ATM Card Authentication with Hardened Retina Based Fuzzy Vault for Highest Level of Security
Full text
Figure
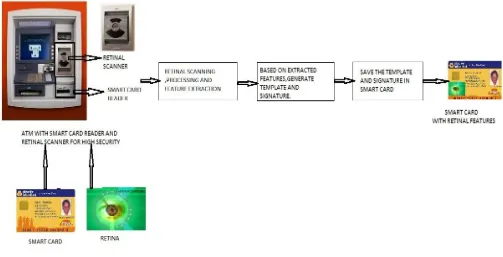
![Figure 3: Feature Extraction[1]](https://thumb-us.123doks.com/thumbv2/123dok_us/705235.1078581/3.595.316.544.338.570/figure-feature-extraction.webp)
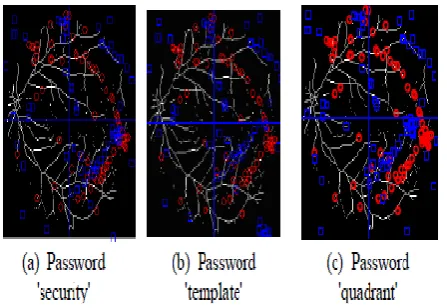
![Table III: False Rejection Rate (FRR) (%) Comparison[3]](https://thumb-us.123doks.com/thumbv2/123dok_us/705235.1078581/5.595.40.283.447.756/table-iii-false-rejection-rate-frr-comparison.webp)
Related documents
To demonstrate whether the syntactic and prosodic structures function in the same way in tone change and tone Sandhi, the numeral morpheme wu (‘five’) that
The extracts from the eyes of the several mutant stocks all gave ab- sorption curves similar t o that of wild type but with lower absorptions in the visible, indicating that
We have provided a comprehensive cyber security incident management playbook and discussed the various components of the playbook, showing how this can be applied to
First review stage: Statements and documentation to warden: Note that the BOP will require not only statements laying out the reasons for the request, but also
in area of crime control, criminology and criminal justice closely merge criminal justice academic education and training.. similarities between
Also, position and research papers pertaining to mental health programs for low income groups, collective bargaining issues relating to job security for mentally ill workers,
The CICTT categories found to show a significant decreasing trend are abnormal runway contact, aerodrome, CFIT, collision with object (approach/landing), collision with
Successive Optimization Tomlinson Harashima Precoding Strategies for Physical Layer Security in Wireless Networks Lu et al EURASIP Journal on Wireless Communications and Networking
