Fragile Watermarking of Medical Image for Content Authentication and Security
Full text
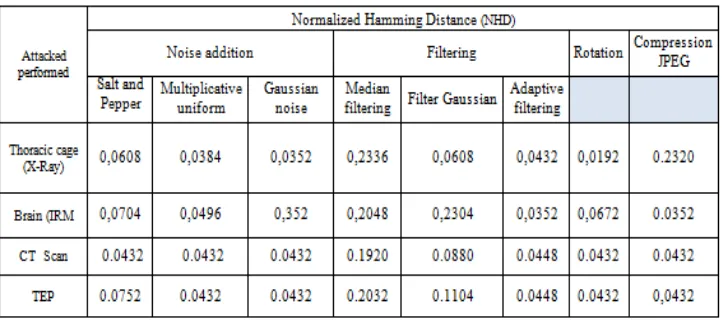
Figure

Related documents
Polemical questions in both the desired and realised colonies arose: How would people in the colonies, particularly those who did not fit into the ethnic and racial
This feature cannot be used to calculate use time as outlined in the sales manual and is incompatible with any standard, optional, or special device utilizing the
En effet, la plupart des enfants nés sous X sont rapidement adoptés après leur nais- sance, ainsi la découverte de leur origine ne peut-elle en aucune façon se substituer au
In this Research work, I have developed an online Punjabi- Hindi spell checker and also developed a new proposed Algorithm for the correction of wrong words according to the
RESEARCH ARTICLE Open Access Evaluation of blood reservation and use for caesarean sections in a tertiary maternity unit in south western Nigeria Oluwarotimi I Akinola*, Adetokunbo O
Keywords: Data mining, analysis, Rough Set Theory, cashless transaction,
The objective of our study is to identify the incidence, causes and peripartum complications associated with pregnancies complicated with IUFD at our tertiary
The estimated coefficient on the efficiency variable, enterprise specialisation, is significantly greater than zero. As reported above, a likelihood-ratio test that this