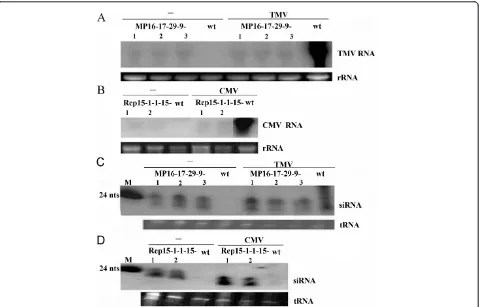
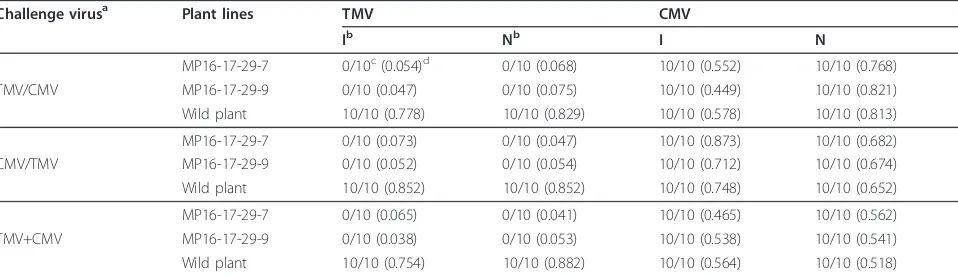
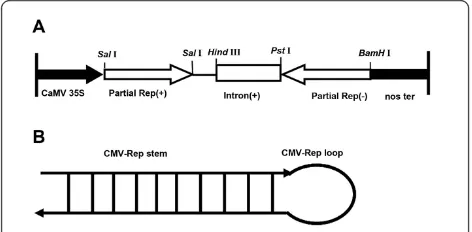
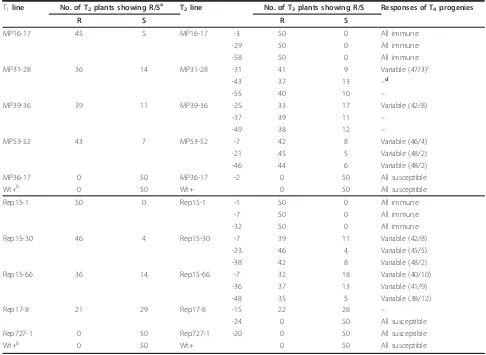
Virus derived transgenes expressing hairpin RNA give immunity to Tobacco mosaic virus and Cucumber mosaic virus
Full text
Figure
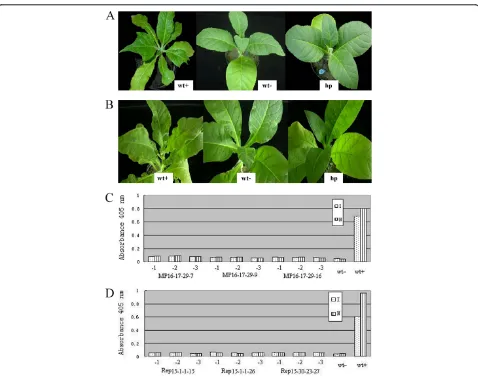
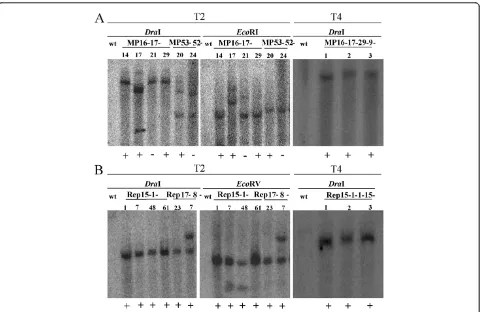
Related documents
ence in axis ratios of the greatest ellipsoid that fits inside the structure and that contains the point of interest, and ranges from − 1 for strongly oblate (discus-shaped)
It is clear from our work that using GPUs can greatly accelerate computation of RNA secondary structure partition functions, allowing calculation of base-pair probabilities for
The content, delivery and evaluation of READ was informed by: (i) studies of patients ’ experiences of discrimination;(ii) studies of stigma and discrimination among
Starting from the 9th week of development, the beginning of the fetal period, the fibers of the lateral pterygoid muscle completely change the position from
A non-rhetorical question for advancing Left research and politics, then: does Global North left-national identity present dangers that differ in kind from those of other
In conclusion, beneficiaries‟ perception of funds sustainability by the Lagos State Contributory Pension Scheme is significantly predicted by fund governance,
Three different positions of masculinity with certain beliefs on the gender order and acceptance of violence within marriage were identified: the traditionalist, the pragmatist, and
Hence, in order to further understand the investigation process of cybercrimes in Malaysia, this paper will briefly discuss the process of investigating cybercrimes under the