User Behaviours Associated with Password Security and Management
Full text
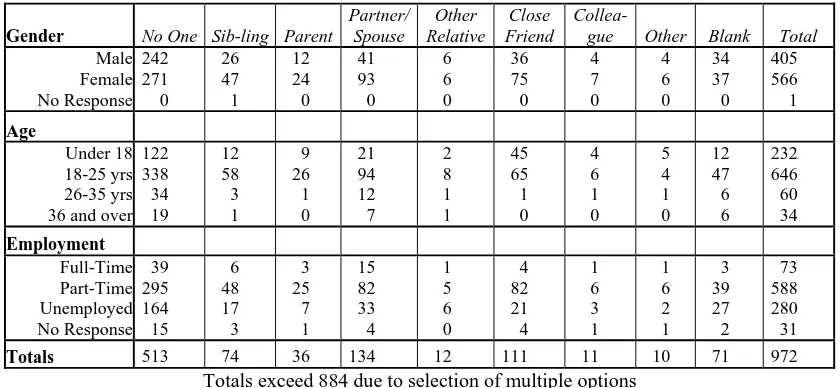
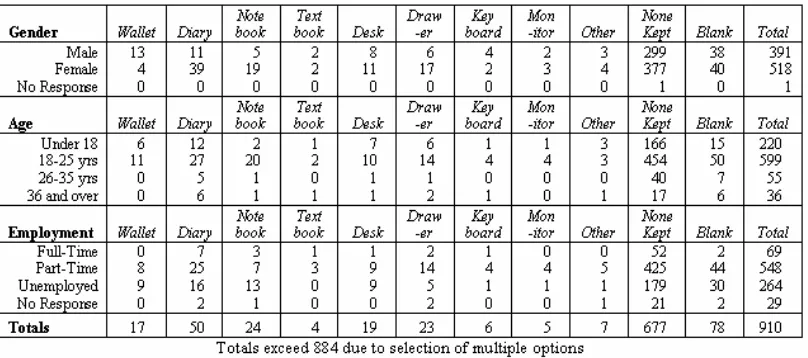
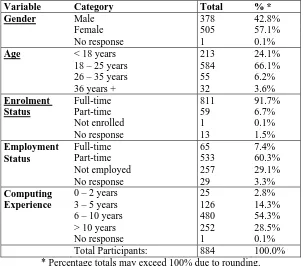
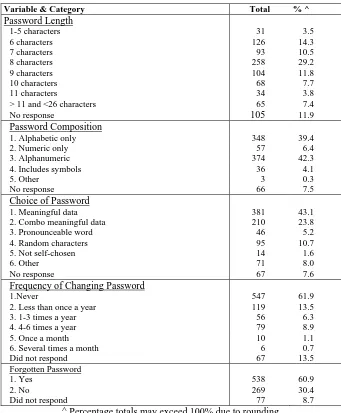
Figure


Related documents
The Zambia Vulnerability Assessment Committee (Zam-VAC) carried out the December Rolling Assessment with the objective to update and further explore the results to determine
As a consequence in the past fi scal year GEA Group’s order intake fell by 1.1 percent year- on-year (excluding the Thermal Engineering Division, which is characterized by large
The seismic profiles show the Bone basin is bordered on both sides by two uplifted basement high and in the middle by flat lying young sediment those are indicate there is an
• Modify the statutory accounts preparation process to produce financial reports using accounts production or end-to-end financial reporting software that offers built-in
Finite course of therapy No resistance Higher rate of HBeAg loss in 1 yr Higher rate of HBsAg loss with short duration therapy* SQ administration
As following up our previous studies on development and optimisation of Hydrophilic Interaction Liquid Chromatography-High Resolution Mass Spectrometry (HILIC-HRMS)
touring to ARKEN Museum for Moderne Kunst, Copenhagen, Denmark Joan Miró , Graphikmuseum Pablo Picasso Münster, Münster, Germany Joan Miró, Galería Leandro Navarro, Madrid,
Although a lot of attention has been paid to the concept, ontologies, taxonomies and approach in the field of strategic management, information systems, digital business