Architectural Data Security in Cloud Computing
Full text
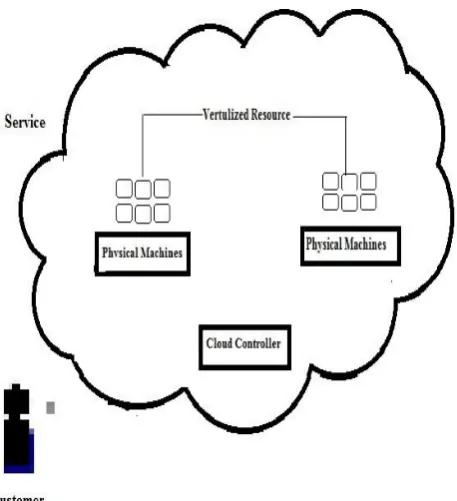
Figure
Related documents
In Mexico, Rossini reigned supreme for many decades to come both in the general public’s perception and in terms of critics’ taste. The endowment of Rossini’s music with
proposed in Wilson and Einbeck (2015, 2016) these exceptions correspond to the observed data either containing no zeros, or consisting entirely of zeros, and hence the adoption
To operate each of the smart water grid programs as a single program, input and output data from multiple water source real-time measurement for water loop distribution and the
28 September 2012 5 October 2012 8 October 2012 12 October 2012 2 November 2012 16 November 2012 28 November 2012 28 November 2012 Chief Executives of all authorised insurers
Quadrant for North American Corporate Telephony, 2005 specifically focuses on the technology suppliers that manufacture and distribute hardware and software products to
Regarding the fact that companions without health insurance for their children were satisfied with the quality of care of the Pediatric Emergency Room, their satisfaction may
● RESULTS: The eye’s higher order aberrations had a small, but significant increase (P ⴝ .03) of approximately 30% 2 months after cutting a flap. No systematic changes were
As institutions that function within both the health and legal systems, health-related adjudicative tribunals must also overcome the realities of the legal sector that may not