Second Order Online Active Learning based
Malicious Web Classification
Miss Divyashree Kelji1, Dr. P. D. Lambhate 2 1
PG student, 2Associate Professor, Computer Department, JSPM’s JSCOE, Handewadi, Pune
Abstract:Active learning is an exceptional instance of semi-directed ML in which a training calculation can intuitively inquiry the client (or some other data source) to acquire the ideal yields at new information focuses. This is more testing than regular online learning undertakings since the student not just needs to figure out how to viably refresh the classifier yet additionally needs to choose when is the best time to query the mark of an approaching occurrence given restricted name spending plan. Login accreditations or record information by sending as an authentic component or individual in email or other correspondence channels which assailant endeavors to learn fragile information in a kind of blackmail called Phishing. To improve the execution of on-line learning classifiers, an upgraded on-line learning procedure is proposed. They potentially use URL data to choose whether the URL interfaces with poisonous pages. The versatile methodology, genuinely characteristic and compelling which can be handle by an epic structure of Cost Sensitive Online Active Learning (CSOAL) for vindictive identification.
Keywords: Second order on-line active learning, URL, Cost sensitive, phishing URL, Machine Learning.
I. INTRODUCTION
In this unique condition, active learning gives a larger number of advantages than in the stationary simple of the issue. The examination work was done on streamlining the execution of the Search Engine. With the objective of marking the most instructive occasions to accomplish high forecast accuracies with least cost, dynamic learning is a ceaselessly developing region in ML research. Here, this computation is altogether upgraded in speed and precision by displacing the working set assurance in the successive minimal streamlining steps. This system requires just straight time. They infer that second request working set determination end up the default in iterative SVM learning calculations. Pernicious Web locales are a foundation of Internet criminal exercises. The malignant URL issues are physically developed blacklists, just as customer side frameworks that dissect the substance or conduct of a Web website as it is visited. This system comprises a gathering of Web destinations & through the Internet clients access the global data of the system in World Wide Web. The program makes an interpretation of a URL into guidelines that is facilitating the site about how to find the server through a multi-step goals process. It is required an effective noxious page location frameworks to recognize a site page before client peruses it, and quit opening malevolent website page to keep away from assaults from pernicious site pages. Examinations are performed on the double and multi-class dataset utilizing the previously mentioned machine learning classifiers. In past examinations, keyword coordinating has dependably been utilized to distinguish malignant URLs, however this technique isn't versatile. Chi Zhang et al. [1] the data sharing plan in calculations is isolated into two sessions: perform various tasks' data is first shared inside every hub and afterward the entire system is pushed towards a typical minimizer by correspondence among various hubs. Empower learning numerous errands at the same time on a decentralized disseminated system. Justin Ma et al. [2] have been expansive interest for creating frameworks to keep the end client from visiting such things. They portray with this issue dependent on robotized URL characterization, utilizing factual strategies. For sure, the framework consequently chooses huge numbers of similar highlights recognized by space specialists as being run of the typical of "noxious" Web destinations. This learning-based way is the issue can succeed if the dispersion of highlight esteems for malevolent models is not the same as kindhearted precedents. W. Jialei et al. [3] proposed two cost-delicate online based learning calculations by specifically streamlining cost-sensitive estimates dependent on online inclination plunge procedures. Calculations perform great on a generally expansive parameter space of the learning rate. This promising outcome approves the upside of the proposed calculations for fathoming a true online inconsistency discovery errand which is regularly profoundly class-imbalanced.
II. RELATED WORK
A.C. Lozano et al. [4] proposed by applying the hypothesis of inclination boosting top-norm based Cost-sensitive boosting strategies for multi-class order. The hypothetical improvement gives a structure to translate an assortment of existing strategies for cost-sensitive learning and their variations. The proposed plan for the part accomplishes unrivaled outcomes as far as cost minimization and, with the utilization of higher request p-norm misfortune in specific cases.
R. Akbani et al. [5] the accomplishment of SVM is restricted when it is connected to the issue of gaining from imbalanced datasets in which negative cases intensely outnumber the positive occurrences. In seven out of the ten datasets SDC calculation has the most elevated g-implies metric, and in the staying three datasets it isn't bring down by much. The issue is that with imbalanced datasets, the educated limit is excessively near the positive examples. This implies SVM is unaffected by non-loud negative cases far from the limit.
S. Hanneke et al. [6] give a general portrayal of the extents of these upgrades as far as a novel speculation of the difference co-effective. It basically speaks to a refinement of Meta-Algorithm 0 to take more prominent favorable position of the consecutive part of dynamic learning. The instinctive explanation behind this is, as the quantity of name demands expands, the distance across of the form space shrivels at an anticipated rate. The system to take more prominent preferred standpoint of the consecutive idea of dynamic learning.
N. Cesa-Bianchi et al. [7] portray an augmentation of the established Perceptron calculation, called second-request Perceptron, and dissect its execution inside the oversight bound model of on-line learning. The prescient execution in the examinations has been assessed utilizing the standard test mistake measure. They create two variations of the calculation and demonstrate comparing mistake limits. The main variation is a versatile parameter adaptation, while the second variation kills parameter "a" and replaces standard lattice reversal with pseudo-reversal.
B. Wang et al. [8] propose a boosting-based structure for online exchange and perform various tasks learning. It center fundamentally on the single source exchange case, anyway the various source exchange learning calculation can be determined likewise. The objective of their work is to give sound expansions to existing exchange and perform multiple tasks learning calculations with the end goal that they can be utilized a whenever setting. It applies the proposed calculation to a standard seat mark just as to a mind boggling seizure recognition assignment.
J. Wan et al. [9] explore another system of figuring out how to rank for CBIR, which intends to look for the ideal mix of various recoveries, conspires by gaining from huge scale preparing information in CBIR. At last, the internet figuring out how to rank calculations is commonly more effective than the group calculation. The proposed on-line based figuring out how to rank depends on straight models and is therefore more versatile than the part based comparability learning approaches. It is hence very wanted to join various sorts of assorted element portrayals and various types of separation measures so as to enhance the recovery exactness of a genuine world CBIR assignment.
Jing Lu et al. [10] present Passive-Aggressive Active learning calculations which are another group of online dynamic learning calculations. Nonetheless, if the example is effectively ordered by the gained genuine name, this preparation case will be disposed of and never be utilized to refresh the student as indicated by the standard of the Perceptron calculation. At last, see that the proposed CSPAA calculation accomplishes the best affectability execution, yet in addition accomplishes genuinely great explicitness execution which is commonly very practically identical to alternate calculations.
S. C. H. Hoi et al. [11] proposed LIBOL is a simple to-utilize open-source bundle for web based learning innovative work. We would like to make LIBOL a helpful AI apparatus, yet additionally a perfect research stage for directing online learning research. In view of the consequence of the misfortune, the student at last chooses when and how to refresh the grouping model toward the finish of each learning venture. The objective of our work is to execute a vast group of assorted web based learning strategies in writing to encourage innovative work of web based learning methods to certifiable applications. In light of the aftereffect of the misfortune, the student at last chooses when and how to refresh the characterization model toward the finish of each learning venture.
III. PROPOSED ALGORITHM A. Description of the Proposed Algorithm
1) Load Dataset: This module, a client loads URL Dataset. The machine learning has discovered colossal achievement where principle center essentially around the static examination strategies. Dynamic investigation strategies incorporate observing the conduct of the frameworks which are potential exploited people, to search for any abnormality. We treat URL notoriety as a binary grouping issue where positive precedents are noxious URLs and negative models are amiable URLs. Likewise adjust all the more rapidly to new highlights in the ceaselessly developing circulation of pernicious URLs. From these highlights and labels, we can prepare an online classifier that distinguishes vindictive Website with most elevated precision over a reasonable dataset.
2) Feature Extraction: The following stage is to extricate useful highlights with the end goal that they adequately portray the URL after the arrangement information is gathered and in the meantime, they can be interpreted numerically by ML models. We develop the element vector for every URL continuously. At the point when our component gathering server gets a URL, it endeavors to question a few outer servers to build the host-based bit of the element vector. Each time that a noxious site is found you simply add it to the rundown. When you run over another connection, simply check to ensure that it doesn't show up on that rundown. Interruption Detection Systems can check the website pages for such signatures, and raise a banner if some suspicious conduct is found.
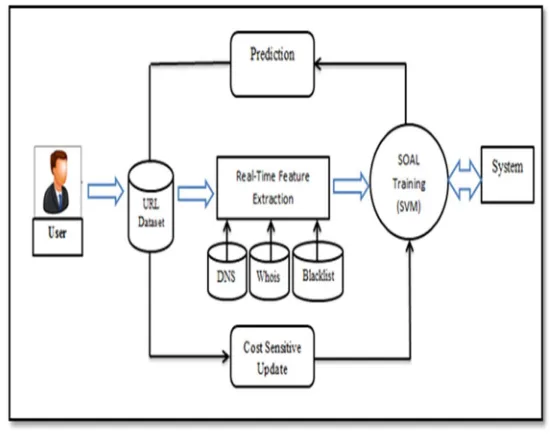
[image:3.612.176.451.398.621.2]3) Improved Cost Sensitive Second Order Online Active Learning: This module applies Cost Sensitive Second Order On-line Active Learning training calculation for highlight separated URL dataset. Online dynamic learning has been effectively investigated and connected to determine the pernicious URL Detection undertakings. On-line dynamic learning calculations generally into two noteworthy classes: (I) First-request online dynamic learning calculation, and (ii) Second-request online dynamic learning calculation. For instance, they as a rule accept the load vector w pursues a Gaussian circulation w N˜ (u, E) with mean vector is having a place into Rd and co difference grid E is having a place into Rdxd. This is especially valuable for malignant URL Detection where information is scanty and high dimensional. To enhance the execution, naturally rearrange the parameters learning rate, regularization and smoothing for accomplishing great outcome.
Fig. 1 Proposed System
Algorithm 1: Improved Cost Sensitive Second Order Online Active Learning
INPUT: penalty parameter C, bias parameter, Smoothing parameter sm, Regularization r and Learning rate lr.
INITIALIZATION: w1 = 0
for t = 1, . . . , T do
Receive an incoming instance xt $=$ Rd;
Predict label ˆyt = sign (pt), where
pt = wt · xt; draw a Bernoulli random variable
Zt = {0, 1} of parameter delta / (delta + |pt|);
if Zt :1 {
sm, r, lr : Random population based iterative algorithm then query label
yt : {−1,+1};suffer loss lt (wt) : l(wt; (xt, yt)); wt+1 : wt + Ttytxt,
where Tt : min{C, lt(wt)}; }
else
wt+1 : wt + Ttytxt, where Tt : 0; end if
end for
IV. PSEUDOCODE A. Malicious URL Detection Method
Step 1) Initialization
1) Step 2) URL dataset
2) Step 3) Select instance
3) Step 4) Extract Feature
4) Step 5) CSOAL Training
5) Step 6) CSOAL Testing
6) Step 7) Optimization
7) Step 8) Classify URL
8) Step 9) Prediction
9) Step 10) Final result
10) Step 11) End
V. ALGORITHM
VI. SIMULATIONRESULTS
(a) (b)
Fig. 2 Performance measure. (a) Accuracy graph of SOAL, SOALcs & Improved SOALcs. (b) Cost graph of SOAL, SOALcs & Improved SOALcs.
VII. CONCLUSIONANDFUTUREWORK
Here, we center on a reciprocal procedure, lightweight ongoing order of the URL itself to foresee whether the related site is noxious. In this way, each time a client chooses whether to tap on a new URL they should verifiably assess the related hazard. This work introduces such a methodology and gives some understanding into utilizing machine movement information to foresee noxious conduct close to collaborating with a URL. Notwithstanding, URL arrangement is a testing errand in light of the fact that new highlights are presented day by day — thusly, the dissemination of highlights that describe pernicious URLs advances continuously. In existing work, the incentive for the parameters learning rate, regularization and smoothing are settled one. To enhance the execution, naturally correct these parameters for accomplishing great outcome. Increment precision and diminish cost for the malevolent informational index dependent on modifying the hyper parameter utilizing enhancement system. Thusly, the occasions chose for CSOAL naming in our proposed calculation are more instructive than those of the current calculations. Portrayal learning in future through profound learning approaches. In future work will incorporate progressively successful online learning and other developing difficulties.
REFERENCES
[1] C. Zhang, P. Zhao, S. Hao, and S. Hoi, “Distributed multi-task classification: A decentralized online learning approach,” Machine Learning, 2017.
[2] J. Ma, L. K. Saul, S. Savage, and G. M. Voelker, “Beyond blacklists: learning to detect malicious web sites from suspicious urls,” international conference on Knowledge discovery and data mining, pp. 1245–1254, ACM, 2009.
[3] W. Jialei, Z. Peilin, and S. Hoi, “Cost-sensitive online classification,” IEEE Transactions On Knowledge And Data Engineering, vol. 26, no. 10, pp. 2425– 2438, 2015.
[4] A. C. Lozano and N. Abe, “Multi-class cost-sensitive boosting with p-norm loss functions,” in Proceedings of the 14th ACM SIGKDD international conference on Knowledge discovery and data mining, pp. 506–514,ACM, 2008.
[5] R. Akbani, S. Kwek, and N. Japkowicz, “Applying support vector machines to imbalanced datasets,” in European conference on machine learning, pp. 39–50, Springer, 2004.
[6] S. Hanneke, “Activized learning: Transforming passive to active with improved label complexity*,” Journal of Machine Learning Research, vol. 13, pp. 1469– 1587, 2012.
[7] N. Cesa-Bianchi, A. Conconi, and C. Gentile, “A second-order perceptron algorithm,” SIAM Journal on Computing, vol. 34, pp. 640–668, Jan.2005.
[8] B. Wang and J. Pineau, “Online boosting algorithms for anytime transfer and multitask learning,” in Twenty-Ninth AAAI Conference on Artificial Intelligence, 2015.
[9] J. Wan, P. Wu, S. C. H. Hoi, P. Zhao, X. Gao, D. Wang, Y. Zhang, and J. Li, “Online learning to rank for content-based image retrieval,” in Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence, IJCAI 2015, Buenos Aires, Argentina, July 2015.
[10] J. Lu, Z. Peilin, and C. S. Hoi, “Online passive aggressive active learning and its applications,” Machine Learning, vol. 103(2), pp. 141–183, 2016.
[11] S. C. H. Hoi, Jialei Wang and Peilin Zhao, “LIBOL: A Library for Online Learning Algorithms,” Research Collection School of Information Systems in 2014. [12] F. Vanhoenshoven, G. N ́apoles and R. Falcon, “Detecting Malicious URLs using Machine Learning Techniques,” IEEE Symposium Series on Computational