Cyber Security Risks and Challenges in Supply Chain
Full text
Figure

Related documents
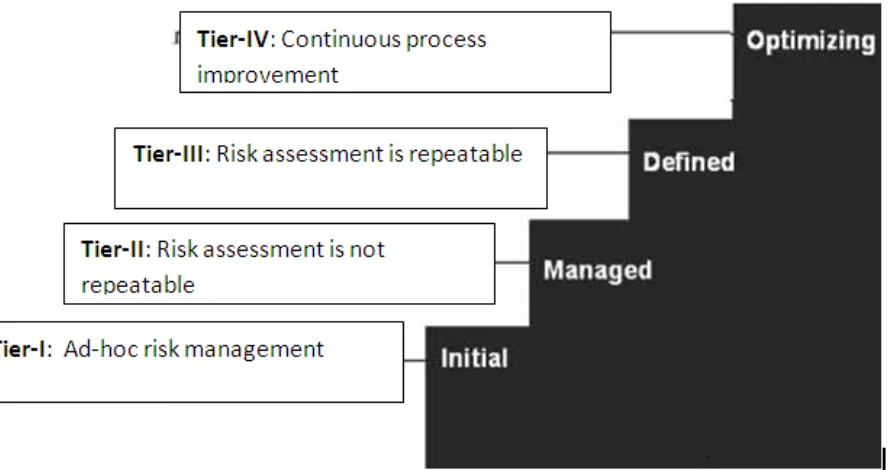
The purpose of Cyber Risk Management is to identify, analyze, and mitigate cyber-security threats and risks to critical information and technology assets and services. Risk
** COMMISSIONER BROWN MOVED TO GRANT PERMISSION FOR THE NORWALK EXCHANGE CLUB TO HANG BLUE LIGHTS ON THE TREE IN ROGER LUDLOW TRIANGLE FOR THE MONTH OF APRIL 2015.. **
In 2002, TxDOT again honored Shahan by naming him “General Aviation Airport Manger of the Year”, and in 2006, the Grayson County Airport (now known as North Texas Regional Airport)
Alternator Engine stop Coolant overheat Hydraulic oil level Auto lubrication Fast-filling Tension Electric lever Emergency engine stop Top valve.. Engine over run Coolant level
In addition, the Euclidean distance among these objects as well as among objects and clusters in figure 4 can be correctly measured, since the space shown in figure 4 is a
India has opened its telecom sector to foreign investors up to 100 percent holding in manufacturing of telecom equipment, internet services, and
An explanatory paragraph following the opinion paragraph, describing that (i) the statement of social insurance presents the actuarial present value of the agency’s estimated
The result of this study shows that faculty credentials, academic calendar, campus facility, research facility and cost of education are associated with quality