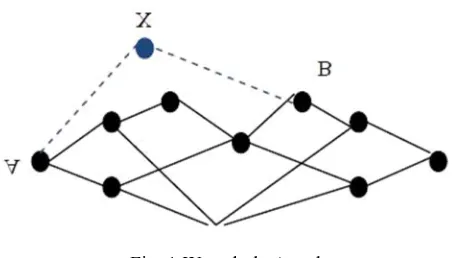
Security of Wireless Mesh Network from Denial of Service Attack
Full text
Figure
Related documents
Expression and activation of the nonreceptor tyrosine kinase Src leads to tumor cell growth, survival, and metas- tasis, and is an indicator of poor prognosis in
4.1.1 A Magistrates’ Court, the Crown Court and the Court of Appeal (Criminal Division) may order the payment of any costs incurred as a result of any unnecessary or improper act
capable of getting optimized solutions for a number of problems like Time Table Scheduling for which no other algorithm exists. It is inspired by nature as
Solving the semantic interoperability problem of metadata schemas by using a primitive event-based knowledge representation scheme was one of the ma- jor challenges in creating the
Brookhart (2010) formative assessment includes having clear learning aims, crafting clear lessons and assignments that communicate those targets to students, and
(2012), Robot built by use of arduino, uno, adafruit motor shield,pololu‟s,QTR-8R line sensors, Islam and Rayman (2013), Built robot by use of op-amps and
In order to overcome the lack of traditional photograph encryption procedures based on dimensional (2-D) maps which may be used best for permutation, this paper presents a
Chapter 3: Solid-State NMR of Magnus' Green and Pink Salts 3.1 Platinum chemical shift tensor parameters determined from 195 Pt static and MAS NMR