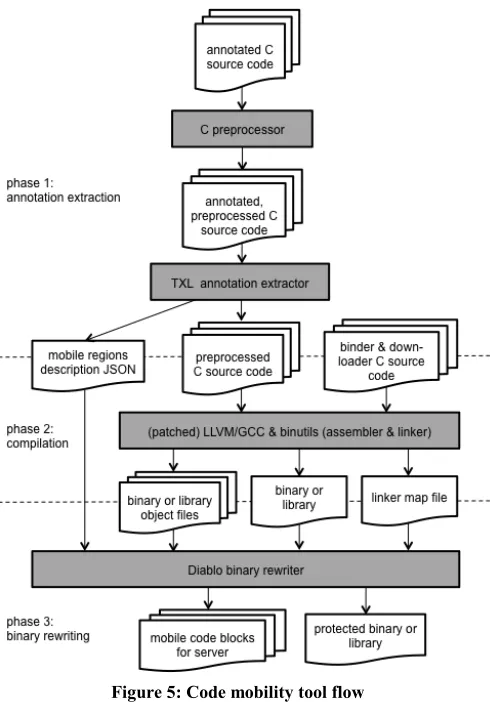
Figure
Related documents
Schwarzkopf et al., 2014 ). Moreover, we show that natural images with a combined wedge and ring aperture are well suited as mapping stimuli compared to more traditional stimuli.
In conclusion, this evidence-based review of the intersection between e-HRM and strategic HRM has led us to four primary findings in the literature: 1) implementation of
If your Bluff check result exceeds your target’s Sense Motive check result, the next melee attack you make against the target does not allow him to use his Dexterity bonus to defense
Then, to access the relevant information from the MEL, follow the steps given in the first example: Go to Section 01, and then, if necessary, Section 02 for operational
-- If (as the fable asserts) land reform in occupied Japan raised productivity, then the prefectures where the program transferred the largest fraction of land should have seen
Nevertheless, the classical phase-space components of the hybrid Bohmian trajectories identify a Hamiltonian flow parameterized by the quantum coordinate and this flow is associated
The learning model that can increase the critical thinking skills and increase the students’ independent learning skills especially for chemistry lesson is problem-based
The interviews revealed that PTs’ epistemological beliefs and beliefs about learning and teaching mathematics are largely in line with constructivist theory, and that their