Major Web Application Threats for Data Privacy & Security - Detection, Analysis and Mitigation Strategies
Full text
Figure
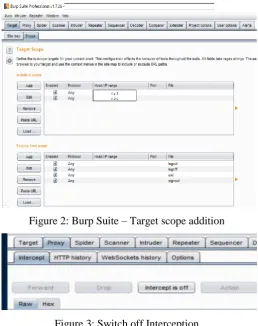
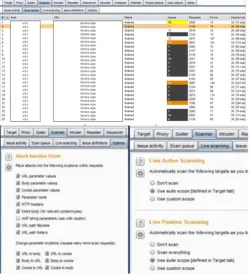

Related documents
In addition to such crucial activities for upper-division students and their faculty advisors, some honors thesis programs consciously highlight the honors thesis early on in
Several privacy-preserving techniques [13] for association rule mining have also been proposed in the past few years. Various proposals and algorithms have been
Other studies confirm extremely poor performance of online ads by showing that the average click-through-rates of Google and Facebook ads, which show how often web users click an
A statistically significant negative correlation was dem- onstrated in the study cohort between the maternal serum PIGF levels, foetal heart rate (FHR), birth weight and length,
This paper presents the assessment of Voice over Internet Protocol (VoIP) security threats and vulnerabilities along with current security technologies and security patterns..
(A) The solubility of n – alcohol in water decreases with an increase in molecular weight (B) The solubility of n – alcohol in water increases with an increase in molecule
security vulnerabilities in Web 2.0 applications using open source security
外文 中文 類別 37 congratulatory cables 賀電 一般外交辭彙 38 consensus 共識 一般外交辭彙 39 consent 同意 一般外交辭彙 40 consoling cables