Survey about Cloud Computing Threats
Full text
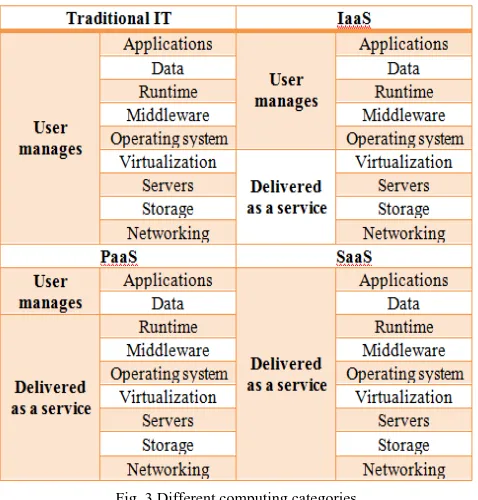
Figure

Related documents
Insurance Absolute Health Europe Southern Cross and Travel Insurance • Student Essentials. • Well Being
A number of samples were collected for analysis from Thorn Rock sites in 2007, 2011 and 2015 and identified as unknown Phorbas species, and it initially appeared that there were
There are eight government agencies directly involved in the area of health and care and public health: the National Board of Health and Welfare, the Medical Responsibility Board
Given the limited spatial resolution of the hyperspectral sensor used in this work, a new method is presented that takes information from the co-registered colour images to inform a
The Lithuanian authorities are invited to consider acceding to the Optional Protocol to the United Nations Convention against Torture (paragraph 8). XII-630 of 3
Reporting. 1990 The Ecosystem Approach in Anthropology: From Concept to Practice. Ann Arbor: University of Michigan Press. 1984a The Ecosystem Concept in
The Asia Tour: Tokyo Dental College (Japan), Korean Dental Society (Korea), National Kaohsiung Medical College, National Tainan Medical College (Republic of China), Hong
The specific aims of this study were to evaluate the effect of Azacitidine and Lenalidomide MDS therapy on: cell cycle regulation, hematopoietic differentiation, gene mutation and