International Journal of Computer Science and Mobile Computing
Full text
Figure
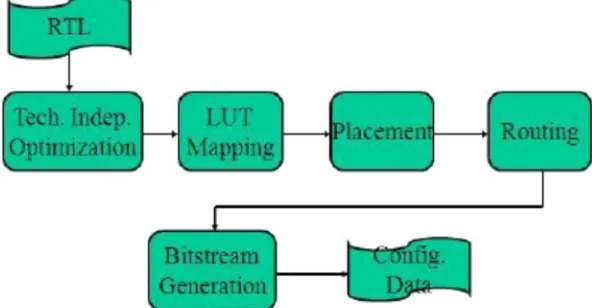
Related documents
Perfectly binding, see Binding Perfectly hiding, see Hiding Perfectly indistinguishable, 7 Proof of knowledge, 8 Prover, 8 Range proofs, 10 Schnorr proof, 12 Soundness, 9.
But as for me, my prayer is unto thee, O LORD, in an acceptable time: O God, in the multitude of thy mercy hear me, in the truth of thy salvation.. Deliver me out of the mire, and
The TOM TAILOR Group comprises TOM TAILOR Holding AG as the ultimate parent company and the subsidiaries listed in the notes to the consolidated financial statements to 31
Do the results of the model, and the empirical data, support the three stylized facts above? In order to answer this question regression analyses were performed on both sets of
If the packet is forwarded from a tunnel interface, the device adds a GRE header to the IPv6 packet, and then adds an IPv4 header to the GRE header according to the tunnel source
Furthermore, across New York State, the Energy Services for Schools Program has identified and installed numerous photovoltaic solar panel sites as an education tool
Although there are articles and studies on the importance of on-time high school completion and collaborative efforts between individuals in the public education and health
This suggests that, in a patient with a petrous bone fracture after a head injury, the radiologist interpreting the CT brain scan should actively look for fractures of other bones