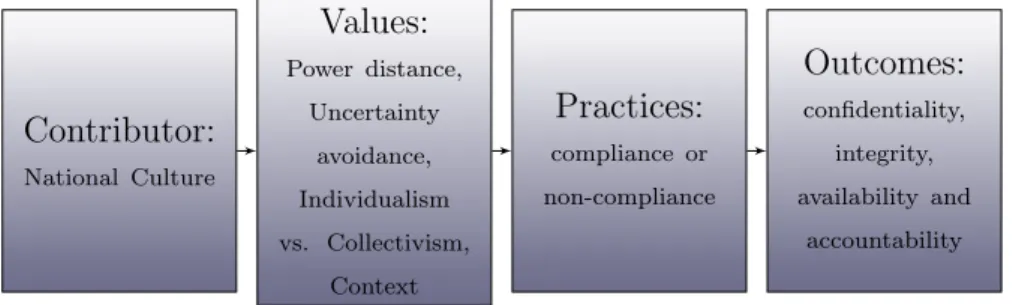
Information security management: A case study of an information security culture
Full text
Figure

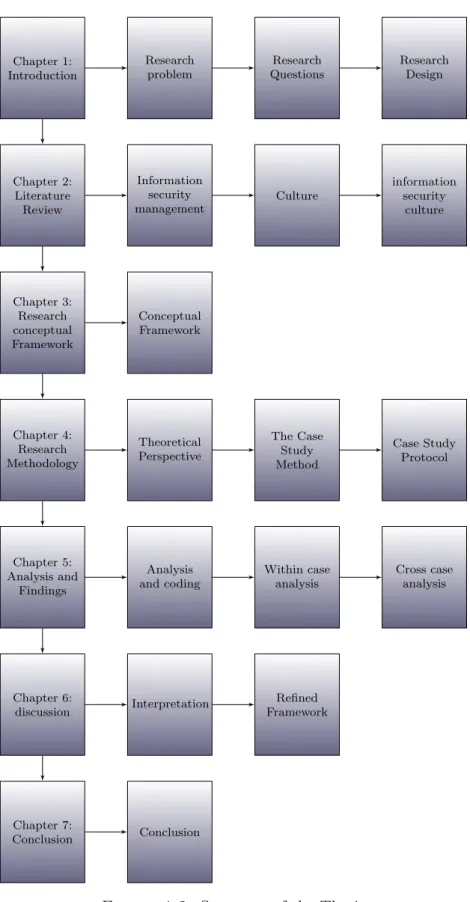


Outline
Related documents
The purpose of this paper is to contribute to the understanding of the gender gap in investor behavior by taking a behavioral perspective and, specifically, resting on the concept of
field at temperatures between 2 and 20 K (left) and the temperature-dependent magnetic entropy change for Fe 8 -A. field at temperatures between 2 and 20 K (left) and
Deep Dip Velocity-Nadir Velocity Target Velocity Track Damps rates to follow profile of planet-relative velocity vector around periapse; APP: +i tracks planet-relative velocity
35 Female labor participation may generate many intra-household effects: time allocation effects (e.g., both parents working have less time to allocate to child care or domestic
The interactive experience provided by this IPE event was an opportunity for students to practice professional collaboration around the topic of food intake, which is best
CITY OF PAWTUCKET’S PURCHASING OFFICE GENERAL CONDITIONS OF PURCHASE All City of Pawtucket purchase orders, contracts, solicitations, delivery orders and service requests shall
Assignment 1: Complete the tasks and answers all the questions listed in “What to do” in App: ID Dynamics Introduction. Characterizing Infectious Disease States. At home ,
Finally, the presented interaction proteome uncovered a large set of interactions with proteins genetically linked to a range of human diseases, including cancer, suggesting