CENTRALIZED KEY DISTRIBUTION USING QUANTUM CRYPTOGRAPHY
Full text
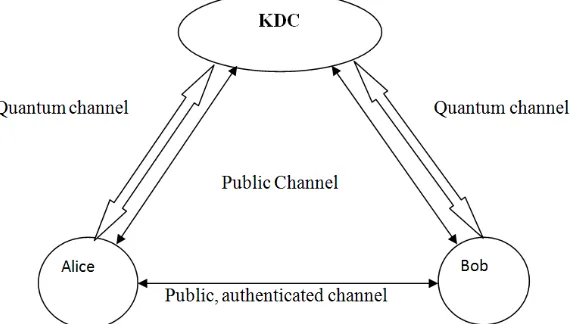
Figure

Related documents
Toward a Database of Geometric Interrelationships of Protein Toward a Database of Geometric Interrelationships of Protein Secondary Structure Elements for De Novo Protein Design,
6, the quadratic model derived from red edge data gave a higher leaf area estimate at high ground cover levels and a lower leaf area estimate at low levels of ground cover than
Abstract : This paper tests the relative version of purchasing power parity (PPP) for a set of ten Asian developing countries using panel cointegration framework.. We employ
Milner PI, Wilkins RJ, Gibson JS: The role of mitochondrial reactive oxygen species in pH regulation in articular chondrocytes. Tattersall AL, Meredith D, Furla P, Shen M-R,
In addition, we showed that the underlying scheme with double Rayleigh fading channels
19. Defendants Roy Wilbanks, Floyd Clack, Gary D. Incarnati, Mohamed Okdie, Francine Parker, Thomas W. Stapleton are members of the Board of Control of Eastern Michigan
Also, tenuigenin significantly ameliorated the degeneration of dopaminergic neurons and inhibited NLRP3 inflammasome activation in substantia nigra of MPTP mouse model.. We
VI. Section IV) and error-sensitive permissions (cf. Section V), we now study the relationship between them in order to identify potential correlations between apps that use