Cross Processor Cache Attacks
Full text
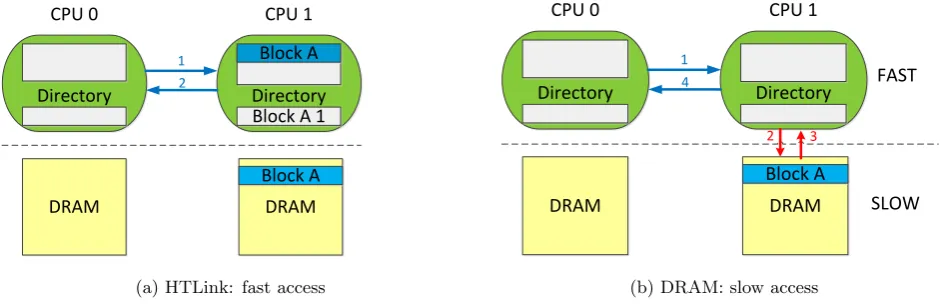
Figure



Related documents
The emotion caused by what for a moment seemed almost a diplomatic incident was diverted by the appearance of two Chinese servants in long silk robes and four-sided hats
Read from main memory by processor 0 of the blue line: line is dirty (contained in P2’s cache). Request: read
All stationary perfect equilibria of the intertemporal game approach (as slight stochastic perturbations as in Nash (1953) tend to zero) the same division of surplus as the static
Caching & Cache Structures CACHE Processor Main Memory Address Address Data Data Address Tag Data Block Data. Byte Data Byte Data Byte Line 100 304 6848 copy of main
• Flush cache whenever needed (e.g., write dirty data to main memory before I/O write). • Similarly, invalidate cache before
Ten years into the reign of Thorin the First, son of Thráin the Old, the King resolved to remove the royal house of Durin’s folk from Erebor to abide in the Grey Mountains.. At the
Step 1: Draw the configuration diagram.. • Problem 11: For the mechanism shown in figure link 2 rotates at constant angular velocity of 1 rad/sec construct the velocity polygon
They can pick up four bridge hands, put them together, riffle eight times, and deal each card back to its original holder, (NOTE: JNH is in error here, TOO perfect riffle


