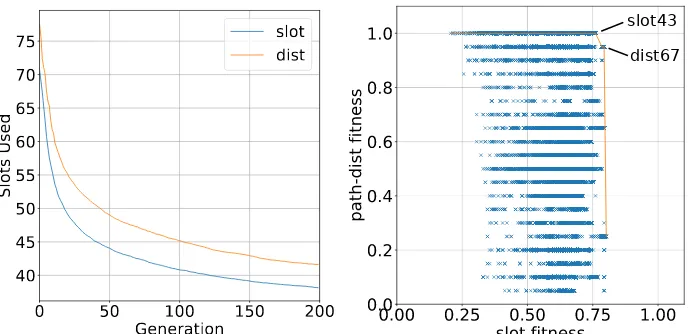
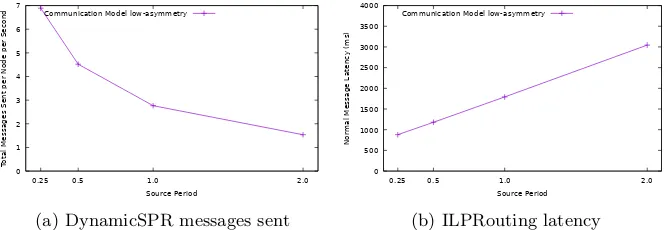
Towards optimal source location privacy aware TDMA schedules in wireless sensor networks
Full text
Figure




Related documents
At an advanced age, when multiple co-morbidities are accu- mulated (partly due to the dysfunction), the injury (both septic and aseptic) of loose connective tissue together with
Among the groups, Group I allocated the four accessions of Keitt mango; Group II consisted of the two accessions of Rosa mango and two of Maçã mangos, while Group III allocated
availability of rural facilities in the selected villages and adoption of new agricultural. technologies by the paddy farmers, therefore, the selected farm
The aim of this study was therefore to examine whether endocrinologists, cardiologists, and nephrologists have different opinions on the reporting of diabetes as the UCD. The
In CP-ABE scheme, attribute policies are associated with data and attributes are associated with keys and only those keys that the associated attributes satisfy
constructing constant price series (in previous year prices) and that used before 2003 (using a base year) is necessary to maintain the growth rates presented
Department of Electronics and Telecommunication, Annasaheb Dange College of Engineering, Ashta Sangli, India. makes the system less invasive, but it is less accurate when
These cases read data from ReadTestData class as TestNG doesn’t involve feature files and writing scenarios into it.. The cases execute based only