S7-400H SIMATIC. Fault-tolerant systems S7-400H. Preface 1 Fault-tolerant automation systems. S7-400H setup options 3.
Full text
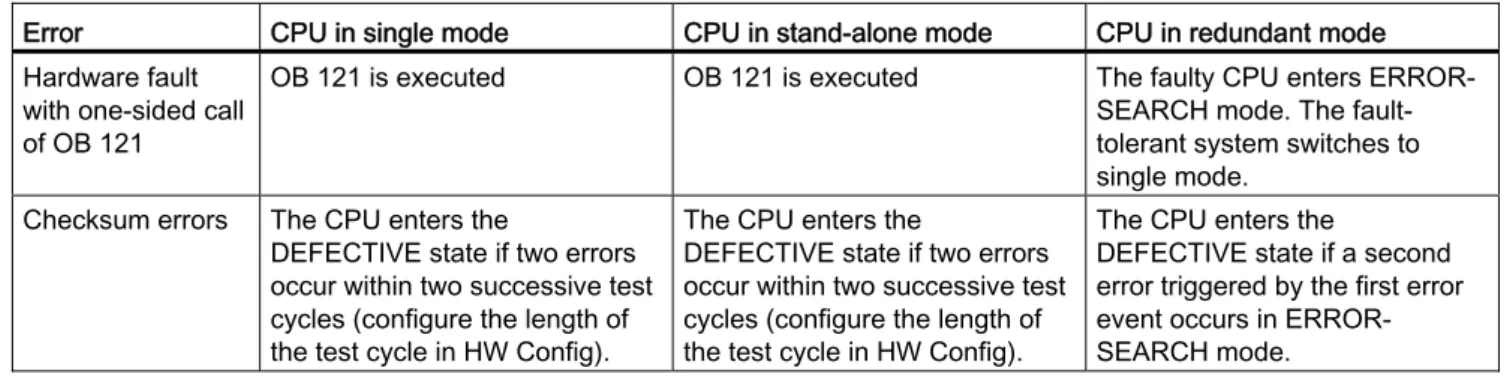
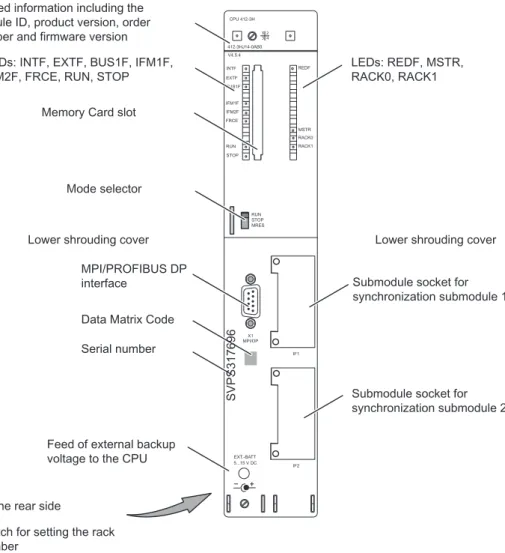
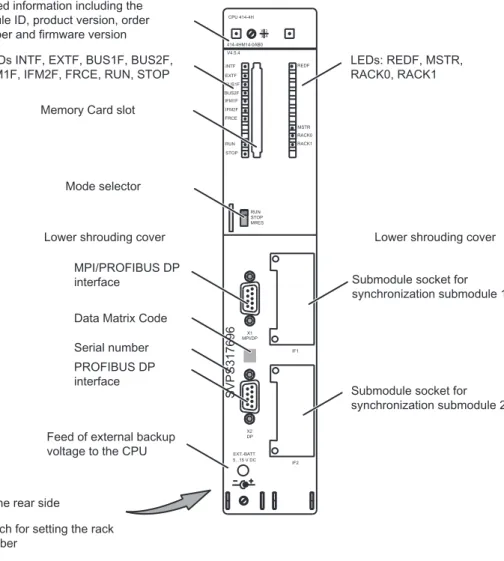
Figure


Related documents
In summary, the coupling from the orthogonal modes to superposed modes in a highly birefringent suspended-core fiber by an acoustically modulated Bragg grating in combination with
¢ Once you have obtained a visa, you may not enter the United States more than 30 days before the program start date listed on your SEVIS Form I-20.. The
Our constructive Steiner network heuristic method considers the double-sided timing constraints, adopts dynamic programming to construct the non-tree solution, and uses greedy
A common approach to the Repeater Tree Problem is to divide it into two steps, Steiner tree generation (also called topology generation) and repeater insertion (also called
Si se lleva a cabo un análisis de los sujetos escolarizados en un centro con Alto Grado de Inclusión, se puede apreciar como existen diferencias significativas tanto en diferentes
Hoy hay que decir, además, que la comunidad internacional ha otorgado el carácter de derecho a esta aspiración a una educación más inclusiva para todos los
In this work, we investigate the initial interaction of water and oxygen with different surface reconstructions of GaP(100) applying photoelectron spectroscopy, low-energy
For example, from 23 lines of YAML code comprising 92 tokens, cascading verification syn- thesizes 104 lines of PRISM code comprising 744 tokens and three behavioral properties