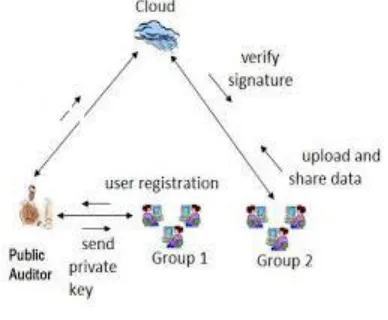
Secure Auditing For Shared Modified Cloud Data with Group User Quieting
Full text
Figure

Related documents
BioMed Central World Journal of Surgical Oncology ss Open AcceResearch Surgical treatment for locally advanced lower third rectal cancer after neoadjuvent chemoradiation with
CUAJ ? December 2012 ? Volume 6, Issue 6 ? 2012 Canadian Urological Association E224 Cite as Can Urol Assoc J 2012;6 E224 E229 http //dx doi org/10 5489/cuaj 10049 Epub 2011 May 1
Vol 7, Issue 5, 2014 ISSN 0974 2441 CHEMICAL CHARACTERIZATION AND BIOLOGICAL ACTIVITIES OF EXTRACTS OFTHREE PLANTS USED IN TRADITIONAL MEDICINE IN BENIN TECTONA GRANDIS, UVARIA CHAMEAE
The results of the case studies show that the voltage dependent load models greatly affect the optimal points of steady state operation, since there is a decrease
Genomic DNA from six individuals was prepared for whole- genome sequencing: diploid Col-0 #1 (used to normalize data from the other individuals), diploid Col-0 #2 (control),
• In the classic ASME NB-3600 procedure only scalar stress differences are used and the actual time and location of the stress in the pipe cross section is lost.. To study the
As such, what ends up happening is that one of the later age ranges (suppose the 50 target for this example) already has a model output above the desired target. 3) The
In Chapter 4, we focus on statistical topic modeling for networks and develop a Relational User Interests (RUI) model as a generalization to the Relational Topic Model (RTM) in