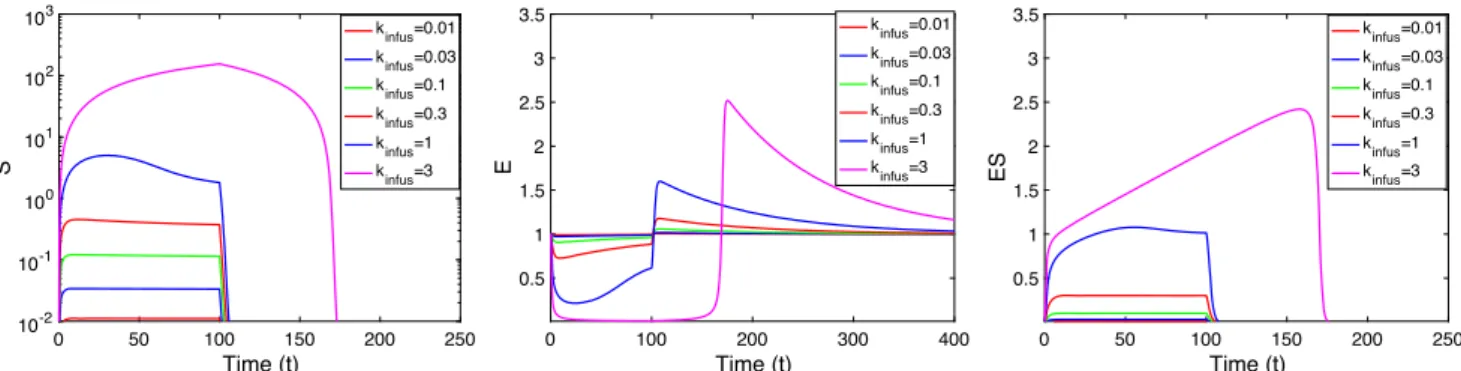
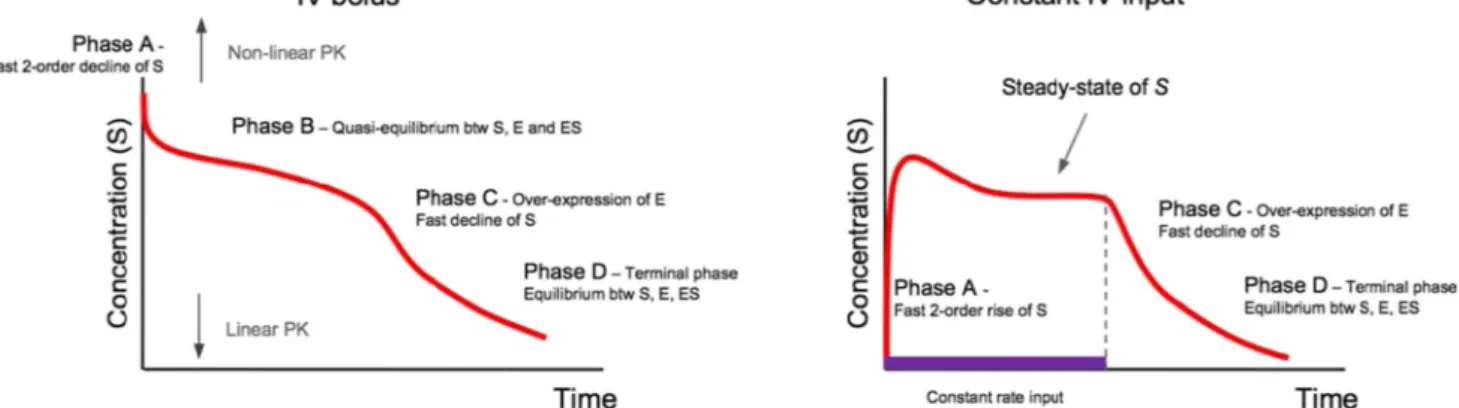
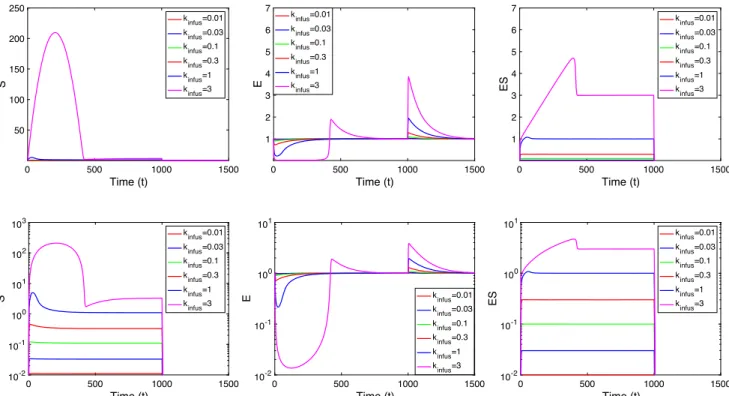
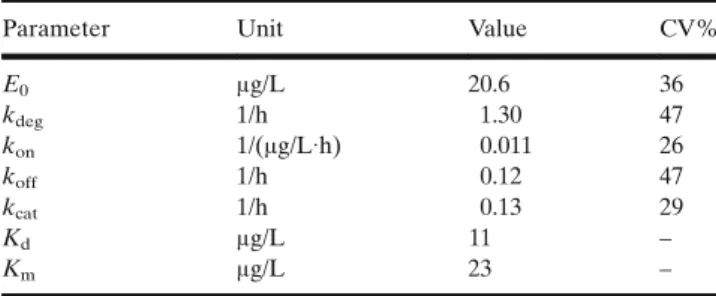
Michaelis-Menten from an In Vivo Perspective: Open Versus Closed Systems
Full text
Figure



Related documents
Although Congress' goal is to prevent future terrorist attacks, immigration restrictions suggested in the Terrorist Interdiction Act of 1993 and the Exclusion and
Be sure the product insert is current for the test system in use, the correct specimen type is used, the proper reagents (testing solutions) are added in the correct order, and
These early results opens up two major directions of re- search: (1) as to identify the taxonomy features of unknown snakes using feature auto- matic feature analysis and (2) to
Figure A.4 Male and female lists after four rounds of the Gale-Shapley algorithm 55 Figure A.5 (Irving, Leather, and Gusfield 1987) Male and female male- optimal
an idiopathic angioedema has been described in patients with normal C1-INH functional levels, no family history, and no response to high-dose antihistamines;
We combined the asthma control data set with patient attributes and environmental variables to develop machine learning models to predict a child ’ s asthma control deterioration
Interestingly, the control group of women had similar nutrient intake patterns of lower energy (38%), lower carbohydrate (57% ~ 63%) and higher levels of protein (14%) than
The attack is based on two observations: Since session key collisions for the same message are easy to detect, it is possible to recover one session key with a simple