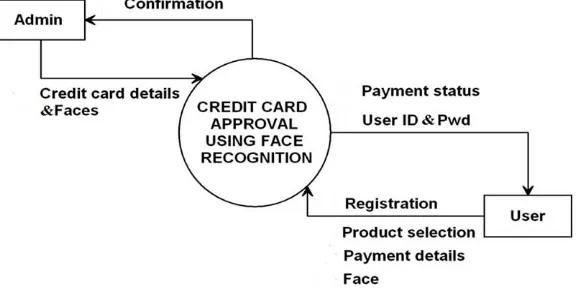
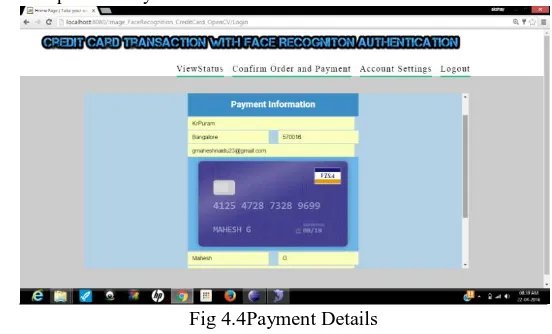
Credit Card Transaction Using Face Recognition Authentication
Full text
Figure


Related documents
In the Natural Log Templates, on the line immediately before the start of a spot break, you need to enter an event (at the approximate spot break start time) and use event
miRNA-lin-4 以来,miRNA 就成为生物信息学的一个重要研究方向。而 miRBase 序列数据库(网址为:http://www.mirbase.org)作为存储 miRNA
Basic details plus any additional text are included in the monthly training calendar included in CJS Weekly and CJS Professional two months prior to start date, eg January
Besides the additional custom tools available, local pass- word managers also have the additional benefit of allowing their users the options of exporting their database of passwords
Research data were obtained from the calculation of scores DIT-1 test. This study aims to examine the level or moral stage of students using story of material moral dilemmas. Based
Based on prior tests of model constructs across cultural and developmental lines (Anderson & Minke, 2007; Deslandes & Bertrand, 2005; Green et al., 2007), we hypothesized
Research Methods CRP 513 - 4 units Architectural Structures ArcE 522 - 3 units Arch Design - Decision-Support Systems Arch 551 - 5 units Arch Design - Facilities Management Arch
The SoftBound pass inserts code to (1) perform base/bound metadata manipulation prior to every memory operation that reads or writes a pointer, (2) perform a bounds check before
