Transmission line modelling for multi-gigabit serial interfaces
Full text
Figure
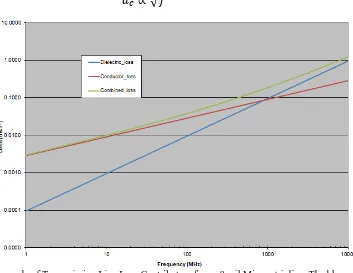
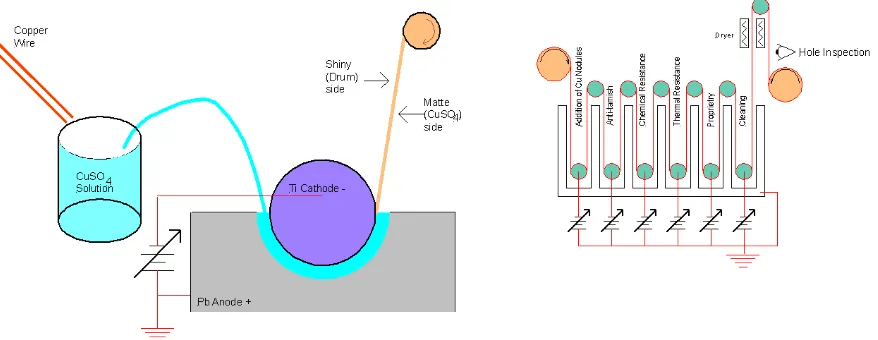
Related documents
Problematic Internet use, health anxiety aroused by online searches for health information and escalation of health concerns as an indicator of cyberchondria, are all associated
We examine the quantile serial dependence in crude oil prices based on the Linton and Whang's (2007) quantile-based portmanteau test which we improved by means of quantile
International Trade Regulation: General Frost Brown Todd’s International Trade Regulation Service Team offers experienced counsel and legal services to Clients whose
The lowest energy structures of the pyridine and pyrimidine rad- ical cation clusters containing 3-4 HCN molecules show a strong tendency for the internal solvation of the
This study examined the effects of increased metabolic heat production during thirty minutes of physical work until the test subject’s body core temperature reached 38.5
The third example shows how cold atoms in optical lattices offer a possible way to implement interacting many-body open quantum
Optimal local and central forest management responds to the MPB outbreak in cell according to the harvest rule for which is a function of the 4 × 36 = 144
In this work we presented UserLoop, a security extension to the Android OS that takes advantage of contextual information in order to block permissions requested when the user is not

![Figure 8 The Two Surface Roughness Models Proposed by [Samuel P. Morgan, 1949]: One Rectangular drawn on the left hand side and the Other Triangular drawn on the right hand side](https://thumb-us.123doks.com/thumbv2/123dok_us/185991.2012550/8.595.78.528.286.403/figure-surface-roughness-proposed-samuel-morgan-rectangular-triangular.webp)
![Figure 9 Measurements of Surface Roughness Made by Optical Profilometers with Approximate Dimensions [Hall, Heck, 2009]](https://thumb-us.123doks.com/thumbv2/123dok_us/185991.2012550/9.595.243.364.351.504/figure-measurements-surface-roughness-optical-profilometers-approximate-dimensions.webp)
![Figure 11 Huray [Huray, 2010] Observed That SEM Photographs of Surface Roughness Looked Like Stacked Smowballs](https://thumb-us.123doks.com/thumbv2/123dok_us/185991.2012550/10.595.79.521.263.435/figure-observed-photographs-surface-roughness-looked-stacked-smowballs.webp)