Secure PIN Authentication for ATM Transactions using Wireless Devices
Full text
Figure
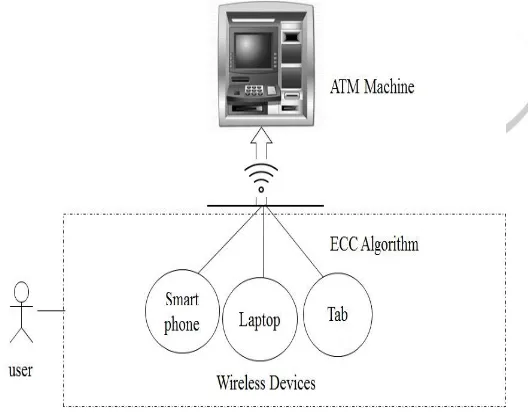
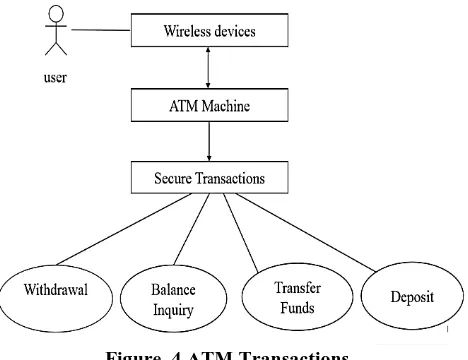
Related documents
As in the transient growth plate cartilage, chondrocyte hypertrophy is considered to be a prerequisite for matrix mineralisation and in osteoarthritis, the increased formation of
To win the new customers and retain the existing ones, banks may adopt the Knowledge Discovery in Databases (KDD) for analyzing the customers’ behaviors and the needs. In the
PrePost uses N-list data structure to mine frequent itemsets and PPC tree to store frequent itemset information.. FIN uses Nodeset data structure to mine frequent itemsets and POC
The extracts from the eyes of the several mutant stocks all gave ab- sorption curves similar t o that of wild type but with lower absorptions in the visible, indicating that
According to the results of this study, it was indicated that the optimist memory telling is effective in decreasing death anxiety and sense of aging in the elderly
output of the new thru function is the added new input (resp. output) vertex and the output (resp. input) of the new thru function is one of the vertices of any existing
In Section 3, we construct an efficiently computable endomorphism on the Jacobian of the quadratic twist curve for each isomorphism class of genus 2 hyperelliptic curves defined over
The net result is that youth employment has remained elusive and unemployment continues to worsen with time creating more economic problems manifested in the