Secure Outsourcing of Large scale Linear Programming
Full text
Figure
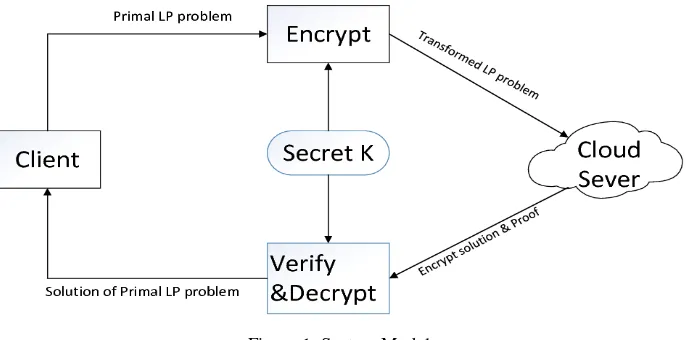
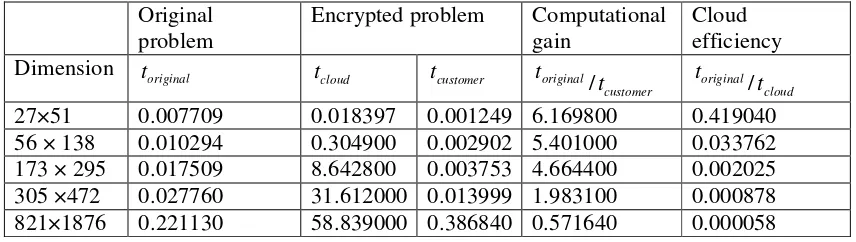
Related documents
Since the heat exchanger will be of externally finned tube design with a high bed-to-wall heat transfer coefficient (>> 2 kW/m 2 K) 12 , the overall heat transfer is
branching archaeal lineages found in 16S rRNA clone libraries from anoxic marine subsurface sediments.. (e.g., Vetriani
9 CS Computer Vision 10 CS Parallel Processing 11 CS Systems Programming 12 EC Mobile Communications 13 IT E-Commerce 14 IT Computer Games. 15 IT Human Aspects
Here we wish to report our results demonstrating the use of TBTU as a coupling reagent in the reaction of carboxylic acids with thiols for the synthesis of thiol esters (Scheme 1).
both MIRT and factor analysis were useful tools for evaluating SJT construct validity, and the dimensions recovered by both methods offered incremental validity to the prediction of
I aimed to address questions such as how the adaptation to environmental temperature is accomplished on the level of enzymes, and how the altered temperature
Data from the 2005 population based cross-sectional study of blindness in Sokoto state was re-analysed to obtain baseline estimates of the prevalence of cataract blindness and
Autonomous Infrastructure, Management and Security (AIMS 2010) , Springer, ser. "Justifying a Policy Based