Mobile Phishing Attacks and Mitigation Techniques
Full text
Figure

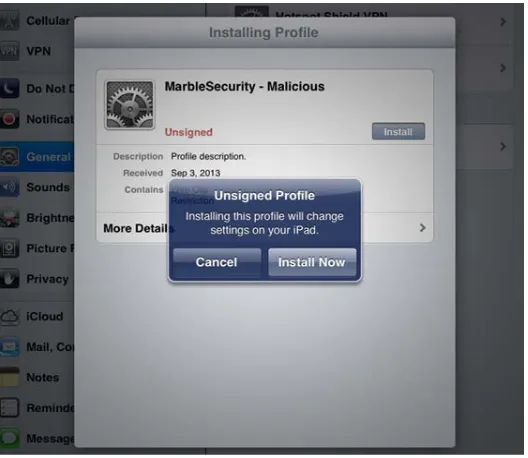
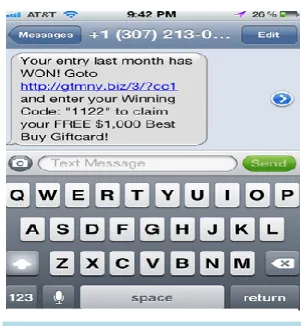
Related documents
improvements are obvious to most practitioners, while the benefits related to cost savings, quality improvement, and risk management still remain unsatisfied. Yet all the six
Ethernet Features 10 Mbit/s operation (10BASE-T; IEEE 802.3i; IEEE 802.3 clauses 13-14) 100 Mbit/s operation (100BASE-TX; IEEE 802.3u; IEEE 802.3 clauses 21-30) 1000 Mbit/s
Thus, in Chapter 4, I will argue that the key to understanding new media rhetoric and writing in a world of nonhuman technological actors will be to revise our understanding
However, if clients had a positive or emotionally intense music listening phase and felt that the therapist had facilitated the postlude in an ineffective manner,
for both docking and affinity prediction algorithms: Structure predictions success rates and correlations with experimentally obtained affinities are lower than reported
At fine scale, JEV ecology is indeed largely affected by both land cover and land use as these factors affect vectors’ and hosts’ ecology (Figure 1). Once the JEV is introduced,
It is difficult (and arguably impossible) to provide a principled rationale for distin- guishing the tax treatment of payments made to provide a return on equity from the tax
We compare size and power properties of time series model diagnostic tests using their asymptotic χ 2 distribution and bootstrap distribution (dynamic and fixed design) against