Message Authentication, Revisited
Full text
Figure
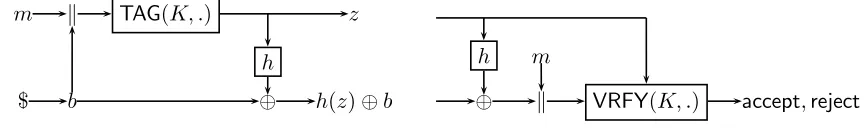


Related documents
Western blot analysis Western blotting was per- formed to characterize the ASD-1 polyclonal antibodies (raised to a potentially antigenic peptide of the ASD-1 protein) and
Theoretical expressions for internal pressure and free volume per unit molecules have been successfully eveluatede by considering thermodynamical properties like
The percentages of similarity between segments of M32 and the corresponding segments of strain LT2 (as shown by connecting lines), based on restriction enzyme analysis and
The simulation results show this estimated prior density represents the true distribution well enough so that the shrinkage (posterior) estimator not only has smaller variance
Aims:As differences in promoter activity and CD30 surface expression between CD30+ lymphoid cell-lines and peripheral blood leukocytes have been shown previously to
Plasmid pBRG554, generated by ligation of the BglII site in IS50R (just 5 bp away from the BclI site used to make pBRG557) and the BamHI site in pBR322, should encode a
In [7] the public variable C was the Initial Vector of a stream cipher and the cube variables were called weak IV bits whenever the de- rived function Γ turned out to be weak enough
For example, when u = 1, by Theorem 1.1, we obtain the following well-known results about the Kloosterman sums..