Similarity Based Large Scale Malware Analysis: Techniques and Implications
Full text
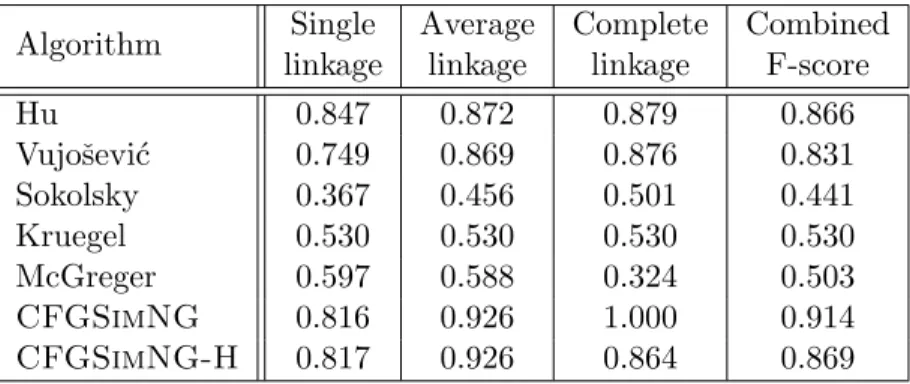
Figure



Related documents
Studies attempted to explore mobile genetic elements that alleviate conflict molecular systems are insufficient to draw conclusive answers (Fernández et al., 2018) As
BIA300 Interior Architecture Technology Driven Design (Coming in 2015) Curtin BIA310 Interior Architecture Technology System Solutions (Coming in 2015) Curtin BIA320
Section 12: ECOLOGICAL INFORMATION Ecotoxicity No data available. Persistence and degradability No
The total cumulative exergy consumption assuming 40% material reutilization is 222.5 PJ (see Fig. With no material reutilization at all, the estimated total exergy loss is 233
The aim of this study was to assess changes in tree AGC stocks in the Taita Hills and its foothills as a case study of land cover change impact on tree AGC stocks in East Africa.
Shell Helix Plus Extra SAE 5W-40 Shell International Petroleum Company. Shell Helix Plus S SAE 5W-40 Shell International
Also, the use of electronic payment systems, especially the mobile payment systems, has grown significantly over time and contributed towards wider outreach of
A report wizard can be used to create a report (in MS Word/Excel, Adobe, PDF, HTML etc) by accessing report scripts within the package or that have been created (user defined)





