University of Manitoba: Description of the PIE System Used for MUC-6
Full text
Figure
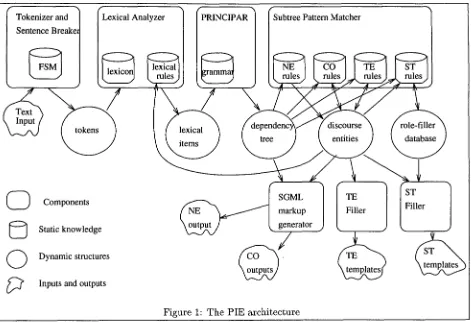

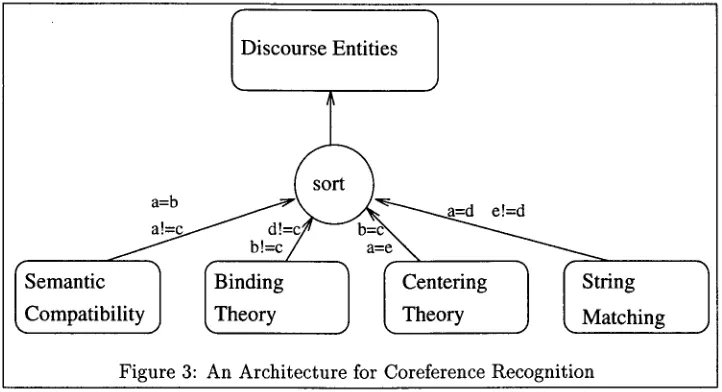

Related documents
Here Vehicle number plate is extracted by using the image segmentation and Optical character recognition technique which is used for the recognizing the character..
In pattern recognition, the K-nearest neighbor algorithm(K-NN) is a widely used classifier for classifying objects based on closest training examples in the
Although Abraham appeals to the way in which the canonical heritage is used in leading people to believe in canonical theism, this does not really accomplish the task in hand, for
At the base station, the sink node gathers data from wireless sensors using the ZigBee protocol and sends this data to Cloud based sensor data platforms.. Here
It eliminates Decryption overhead for users according to attributes .This secure attribute based cryptographic technique for robust data security that‟s being shared in the
28.Luther stel: ‘Ideo peccator est adhuc quisquis iustificatur. Et tamen velut plene et perfecte iustus reputatur, ignoscente et miserente Deo. Ignoscit autem et miseretur
The knowledge of our salvation is fundamentally linked to the question of original sin. The reductionism evident in limiting original sin to bodily lusts, leads to two errors: Firstly,
Van Selms meen dat dit ’n al te rasionele en oppervlakkige verstaan sou wees, wat nie rekening hou met (Luk 13:34; Van Selms s.a.):.. [D]ie feit van die werking van die gebod