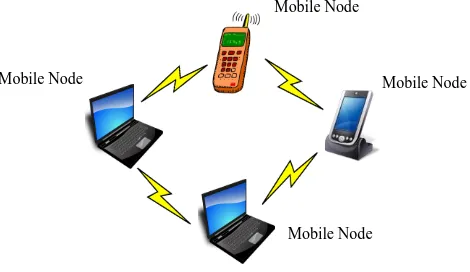
Analysis of Security Threats and Vulnerabilities in Mobile Ad Hoc Network (MANET)
Full text
Figure


Related documents
These results show that use of sesame oil delays the onset of phlebitis induced by peripheral intravenous infusion of amiodarone in the intervention group. In line with the
In March 2003, the Resource Management and Audit Scrutiny Panel considered the following motion submitted by Councillor Wheeler: “To instruct the Director of City Development
These include changing how C is allocated in fixed and dynamic schemes based on data from current forest syntheses and different parameterization of allocation schemes for
Redundant Radix-4signed digit encoding technique, it has high performance compared with the modified booth.. algorithm and also it has lass decoding time for data transmission.In
This study directed to investigate and determine the genetic diversity and relationship of the tidal swamp rice germplasm of the South Kalimantan Province, Indonesia using
The purchase of this arrangement includes a permission license to copy as needed for use within your non-profit.. church
The data presented reflects that the quality improvement initiative influenced movement towards meeting the aims of creation of buy-in for standardized education and screening process
In summary, our approach to construction of a PACC instrument is to select items from the literature to measure the four commonly found dimensions (cultural attitudes;