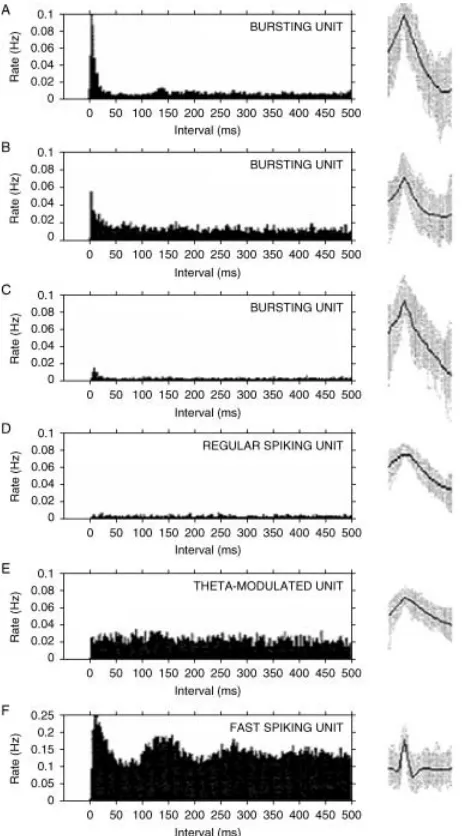
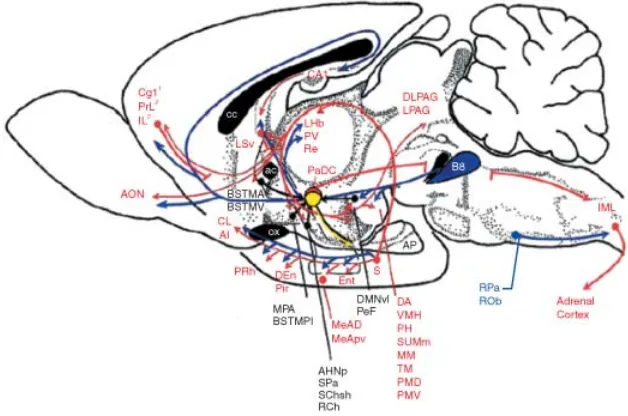
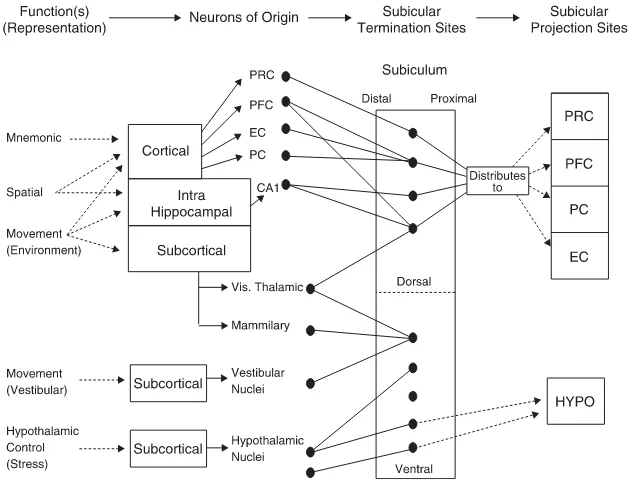
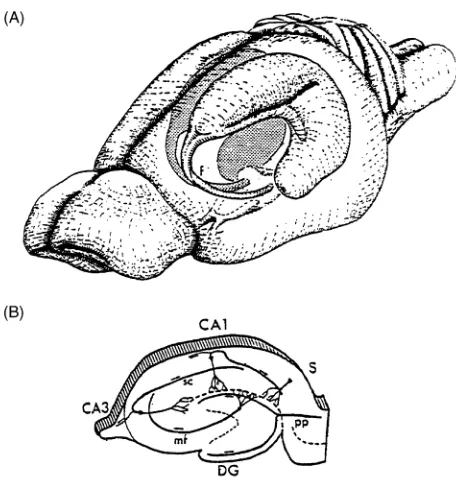
The Subiculum: What It Does, What It Might Do, And What Neuroanatomy Has Yet To Tell Us
Full text
Figure
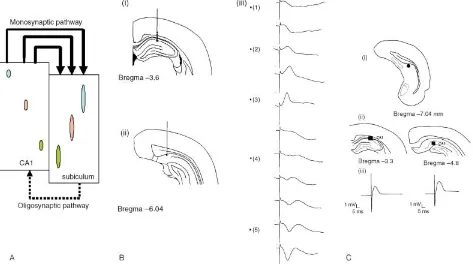
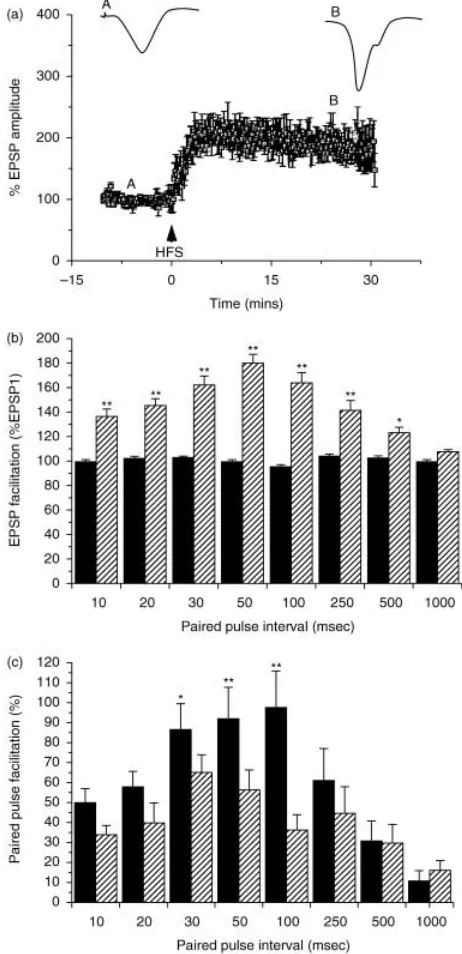
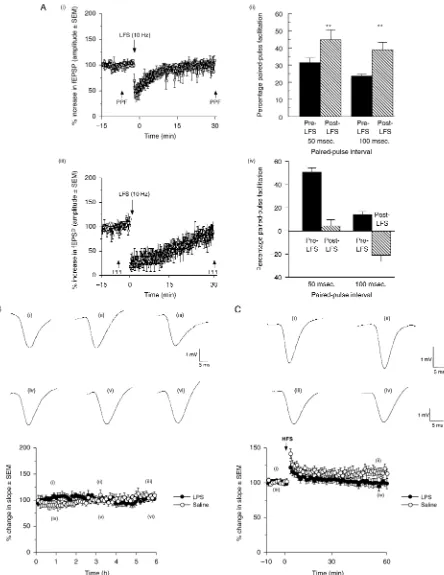
Related documents
Online – using the online form, you have to enter the required data, and after generating the boarding pass, you have to print it and take with you to the airport (you will see
This elite 2 + 2 programme offers H.I.T.’s high achieving students the opportunity to obtain the BEng (Hons) Mechanical Engineering degree from the University of Bath, UK.. After
The JBoss Enterprise SOA Platform includes service- oriented architecture (SOA) open source middleware such as JBoss Enterprise Service Bus (ESB), JBoss jBPM, JBoss Rules and
We find that households that experienced a land dispute before the first-stage land reg- istration was implemented are more likely to be interested in a second-stage
100–120(–140) µm wide; apex outwardly greenish black to black, 80–120(–140) µm wide, K–, slightly concave to slightly convex, then occasionally with a minutely papillate
Thus, probably the most challenging of the 16 data sets for a DS detection method (see also Table 1) consisted of (1) one condition containing 15 samples and a second con-
That the certificate of insurance shall contain a provision or endorsement that the coverage afforded will not expire, be canceled, materially changed, nor renewal refused
A5: Cross Site Request Forgery (CRSF) A6: Security Misconfiguration A8: Failure to Restrict URL Access A10: Unvalidated Redirects and Forwards A7: Insecure Cryptographic