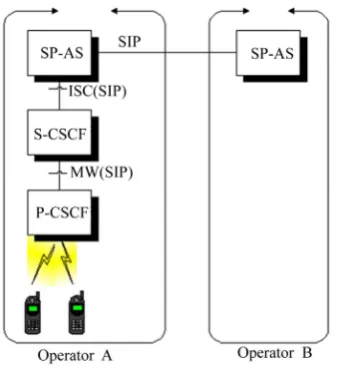
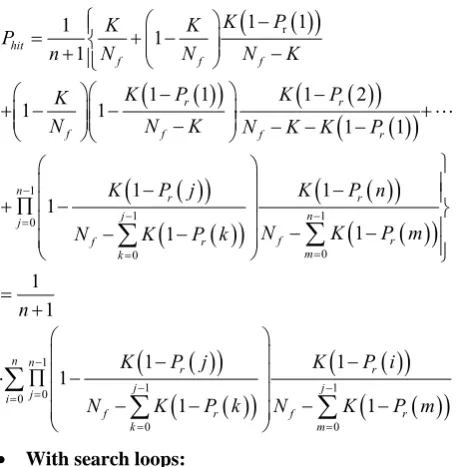
A Framework for Security Enhanced Peer to Peer Applications in Mobile Cellular Networks
Full text
Figure

Related documents
Theme setting: In this study, by describing the success model of implementing e-CRM, the relevance of variables like customer information quality, e-CRM
The relationship between seismicity and fault structure in zones A and B on DW (Figure 9) is strikingly simi- lar to what is observed on the western end of the G3 segment of the
Few studies have examined gender differences in psychological distress in relation to the iso-strain framework, although the general pattern of poorer mental health across
Instead, the data are carefully reviewed to understand the main features (e.g., center and spread) to determine what evidence this data might provide about the population.
In addition to weed species listed in the ANNUAL WEEDS and BIENNIAL and PERENNIAL WEEDS Application Rate and Timing tables, these treatments may be used to control or suppress
The average goods and services deficit decreased $2.1 billion to $43.1 billion for the three months ending in November.. Average exports of goods and services decreased $0.7
I have also actively participated in scope of practice discussions since 2004, resulting in my voicing of strong support for the scope review process as developed by the
For lecture recording and distribution, virtUOS applies four open-source solutions, virtPresenter (www.virtpresenter.org) for automatic lecture recording, the