Measuring Security Requirements for Software Security
Full text
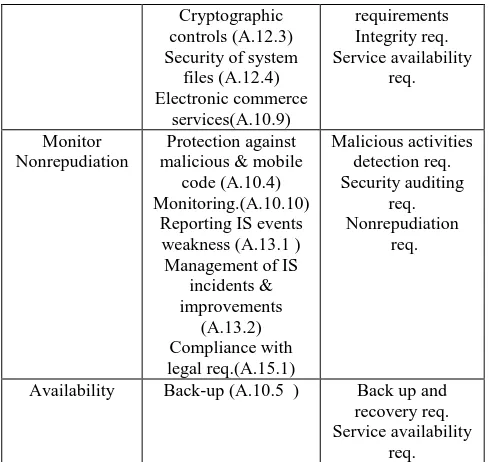
Figure
Related documents
The consumers’ surplus obtained from the use of both information goods includes four e ff ects: the negative e ff ect on illegal copiers because of the increase in the copying cost K
A significant change in the system towards the achieving "free movement of the judgments" is the introduction of the European Enforcement Order (EEO) (Regulation (EC)
www.nordsonefd.com info@nordsonefd.com +1-401-431-7000 Sales and service of Nordson EFD dispensing systems are available worldwide... Large textured ribs provide an
Kosa 1 Kosa 2 Čelinska a Kumanic Zaton na Ramči Goja Biological and landscape diversity, protected areas Close to biocorridor of southeast Dinarides, proximity to
For example, you can lock components in position, create routing points and add routing planes and pipe racks to the constraint list.. All of these facilities are explained in
Arrowgrass Early growth in spring, this plant contains prussic acid highly toxic after frost, also toxic when dried in hay.. Black Locust Pea like leaves and pods, sweet smelling
Ukoliko proizvođač isporučuje svoje proizvode nekom od trgovinskih lanaca u Evropi, sertifikacija prema EUREPGAP standardima može se pokazati kao neophodnost. Takvi
Color Image Reader Unit-B2, Printer Cover-C1, iR Pedestal (New), Inner 2way Tray-F1, Inner Finisher Additional Tray-A1, Buffer Pass Unit-G1, External 2 Hole Puncher-B1, Copy