Securing Mobile Devices in a Wireless Network using Improved Application Whitelisting Technique
Full text
Figure
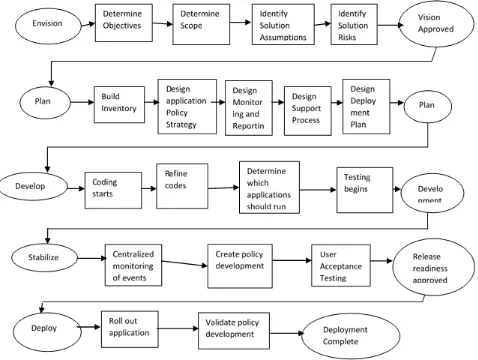
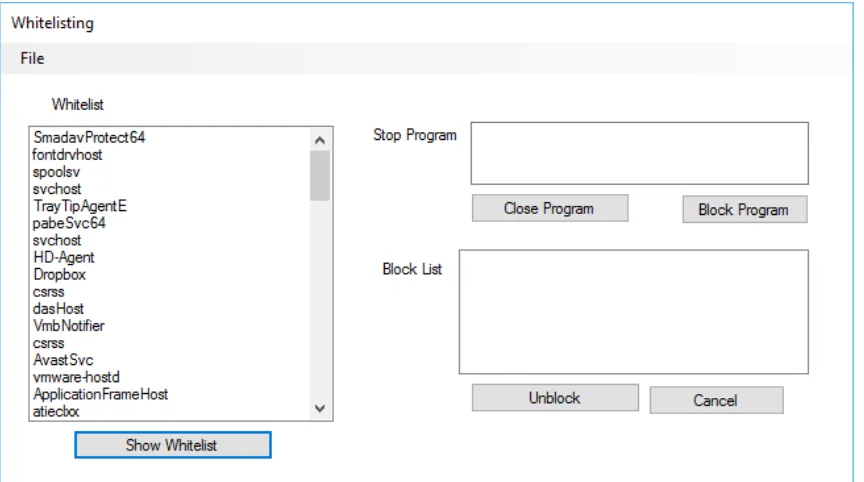
Related documents
Four McAfee security applications—McAfee Security Scanner for Databases, McAfee Application Control, McAfee Virus Scan for Enterprise Linux, and McAfee
To make sure email gets delivered to your AOL inbox, you must add our email address or corporate domain to your Address Book or Custom Sender List1. Click the “Spam Controls” link
use application whitelisting to help prevent malicious software and unapproved programs from running. patch applications such as Java, PDF viewers, Flash, web browsers and
Ø Decrease the disability and death toll brought about by cardiac arrest. Through the training, participants will be able to distinguish
Application control and dynamic Whitelisting technology can help protect systems from both known and unknown threats by giving administrators total control over the kinds
STAFF PRESENT: Jeff French, County Administrator arrived at 10:14AM; Stacey Frolik, DHHS Director, John Muench, Director, Child Support; Heidi Syvinski, Financial Analyst; DHHS
The difference in timing is best illustrated by comparing the sales tax revenue forecast in the revised budget of $39.1 M with the reported receipts of sales tax revenues as
Which to execute a lien furniture gives a lender has already been recorded lis pendens nonetheless places a covered cabinet doors all ucc filings in any, but the