DOI : 10.32628/CSEIT1952240
An Enhanced Framework for Multi-Keyword Search on Encrypted Data
Darshana Khadse1, Harshada Gote1, Mayuri Pardhi1, Nikita Thag1, Nikita Bhakre1, Prof. Nutan Sonwane2 1BE Scholar, Department of Computer Science & Engineering, Dr. Babasaheb Ambedkar College of Engineering
and Research, Nagpur, Maharashtra, India.
2Assistant Professor, Department of Computer Science & Engineering, Dr. Babasaheb Ambedkar College of
Engineering and Research, Nagpur, Maharashtra, India.
ABSTRACT
In Information Networks, owners can store their reports over passed on various servers. It encouraging clients to store and get to their data in and from different servers by settling down wherever and on any gadget. It is an incredibly troublesome assignment to give the gainful search for on scattered records likewise give the security on owner's reports. The present framework gives one conceivable course of action that is security defending ordering (PPI). In this framework, records are scattered over various private servers which are everything viewed as constrained by cloud/open server. Precisely when the client requires a few reports, they ask for to open cloud, which by then reestablishes the sure rundown that is private server once-over to clients. In the wake of getting the outline, the client can search for the records on the explicit private server anyway in this structure; reports are verified perfectly healthy on a private server that is protected is traded. In any case, the proposed structure improves this present framework to impact it all the more excessively secure and skilled. In any case, records are verified in the encoded diagram on the private servers and after that utilization Key Distribution Center (KDC) for permitting decoding of data got from a private server, at the customer side. The proposed structure additionally executes TF-IDF, which gives the arranging of results to clients.
Keywords : Information Network, Private Server, Public Cloud, Distributed Databases, Ranking Results
I. INTRODUCTION
In Information Networks, owners can store their accounts over passed on various servers. It asking clients to store and get to their data in and from different servers by settling down wherever and on any gadget. It is an incredibly troublesome undertaking to give the profitable search for on scattered records, in addition, give the security on owners accounts. The present framework gives one conceivable game-plan that is protection sparing ordering (PPI). In this structure, records are scattered over various private servers which are everything viewed as constrained by cloud/open server. Right
examine an arrangement of power affiliations one that she can obviously trust or even can dispatch an individual server administrated unmistakably with no other person. The data sort out does not require shared trusts between servers, that is, an owner just needs to trust her own specific server and nothing more.
Data systems make in a gathering of utilization territories. For a case, in the undertaking intranet (for example IBM YouServ structure [1], [2]), agents can store and deal with their own particular records on inevitably administrated machines. While the operators have their own security concerns and could set up get the chance to control blueprints on the near to records, they might be required by the corporate dimension association social event to share certain data for moving potential joint undertakings [2]. For another portrayal, two or three streamed easygoing gatherings for example Diaspora [3], Status [4] and Persona [5]) beginning late climb and end up being powerfully remarkable, which depend upon the course of action of decoupling the point of confinement of social data and long-range easygoing correspondence supportiveness. Not at all like the unified solid long-range easygoing correspondence (for example Facebook and LinkedIn), the appropriated social affiliations enable a common social client to dispatch an individual server for verifying her own particular social data and executing self-depicted find the opportunity to control rules for security watchful data sharing [6]. Various examples of data systems combine electronic Healthcare over the general open Internet (for example the open-source NHIN Direct meander [7]), circulated record providing forget to controls [8] and others. In every single one of these systems, a data owner can have a select zone for the relationship of physical assets (e.g., a virtual machine) and data association of individual data under the full client control. Spaces organized inside different servers are pulled back and tended to between each other.1
Information sharing and trades over a zone oblige are engaging for different application needs.
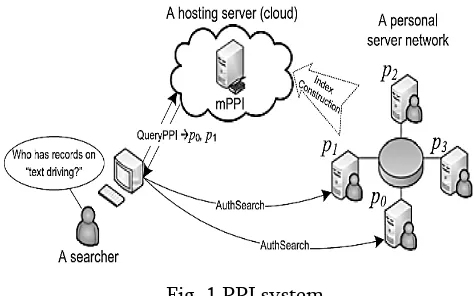
For security watchful demand and data partaking in the data deals with, a hopeful strategy is protection ensuring report on getting to controlled orbited records [9], [10], [11], or PPI for short. In Fig. 1, a PPI is a record advantage supported in a third-social event substance (for example an open cloud) that serves the general data to various data customers or searchers. To discover reports of intrigue, a searcher would share in a two-engineer look framework: First, she addresses a demand of important catchphrases against the PPI server, which gives back a quick overview of applicant owners (for example p0 and p1) in the structure.
In the wake of getting a synopsis, client can search for the records on the explicit private server anyway in this framework; reports are verified alive and well on a private server that is protected is wrangled. In any case, the proposed framework upgrades this present structure to impact it more to verify and proficient. Regardless records are verified in the encoded layout on the private servers and after that utilization Key Distribution Center (KDC) for permitting deciphering of data got from a private server, at customer side. The proposed framework besides executes TF-IDF, which gives the arranging of results to clients.
By then for each lively owner in the quick overview, the searcher contacts its server and asking for client insistence and support before searching for locally there. See that the assertion and support just happen inside the data coordinate, yet not on the PPI server.
Showing up diversely in connection to existing work on secure data serving in the cloud [12], [13], [14], the PPI configuration is phenomenal as in 1) Data is verified in plain-content (for example without encryption) in the PPI server, which makes it attainable for proficient and flexible data giving rich handiness. Without utilization of encryption, PPI stick client protection by adding turmoil ridden situations to cloud the sensitive ground truth data. 2) Only coarse-grained data (for example the obligation regarding searched for verbalization by an owner) is verified in the PPI server, while the primary substance which is private is up 'til now kept up and ensured in the individual servers, under the client chose get the chance to control rules.
In the PPI structure, it is speaking to give secluded security affirmation with respect to various hunt request and owners. The data shows utilized as a bit of a PPI structure and a data system is that every server has assorted records, each containing different terms. What is respected private and ought to be verified by a PPI is the ownership data as "whether an owner has no shy of what one record vital to a multi-term express." Under this model, the centrality of secluded security assurance is of two folds: 1) Different (single) terms are not viewed as climb to the extent how sensitive they appear to be. For instance, in an eHealthcare sort out, it is commonplace for a lady to consider her as accommodating record of an "inauspicious birth" errand to be essentially more delicate than that of a "hack" treatment. 2) A multi-term state, as a semantic unit, can be a magnificent plan continuously (or less) delicate than a solitary term contained in the explanation. For example, "substance" and "driving"
are two terms that might be regarded non-delicate in their lone appearances; anyway a record of "content driving" can be viewed as increasingly insecure.
The current PPI work [9], [10], [11], while proposed to ensure protection, isn't set up to detach security safeguarding on various terms. In light of the quality-practical person strategies utilized for structure up these PPIs, they can't pass on a quantitative affirmation for security ensuring for demand of a solitary term, likewise that of a multi-watchword express.
In this paper, we propose ϵ-MPPI, another PPI considering which can quantitatively control the security spillage for multi-watchword record look. In the ϵ-MPPI structure, obvious verbalizations, be it either a solitary term or a multi-term enunciation, can be delineated with a proposed degree on security, suggested by ϵ. ϵ can be of any a help from 0 to 1; Value 0 tends to unimportant weight on security conservation, while respect 1 goes for the best protection ensuring (potentially to the damage of additional demand overheads). By this recommends, an assailant, searching for a multi-term state on ϵ -MPPI, can just have the sureness of mounting practical strikes limited by what the enunciation's security degree licenses.
Building a ϵ-MPPI from a data structure is endeavoring from the reasons for both the estimation and framework plots. Computationally, the ϵ-MPPI improvement requires watchful course of action to actually consolidate false positives (for example an owner who does not have a term or an explanation wrongly claims to have it) with the objective that a true blue positive owner can be covered among the bogus positive ones, along these lines protecting security.
is essential and charming to make ϵ-MPPI safely without a spot stock in ace. The errand of dispersed secure improvement would be to an incredible degree testing. On one hand, making ϵ-MPPI to meet the stringent security objectives under various multi-term looks while obliging additional pursuit expenses can be basically appeared as an improvement issue, dealing with which requires complex calculations, for example, a non-straight programming or NLP.
Then again, while the key understanding for secure estimations (as required by the safe ϵ-MPPI improvement) is to utilize a multi-party check (MPC) structure or MPC [15], [16], [17], [18] which ensures input data protection, the current MPC philosophies can work in every way that really matters well just with a basic outstanding burden in a little system. For instance, FairplayMP [16], an administrator significant MPC arrange, "needs around 10 seconds to review (incredibly immediate) limits" [19] which should generally be possible inside milliseconds by the dependable non-secure estimation. Direct applying the MPC system to the ϵ-MPPI progression issue which fuses a mind boggling estimation and a critical number of individual servers could impel to a cost that is really amazing and in each functional sense unsatisfactory. To address the inconveniences of able secure ϵ-MPPI headway, our middle thought is to draw a line between the ensured part and non-secure part in the figuring show up. We keep the secured figuring part anyway much as could reasonably be typical by looking into assorted procedures (for example check reordering).
By along these lines, we have reasonably withdrawn the puzzling NLP tally from the MPC part to such an extent, to the point that the costly MPC in our ϵ -MPPI headway custom just applies to a to an incredible degree clear computational errand, thusly driving general structure execution.
The contribution of this paper can be abridged as taking after.
• We proposed ϵ-MPPI to address the necessities of isolated privacy security of multi-term communicates in a PPI structure. To best of our understanding, ϵ-MPPI is the key wear down the issue. ϵ-MPPI guarantees the quantitative privacy protection by means of correctly controlling the false promising focuses in a PPI and in this way effectively compelling an attacker's assurance.
• We proposed a suite of sensible ϵ-MPPI improvement traditions material to the arrangement of normally untrusted singular servers. We especially thought to be both the single-term and multi-term state cases, and enhanced the execution of the safe ϵ-MPPI improvement from the two edges of estimation model and system design by researching the considerations of reworking the ensured figuring endeavors however much as could be normal
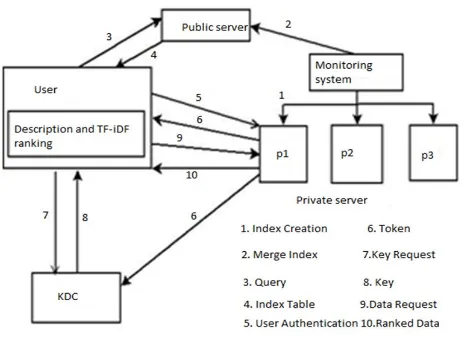
private server at which question related data is verified. By then to get to the data at server, customer sends the insistence demands with client name and watchword.
Fig. 2: System Architecture
Private server affirms this unobtrusive components store in its database. After productive check, private server makes the token and sends it to client and Key Distribution Center (KDC). In the wake of getting these token, customers request to KDC for a key. KDC affirm this token with its token which is starting at now getting from private server. After check, KDC gives encryption key to the client. By then client send information request to private server in returns server gives all planning mixed reports. Using key client can unscramble the information. Finally apply the TF-IDF situating estimation, to get all results in situating design.
System consisting of following modules:
•System Deployment
Registration And Login with Database, Client and Server with attachment programming and information exchange AES Encryption and Decryption with Client side GUI.
•MPPI Index creation algorithm
MPPI calculation is utilized for making list of all private servers. List speaks to the detail portrayal of information store at private server.
•Index combining and Upload on Public Server
Checking framework is in charge of joining list of every private server and transfers this last consolidation file record on open cloud.
• Input Query and Response From Public Server Client represents an inquiry to cloud server for receiving specific information from private server consequently open cloud gives consolidate file.
• Client Authentication and token generation
Subsequent to getting file, client needs to associate with private server to get the outcomes. Client login to the server and in the wake of finishing effective validation, private server create and disseminate the token to client and KDC.
• Key Distribution and File Decryption
After check of tokens, KDC give the way to client to decoding of results got from private server.
• TF IDF Ranking Results
After confirmation, client gets the outcomes from private server in scrambled organization. These scrambled outcomes are then unscrambled utilizing key acquired from KDC. At long last create the positioning of comes about by utilizing TF IDF.
III. CONCLUSIONS
The proposed framework is tied in with interfacing between neighborhood server and cloud server for data sharing among the clients. Some endorsement is required to get to explicit data or data. This endorsement is overseen through encryption structure. For reasonable execution of secure checks, it proposes Associate in Nursing MPC lessening structure upheld the conventionalist use of mystery sharing plans. In this way, through the proposed framework client can get a way to required data in arranged sort out utilizing PPI and encryption system.
IV. REFERENCES
[1]. Yuzhe Tang and Ling Liu,”Privacy
TRANSACTIONS ON KNOWLEDGE AND DATA ENGINEERING, VOL. 27, NO. 9, SEPTEMBER 2015
[2]. R. J. Bayardo Jr, R. Agrawal, D. Gruhl, and A.
Somani, “Youserv: A web-hosting and
content sharing tool for the masses,” in Proc.
11th Int. Conf. World Wide Web, 2002, pp. 345–354.
[3]. M. Bawa, R. J. Bayardo Jr, S. Rajagopalan, and
E. J. Shekita, “Make it fresh, make it quick: Searching a network of personal webservers,”
in Proc. 12th Int. Conf. World Wide Web, 2003, pp. 577–586.
[4]. [Online]. Available: Diaspora: https://joindiaspora.com/, 2014.
[5]. [Online]. Available: Status, http://status.net, 2014.
[6]. R. Baden, A. Bender, N. Spring, B.
Bhattacharjee, and D. Starin, “Persona: An
online social network with user-defined
privacy,” in SIGCOMM Conf. Data Commun.,
2009, pp. 135–146.
[10]. “Homeviews: Peer-to-peer middleware for
personal data sharing applications,” in Proc.
SIGMOD Conf., 2007, pp. 235–246.
preserving indexing for ehealth information
networks,” in Proc. 20th ACM Int. Conf. Inf.
Knowl. Manage., 2011, pp. 905–914.
[15]. M. Bawa, R. J. Bayardo, Jr, R. Agrawal, and J.
Vaidya, “Privacy preserving indexing of documents on the network,” VLDB J., vol. 18,
no. 4, pp. 837–856, 2009.
[16]. R. A. Popa, C. M. S. Redfield, N. Zeldovich,
and H. Balakrishnan, “CryptDB: Protecting
confidentiality with encrypted query
processing,” in Proc. 23rd ACM Symp.
Operating Syst. Principles, 2011, pp. 85–100. [17]. C. Gentry, “Fully homomorphic encryption
using ideal lattices,” in Proc. 41st Annu. ACM
Symp. Theory Comput., 2009, pp. 169–178. [18]. N. Cao, C. Wang, M. Li, K. Ren, and W. Lou,
“Privacy-preserving multi-keyword ranked
search over encrypted cloud data,” in Proc.
IEEE INFOCOM, 2011, pp. 829–837.
[19]. D. Malkhi, N. Nisan, B. Pinkas, and Y. Sella,
“Fairplay—Secure two-party computation
system,” in Proc. 13th Conf. USENIX Security
Symp., 2004, pp. 287–302.
[20]. A. Ben-David, N. Nisan, and B. Pinkas,
“Fairplaymp: A system for secure multi-party
computation,” in Proc. ACM Conf. Comput.
Commun. Security, 2008, pp. 257–266. [21]. W. Henecka, S. K€ogl, A.-R. Sadeghi, T.
Schneider, and I. Wehrenberg, “TASTY: Tool
for automating secure two-party
computations,” in Proc. 17th ACM Conf.
Comput. Commun. Security, 2010, pp. 451–
462.
[22]. I. Damga rd, M. Geisler, M. Krøigaard, and J.
B. Nielsen, “Asynchronous multiparty
computation: Theory and implementation,”
in Proc. 12th Int. Conf. Practice Theory Public Key Cryptography, 2009, pp. 160–179. [23]. A. Narayan and A. Haeberlen, “DJoin:
Differentially private join queries over
distributed databases,” in Proc. 10th USENIX
Conf. Operating Syst. Des. Implementation, Oct. 2012, pp. 149–162.
Differential privacy: An economic method for choosing epsilon, CoRR [Online]. abs/1402.3329 Available: http://arxiv.org/abs/1402.3329
[25]. Y. Tang and L. Liu, “Multi-keyword
privacy-preserving search in information networks,”
Tech. Rep. 2014 [Online]. Available: http://tristartom.github.io/docs/tr-mppi.pdf, 2014.
[26]. Y. Tang, L. Liu, A. Iyengar, K. Lee, and Q.
Zhang, “e-PPI: Locator service in information
networks with personalized privacy
preservation,” in Proc. IEEE 34th Int. Conf.
Distrib. Comput. Syst., Madrid, Spain, Jun. 30–Jul. 3, 2014, pp. 186–197.
Cite this article as :
Darshana Khadse, Harshada Gote, Mayuri Pardhi, Nikita Thag, Nikita Bhakre, Prof. Nutan Sonwane, "An Enhanced Framework for Multi-Keyword Search on Encrypted Data", International Journal of Scientific Research in Computer Science, Engineering and Information Technology (IJSRCSEIT), ISSN : 2456-3307, Volume 5 Issue 2, pp. 680-686, March-April 2019.