Adaptive Security of Constrained PRFs
Full text
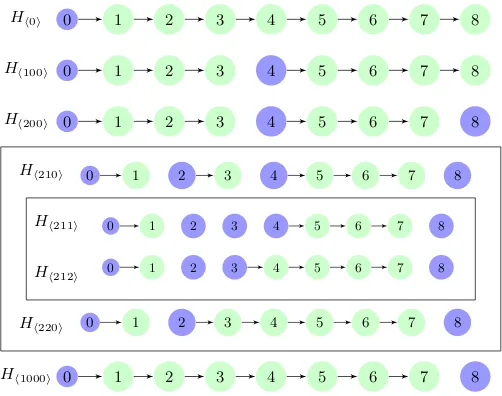
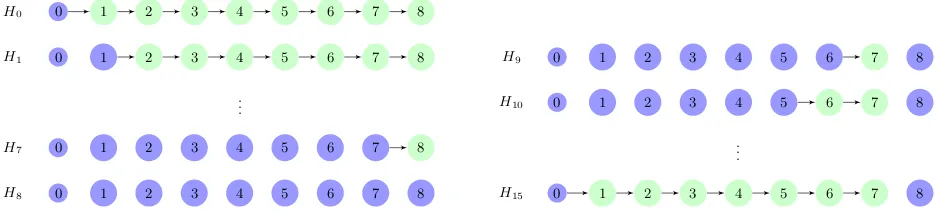
Figure


Related documents
Indeed, we found a strong reduction of mTOR protein expression 18h after activation when miR-99a was overexpressed compared to control virus or miR-10b infected cells
In the following, we show the security of (s)OAKE-HDR (resp., rOAKE-HDR), with off-line pre- computed DH-exponents, DH-components, and the values A yc or B xd (resp., only
Results show that the improved second-order sliding mode controller is based on the PID direct suspension force control strategy, which further enhances the robustness of the
are different in physiognomic features. For regions of intensive economic development, to which the Ferghana Valley belongs, the use of physiognomic elements of the
amount of data packets regardless of delivery rate from DSR but in all cases of nodes speed, protocols DSDV and DSR always perform better at low speed of nodes; When movement speed
Recently, a comparative study between the bioMe´rieux and Dade-Behring assays, with a panel of well-characterized sera from recent or past HCMV infection, showed that the
In this paper, proposed method is based on naive bayes classifier to detect covert channels in TCP ISN and IP ID fields of TCP/IP packets..
