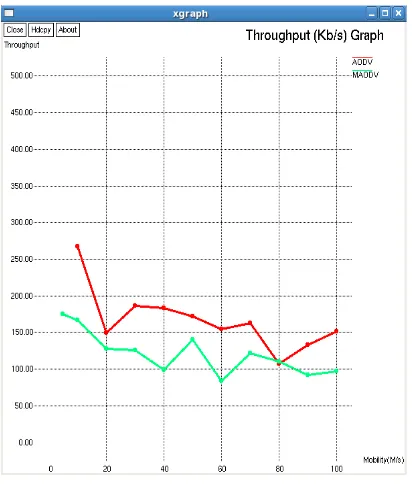
An Innovative Approach to Detect the Gray Hole Attack in AODV based MANET
Full text
Figure



Related documents
and in-game emotions on cognitive interference during sport performance: The moderating role of self-confidence and reappraisal..
The Figure 1.a represents the SEM micrograph of pure PPy. The figure represents the size and spherical nature of PPy particles. The SEM micrograph is shown a characteristic peak
reduce at least 20% the defects generated during the welding process in the Manual Finish
(a) and (b) FDCs for behavioural parameter-value sets for Dynamic TOPMODEL in the Brue catchment for calibration in 1995– 1996 using R FDC − V (all FDCs plotted as grey/shaded lines),
International Journal of Scientific Research in Computer Science, Engineering and Information Technology CSEIT1833369 | Received 20 March 2018 | Accepted 31 March 2018 | March April 2018
Unlike Oryx and Crake , however, the film does allude to a past where the merits of pure research were recognized: “Yet it’s in this minor facility that Wells created Renovor.
Klason lignin and sugar content of the wild type group and the different genetic lines of transgenic aspen subjected to different decay treatments.. Syringyl to guaiacyl lignin
Tygar, 2010 : Machine learning advocates have projected learning-based systems for variability of security applications, containing spam detection and network