Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3348
Recognition of Scenario Instances on Cavernous Features
of Networks using Laser and Wireless Integrations
Sanehaa
Assistant Professor
Govt. College for Women
Gohana, Sonepat, Haryana, India
Abstract
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3349 the product applications. In this structure, the shifting components and advancements are resolved for system criminological and audit.
Keywords: IoT Security, Malware Detection, Load Testing, Network Performance Testing
Introduction
The malware discovery and load entrance testing is required in the system based applications so the general execution and viability of the system [1, 2]. There are various devices and strategies with the coordination of profound learning for system testing and review [3, 4].
There are number of programming items accessible in the innovation showcase that gives the modules of system sniffer utilizing which the framework director can investigate the bundles. Parcel Capturing is the system of catching and logging development. The parcel analyzer is likewise alluded to as a system analyzer, convention investigation apparatus or convention analyzer, bundle sniffer, Ethernet sniffer or just a remote sniffer. Such programming is actually a product program that captures, seize and log the activity going through a system framework. As data streams over the framework, the sniffer gets each bundle and, whenever required, deciphers the parcel's unrefined data, exhibiting the characteristics of various fields in the package, and researches its substance reliable with the appropriate RFC or distinctive judgments.
Dynamic and Passive Sniffing of Network Environment
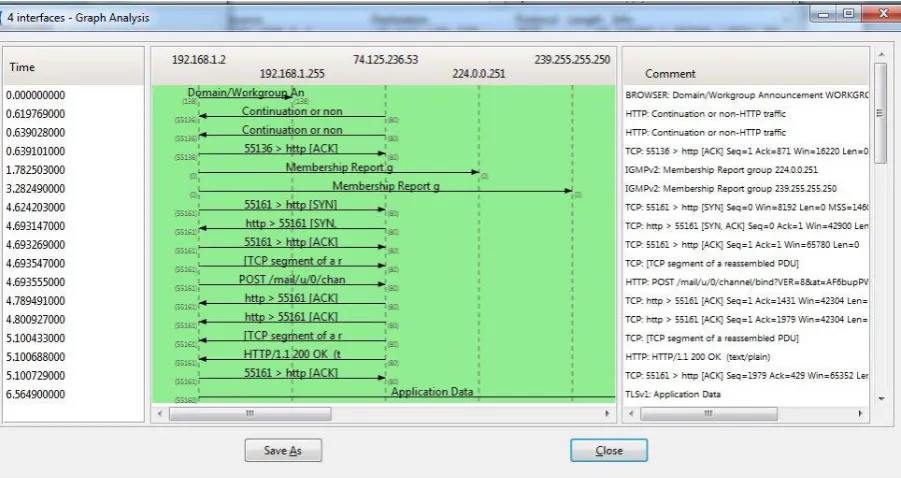
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3350 Highlights of Packet Tracing and Analysis Tools in IoT Environment
There are number of utilizations and utilizations where the bundle analyzers or sniffers can be utilized helpfully. Following is the rundown of the positive parts of parcels following instruments :
• Analyze organize issues
• Detect organize interruption endeavors
• Detect organize abuse by inner and outer clients
• Documenting administrative consistence through logging all border and endpoint
activity
• Gain data for affecting a system interruption
• Isolate abused frameworks
• Monitor WAN transmission capacity use
• Monitor arrange use (counting inner and outer clients and frameworks)
• Monitor information in-movement
• Monitor WAN and endpoint security status
• Gather and report arrange insights
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3351 • Serve as essential information hotspot for everyday system checking and the
executives
• Spy on other system clients and gather delicate data, for example, login subtleties or
clients treats (contingent upon any substance encryption techniques that might be being used)
• Reverse build exclusive conventions utilized over the system
• Debug customer/server interchanges
• Debug arrange convention executions
• Verify includes, moves and changes
• Verify interior control framework viability (firewalls, get to control, Web channel,
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3353 Figure 2: View Enabled Protocols for Analysis
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3354 Figure 4: Analysis of all packets
Superior IDS and IPS based Library of Snort: Snort is an open source device written in C utilized as system interruption avoidance and identification framework (IDS/IPS) created by Sourcefire. It is having astounding blend of the advantages of mark, convention, and oddity based assessment. The instrument is related with a huge number of downloads and about 400,000 enlisted clients, Snort has turned into the true standard for IPS.
Grunt can execute convention examination and substance examination with number of different highlights including discovery of an assortment of assaults and tests, for example, cushion floods, stealth port sweeps, CGI assaults, SMB tests, OS fingerprinting endeavors, and substantially more. Grunt makes utilization of an adaptable principles dialect to clarify the movement that it should gather or go, and also a location motor that uses a measured module design.
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3355 the parcels to the circle. In interruption location mode, the apparatus screens the system movement and breaks down it against a standard set characterized by the client.
The fundamental arrangement document is/and so on/grunt/snort.conf. In this arrangement record, the real data of the system or framework is determined that is under scrutiny. All qualities and parameters are remarked in the document with the goal that the progressions should be possible effortlessly.
Conclusion and Scope of Future Directions
In the domain of security towards the web based applications, there exist enormous perspectives which are required to be addressed and worked out. Following are few of the aspects and research points which can be solved by the researchers, corporate organizations and the academicians in the segment of network audit, evaluation and forensic based audit of network modules
Biometric integrated Access for Secured Web Portals
Development of Trust Architecture for Secured Network and Cloud Applications Integrity Aware Vulnerability Recognition in Secured Network Applications Deep Learning based Identification of Suspects in the Access of Web Applications
The packet tracing or sniffers are also used by the hacking community to analyze the data packets but as far as constructive purpose is there, such tools are very useful for the network administrators. The network administrators and engineers can analyze the type of packets flowing in their network infrastructure, bandwidth issues, port and protocols using such tools.
References
[1] Xue Y, Meng G, Liu Y, Tan TH, Chen H, Sun J, Zhang J. Auditing Anti-Malware Tools by Evolving Android Malware and Dynamic Loading Technique. IEEE Trans. Information Forensics and Security. 2017 Jul 1;12(7):1529-44.
Available online: https://edupediapublications.org/journals/index.php/IJR/ P a g e | 3356 [3] Kolosnjaji B, Demontis A, Biggio B, Maiorca D, Giacinto G, Eckert C, Roli F.
Adversarial Malware Binaries: Evading Deep Learning for Malware Detection in Executables. arXiv preprint arXiv:1803.04173. 2018 Mar 12.
[4] Mohan AK, Sethumadhavan M. Wireless Security Auditing: Attack Vectors and Mitigation Strategies. Procedia Computer Science. 2017 Dec 31;115:674-82.
[5] Düllmann TF, Heinrich R, van Hoorn A, Pitakrat T, Walter J, Willnecker F. CASPA: A Platform for Comparability of Architecture-based Software Performance Engineering Approaches.
[6] Halili EH. Apache JMeter: A practical beginner's guide to automated testing and performance measurement for your websites. Packt Publishing Ltd; 2008 Jun 27. [7] Rawal BS, Karne RK, Wijesinha AL. Mini Web server clusters for HTTP request
splitting. InHigh Performance Computing and Communications (HPCC), 2011 IEEE 13th International Conference on 2011 Sep 2 (pp. 94-100). IEEE.
[8] Srisuresh P, Holdrege M. IP network address translator (NAT) terminology and considerations. 1999.
[9] Bonomi F, Milito R, Zhu J, Addepalli S. Fog computing and its role in the internet of things. InProceedings of the first edition of the MCC workshop on Mobile cloud computing 2012 Aug 17 (pp. 13-16). ACM.
[10] Mirkovic J, Reiher P. A taxonomy of DDoS attack and DDoS defense mechanisms. ACM SIGCOMM Computer Communication Review. 2004 Apr 1;34(2):39-53. [11] Braga R, Mota E, Passito A. Lightweight DDoS flooding attack detection using
NOX/OpenFlow. InLocal Computer Networks (LCN), 2010 IEEE 35th Conference on 2010 Oct 10 (pp. 408-415). IEEE.
[12] Jin S, Yeung DS. A covariance analysis model for DDoS attack detection. InCommunications, 2004 IEEE International Conference on 2004 Jun 20 (Vol. 4, pp. 1882-1886). IEEE.
[13] Li L, Lee G. DDoS attack detection and wavelets. Telecommunication Systems. 2005 Mar 1;28(3-4):435-51.