Electromagnetic Spectrum Analysis Based Hardware Trojan Detection Methodology
Full text
Figure
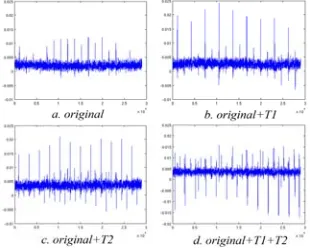
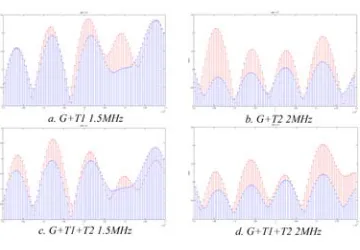
Related documents
If the bargaining unit is formed, the above-school-level educators will be eligible to join FEA as Active Members, with full membership rights and access to all FEA/NEA
When the sample containing target gas flows through the sample cell, a reduction in radiation energy is received by the detector chamber, which causes the temperature and pressure
Firms with a Center of Excellence in place were six times more likely to report “very successful” enterprise-wide BPM initiatives than firms with just a dedicated BPM team, and
Managing the process of establishing learning relationships depends on the retailer’s ability to perform filtering of information received from its customers, to use them and
A systematic review of preventive effect of oral hygiene on pneumonia and respiratory infections in elderly people in hospitals and nursing homes... Dental disease can cause
The three-year risk-adjusted total NPV (net present value) of $161,321 represents the net cost savings and benefits attributed to using the NetApp solution when compared with
Demersal fish landings (t) by commercial and traditional fisheries on the West Coast of Peninsular Malaysia from 1971 to 1997.. Source: Annual Fisheries Statistics 1965
To approximate the consumption of the rich, I use two approaches: one explores the data from Piketty, Saez and Zucman (2016) on the income and wealth of the rich to back out a