Implementation & Security Analysis for RSA based Algorithms on Variable Key Length
Full text
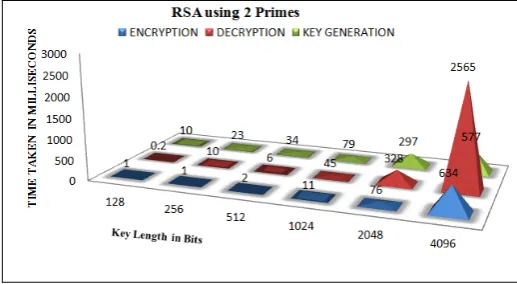
Figure



Related documents
New propose for dengue encephalitis definition: (1) presence of fever (2) acute signs of cerebral involvement, such as altered consciousness or personality and/or
Therefore, previous studies of healthcare reform in China mainly used a macro perspective to focus on the challenges of reform or medical and economic outcomes, e.g., health-
Aim of the present study was to explore the influence of demographic and disease related factors on parental HRQoL, mediated by employment, income, leisure time, holiday and
of the adoption of this conceptual model as a facilitator of analytical studies of the various.. A Monthly Double-Blind Peer Reviewed Refereed Open Access
We note that Lactobacilli constitute the majority of the pro- biotic bacteria population in the dietary supplements (Table 1) and have therefore excluded contributions of
AFB: Acid fast bacilli; ART: Anti-retroviral therapy; ATS: American Thoracic Society; ATT: Anti-tubercular therapy; CDC: Centers for Disease Control; CMO: Cystoid macular edema;
Use of information technology enables automation of data mining and knowledge that help bring some interesting patterns which means eliminating manual tasks and easy data
The advantages of metalworking fluids and its performances with respect to the cutting force, surface finish of work piece, tool wear and temperature at the cutting zone have


