Network Access Control Technology—Proposition to Contain New Security Challenges
Full text
Figure
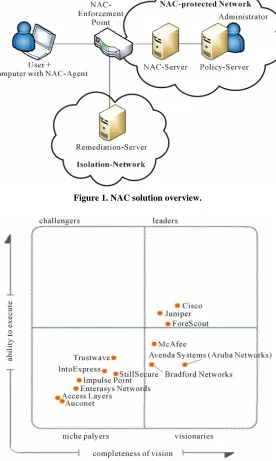
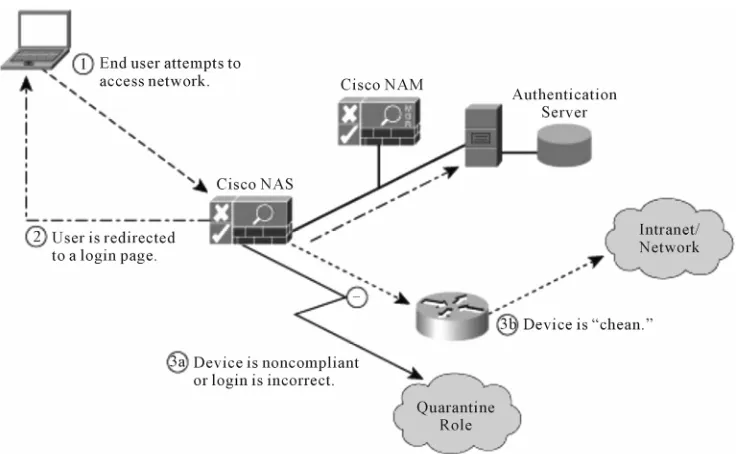
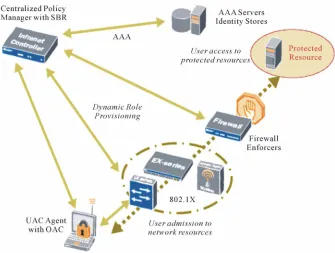

Related documents
In a wired environment, where simple Extensible Authentication Protocol (EAP) pass-through switches are used at the edge of the network, then 802.1X or web authentication is
• Makes an access control decision based on the attributes and/or supplied identity information.. • Redirects the user to a login endpoint if no identity information
After Policy Creation is complete and enforcement actions have been decided upon, it is critical to individually test the policies to ensure complete understanding of estimated
• Identity-driven security and access control: – Per-user ACLs: permits or denies user access to specific network resources based on user identity and time of day, allowing
• Identity-driven security and access control: – Per-user ACLs: permits or denies user access to specific network resources based on user identity and time of day, allowing
By repeating the step name over and over while moving your body and hands as described above, in your best interest and benefit only, CLEAR ALL: 001.. DEVICES - Your entire system
○ If BP elevated, think primary aldosteronism, Cushing’s, renal artery stenosis, ○ If BP normal, think hypomagnesemia, severe hypoK, Bartter’s, NaHCO3,
When it comes to developing the right talent for this sector, we need to predict industry needs, respond to the diversity of demand from companies, and equip talent with the

