Increasing virtual machine security in cloud environments
Full text
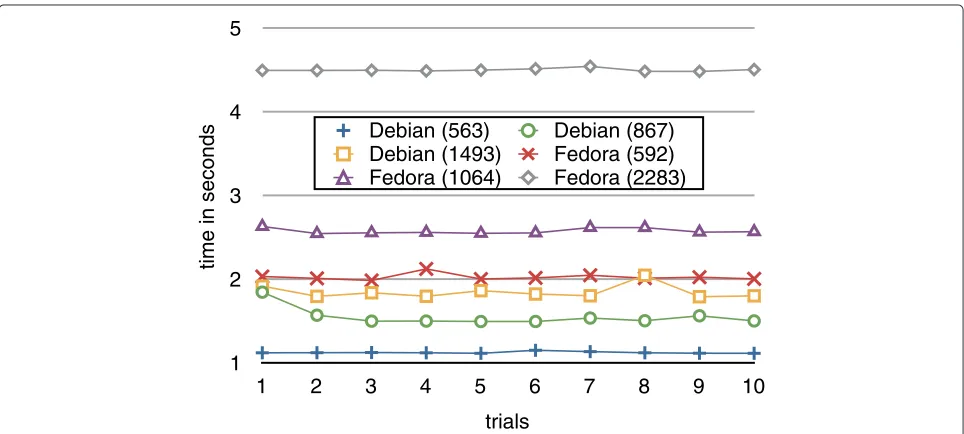
Figure
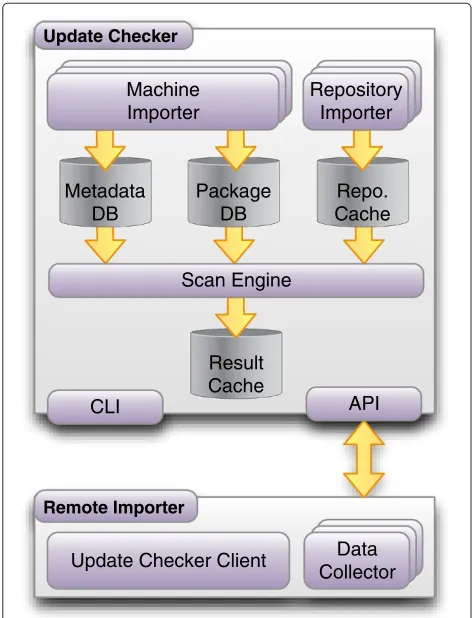
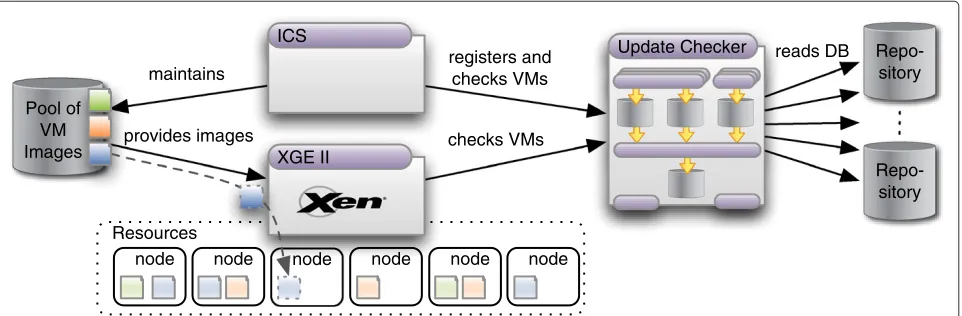


Related documents
The places where the two parties seek justice outside the Court, which Marck Galanter calls Justice in Many Rooms , is not a state court building, but a place/space where the
Instructional Practices: Teacher led instruction Student created composing Listening and evaluating of professional and peer created selections utilizing MIDI Peer
• Focus group of Service Users who participated in the Adult Nursing recruitment cycle.. • Questionnaire data regarding Academic staff’s perspective of engaging SU/carers in
SKEW T BASED MAXIMUM LIKELIHOOD ESTIMATION OF LATENT GROWTH CURVE MODELS WITH NON-NORMAL AND MISSING DATA.. A Dissertation
West NR, Hegazy AN, Owens BM, et al.: Oncostatin M drives intestinal inflammation and predicts response to tumor necrosis factor-neutralizing therapy in patients with
Objectives: Ulcerative colitis (UC) is a relapsing inflammatory disorder of unconfirmed aetiology, variable severity and clinical course, characterised by progressive
The mission of the Bexar County Women’s Bar Foundation is “to protect and promote the well-being of Bexar County and other Texas families through legal, charitable and
(18) Los párrafos originales de Baroja decían: «Es hora, amigos míos, de que los españoles y los vascos no seamos sólo de un país