Refining the Confidence Level for Optimistic Bandit Strategies
Full text
Figure

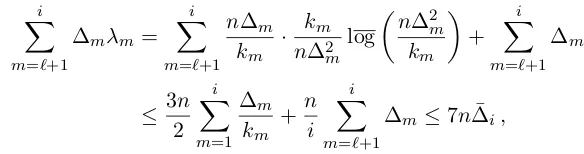
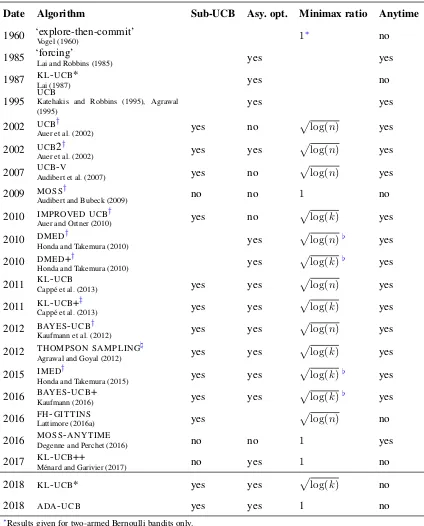

Related documents
If the panel to be installed does not properly align with the panel next to it that you must STOP and DO NOT INSTALL as there might be three possibilities
• The optimal offline resource allocation schemes for the Gaussian multiple access channel (MAC) with two transmitters powered by a shared energy harvester are developed with
Acquistion of the Morphological Structure of the Lexicon Based on Lexical Similarity and Formal Analogy Coling 2008 Proceedings of 3rd Textgraphs workshop on Graph Based Algorithms in
This is used in the large animal and small animal surgical areas where blood and bodily fluids are exposed to our housekeeping staff and other patients; HDQ is used to help kill
Neofusicoccum luteum is reported for the first time from olives ( Olea europaea), causing fruit rot and leaf necrosis.. Affected fruits initially became brown with pycnidia
Urban livelihood asset is an accumulation of labor capital and financial capital. The existence of a slum area in the coastal area of Untia with an area of 7.13 ha of 740.10 ha of
In molti pazienti con malattia mitocondriale soste- nuta da mutazioni del DNAmt, inclusa la mutazione 3243A > G, vengono riportati sia il disturbo depres- sivo unipolare che
Grounded on the trust–risk framework (Mcknight, Cummings, and Chervany.. 1998), this study contributes to the operationalization of privacy concerns measurements in online