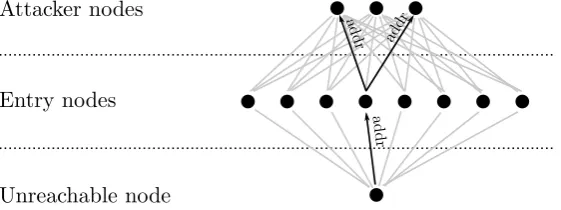
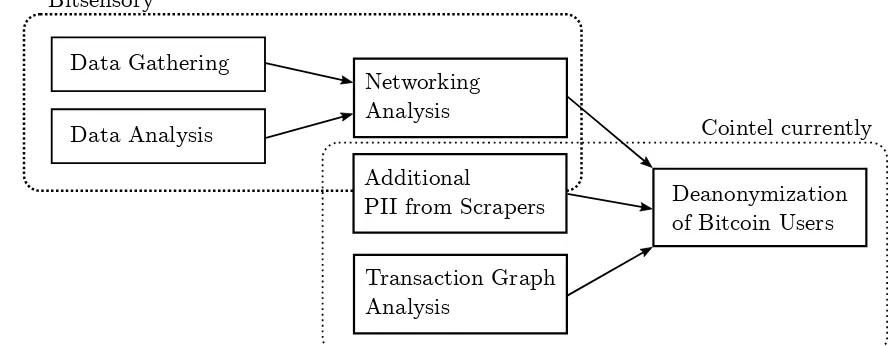
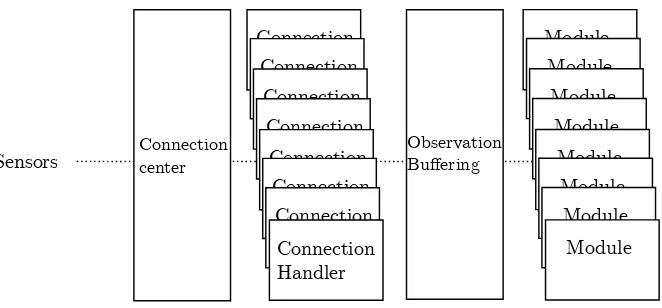
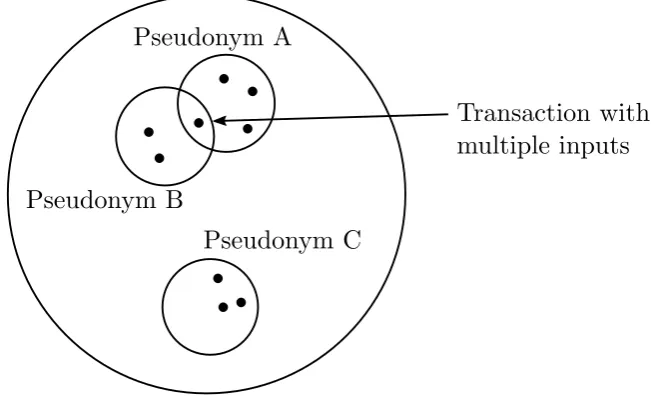
Gathering intelligence from the Bitcoin peer to peer network
Full text
Figure
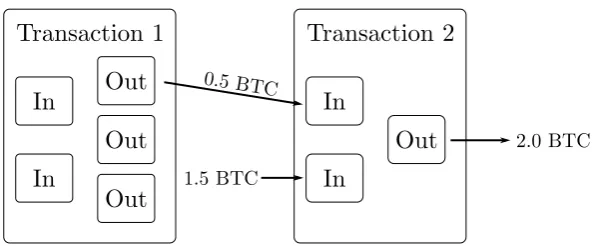
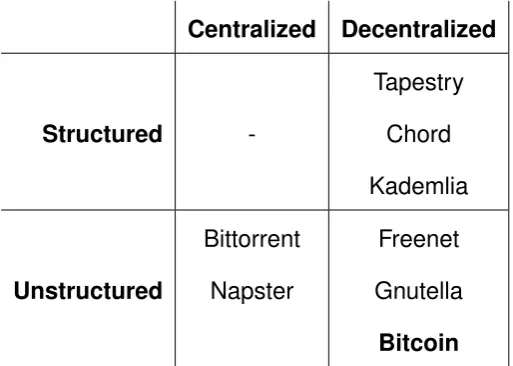
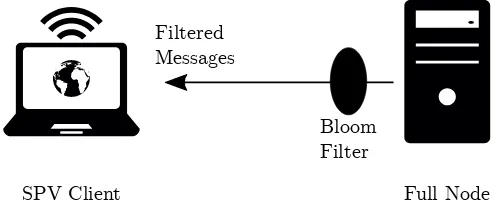
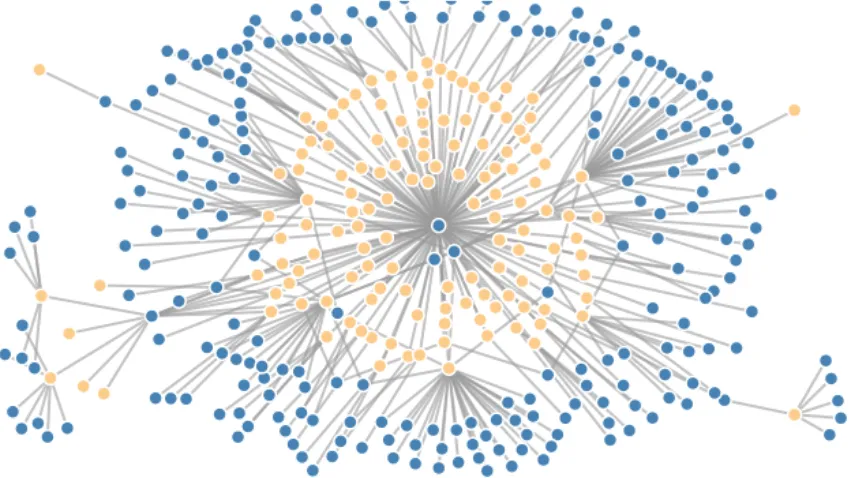
Related documents
The performance of RDTs is very often analysed from the clinical point-of-view: the capacity of RDTs to iden- tify correctly malaria positive and negative samples is evaluated
- Organizational communication of changes on reward structures 4. Labour market characteristics and external equity. Grading - Group assignment with 3 phases: the weight of
This study extended previous work concerning resilience in the work environment by examining connections between resilience and work-related factors, such as work
Fig. 3 shows a sample results of the denoising process on the trimmed and padded spectrograms. It is apparent that the devel- oped CDAE is capable of performing an effective
Circulating tumor cells with a putative stem cell phenotype in peripheral blood of patients with breast cancer.. Gleghorn JP, Pratt ED, Denning D, Liu H, Bander
Considering the importance of wood density in the estimation of the AGB and the lack of this information for peat swamp forest tree species, research should be dedicated
We agreed the amounts reported by the University on its supplemental schedule of fines and assessments, as reported in the annual financial statement audit for the year ended
In the probe design for DSECT system, the effects of the probe design parameters including the number of GMR sensor, excitation coil thickness and probe diameter were investigated