Detecting Unknown or Fake User Accounts on Different Micro blogging and Social Media Networks
Full text
Figure
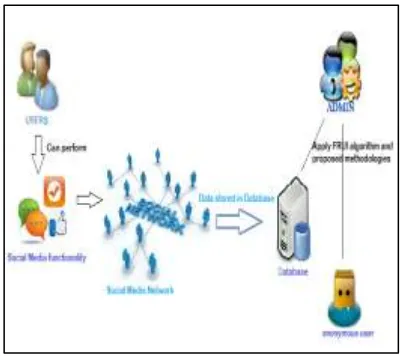
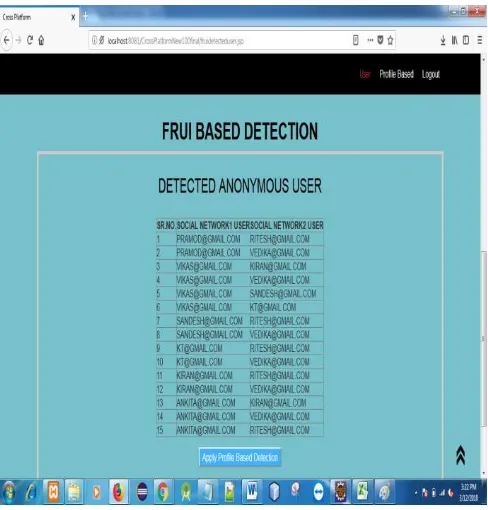
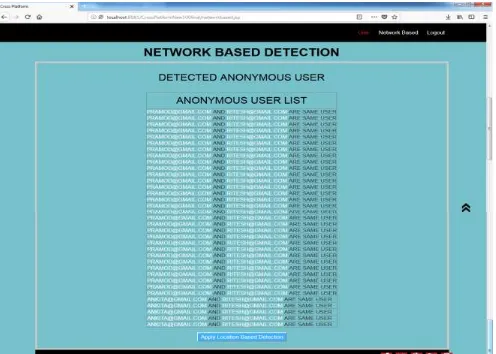
Related documents
This paper provides the following contributions to research on search- based software engineering: (1) we show how a cost-constrained producer/consumer problem can be modeled as a
Good advising should link a student ’ s academic capabilities with his or her choice of courses and major, access to learning resources, and a belief that the academic pathway
Using data from the Federal Reserve Board of Governors, he finds that the rate of state bank failures attributable to mismanage- ment and malfeasance was higher during some
9am Gerardo Biaquis Cynthia Osborne Sylvia Montalvo Mely Hubbard Crystal Huerta.
Comparing N content of all shoot vegetative organs (except the rachis, which was used entirely for mineral analysis) between these time points (Fig. 3), total shoot N
Again, it can be seen that the polarization resistance obtained for mild steel in the free acid solution as well as those containing different concentrations
As a result of the above mentioned, we anticipate that subjective norms may interact with self-efficacy in the prediction of entrepreneurial intentions (see Figure 1).
Comparisons of the percentage reductions eq (1) , eq (3) and eq (5) and their associated 95% upper con fi dence limits (UCLs) and lower con fi dence limits (LCLs) were made