VCE Word Template Table of Contents
1
© 2011 VCE Company, LLC. All Rights Reserved.
VBLOCK™ GRC SOLUTION WITH RSA
(GOVERNANCE, RISK, AND COMPLIANCE)
August 2011
Contents
Executive Summary ... 3
The Challenge ... 3
The Solution ... 4
Governance, Risk, and Compliance (GRC) as a Business Requirement ... 6
Growing Need for Internal Governance ... 6
Increasing Regulatory Demands ... 6
IT GRC as the Foundation ... 6
VCE and RSA Approach to Implementing IT GRC ... 8
VCE Security Management Approach ... 8
RSA Solution for Cloud and Security Compliance ... 9
Integrated VCE and RSA Approach to IT GRC ... 10
Technology Overview ... 15
Vblock
™
Infrastructure Platforms ... 15
RSA Components ... 15
Solution Architecture ... 18
Creating the RSA Solution for Cloud and Security Compliance ... 18
Hardware and Software Resources ... 18
Configuration Details ... 19
Solution Validation: PCI-DSS Compliance Use Case ... 21
Step 1: Implement Phase – Device Discovery ... 22
Step 2: Implement Phase – Compliance Checks ... 23
Step 3: Validate Phase – Assess Environment ... 23
Step 4: Validate Phase - Remediate Findings ... 24
Conclusion ... 27
Next Steps ... 27
Additional References ... 28
Executive Summary
Businesses large and small are moving quickly to take advantage of the financial and operational efficiency of virtualized converged infrastructures. IT departments are now able to transform from a reactive cost center to an agile, proactive, strategic business differentiator.
Security and compliance are repeatedly cited as top concerns for adoption of cloud across all industry verticals. With more and more organizations embracing the move to virtualization, converged
infrastructure platforms, and different cloud deployment models, the need for automated and timely assessment of the virtualized infrastructure's compliance to business and regulatory requirements has never been greater.
IT organizations are being asked to manage and provide visibility into the security and compliance posture of this new environment while seamlessly integrating with existing risk management policies. This shift in the data center demands consolidation, automation, and centralized visibility to ensure those making the decisions see a complete picture within the context of business risk.
There is a growing need for internal governance in the face of increasing regulatory demands. VCE customers leveraging Vblock™ Infrastructure Platforms want the ability to assess their platform and the solutions and services it presents, and to ensure compliance through automated and standardized means.
The Challenge
According to a recent Forbes Insights report (Seeding the Cloud: Enterprises Set Their Strategies for Cloud Computing 2010), 48% of the 235 CIOs and IT executives surveyed stated that they have virtualized at least a quarter of their organization’s servers to reduce infrastructure costs and deliver applications more rapidly. This adoption is not without its concerns and challenges, with security identified as the top concern of 43% of the respondents. Governance, Risk, and Compliance (GRC), specifically IT GRC, addresses this clear demand.
The IT GRC domain focuses on the management of IT-related controls. This is vital to the converged infrastructure provider as surveys indicate security ranks highest amongst the concerns for using cloud-based solutions. The ability to ensure oversight and to effectively report on technical security controls (such as firewalls, hardening configurations, and access management services) and non-technical controls (such as consistent use of processes, background checks for employees, and regular review of policies) is paramount to the provider’s success in ensuring the security and compliance objectives demanded by their customers.
Key benefits of a robust IT GRC solution include:
§ Creating and distributing policies and controls and mapping them to regulations and internal compliance requirements
§ Assessing whether the controls are actually in place and working, and remediating them if they are not
The Solution
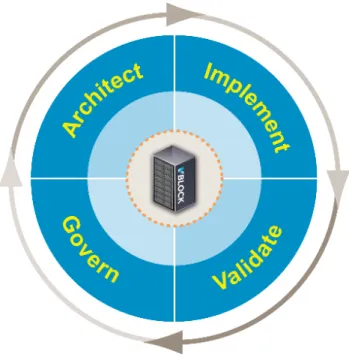
VCE has teamed up with RSA®, the security division of EMC, to define a solution that leverages the power and flexibility of the RSA Solution for Cloud Security and Compliance (based on the RSA Archer eGRC Suite) to manage and govern the virtualization infrastructure components of the Vblock platform. The solution applies VCE’s four-phased security approach of Architect, Implement, Validate, and Govern.
The RSA Solution for Cloud Security and Compliance provides a single pane of glass to manage the security compliance of the Vblock platform. Based on several modules within the Archer eGRC Suite, RSA offers the RSA Solution for Cloud Security and Compliance for VMware® environments, which enables organizations to apply governance policies and control standards to the virtualization infrastructure, perform continuous and automated monitoring, simplify remediation workflows, and centrally view their compliance posture. The solution is intended to provide security and compliance monitoring of virtual and consolidated infrastructures. These infrastructures can be deployed for use as public or private clouds.
In addition to providing a single point to manage compliance activities, RSA Archer eGRC provides powerful and real-time dashboards and reports to allow those in the governance role to quickly and easily view the state of the environment and make decisions based upon the context of business risk. The converged Vblock Infrastructure Platforms provide revolutionary opportunities for standardization and reduced capital and operating expenses through virtualization. The resulting Vblock GRC solution with RSA provides tightly integrated, automated, and consistent processes and provides the
transparency needed by the organization’s decision makers to manage the security and compliance of their converged infrastructure and make informed decisions within the context of business risk.
Scope
This paper demonstrates how to secure and govern the virtualization infrastructure of Vblock
Infrastructure Platforms using the RSA Solution for Cloud Security and Compliance. The specific goal of this paper is to provide the methodical, iterative approach from VCE and RSA in the use of the RSA Archer eGRC Suite and the RSA Solution for Cloud Security and Compliance. The focus is on IT GRC for Vblock platforms.
This document is not intended as a how-to guide for installing and configuring the RSA Archer eGRC Suite or the RSA Solution for Cloud Security and Compliance. For information on those topics, refer to RSA SecurBook: RSA Solution for Cloud Security and Compliance: A Guide for Deploying and
Audience
This paper is intended for Vblock platform customers in the following roles:
§ Security and compliance managers and analysts responsible for day-to-day management of security and compliance
§ Virtualization administrators
§ Those responsible for IT and Security governance, such as chief information officers, chief information security officers, chief financial officers, chief risk officers, or chief compliance officers
§ Vice-presidents and directors with delegated authority over GRC programs
Terminology
The following table contains terms used throughout this paper.
Term Description
Cloud Computing A model for enabling convenient, on-demand network access to a shared
pool of configurable resources (for example, networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.
Converged Infrastructure Packages multiple IT components into a single computing solution.
Components of a converged infrastructure include servers, data storage devices, virtualization, networking equipment, and software for IT infrastructure management.
Enterprise GRC (eGRC) Describes how an organization defines the objectives, policies, and
procedures by which it is managed; pursues opportunities while avoiding or managing negative events; and demonstrates adherence to laws,
regulations, policies, and industry standards. Governance, Risk, and
Compliance (GRC) Organizations leveraging GRC processesor internal framework for satisfying governance requirements, desire to establish a regulatory evaluate risk across their enterprise, and track how the organization complies with the
established governance requirements. GRC processes typically fall within
one of four key domains: IT, operations, finance and legal.
IT GRC A domain of GRC focused on the management of IT related controls.
These may include security controls such as firewalls and or security information management system, system controls, automation and
vulnerability monitoring tools, identity and access management systems, or disaster planning and recovery systems.
Private Cloud The cloud infrastructure is operated solely for an organization. It can be
managed by the organization or a third party and can exist on premise or off premise.
Governance, Risk, and Compliance (GRC) as a Business
Requirement
This section looks at industry-related governance and compliance requirements.
Growing Need for Internal Governance
The need for internal governance is greater today than ever before. With media attention shifting to companies that fail to protect the sensitive information to which they are obligated, businesses and their executives and board members have to focus on the way they conduct business. Through effective governance, they can ensure that day-to-day operations and compliance aligns with corporate strategy. As they are ultimately accountable, executives and boards of directors need accurate and transparent information to ensure compliance and manage risk in relation to their business requirements.
Virtualization offers a powerful new way to manage and use digital information, but it also creates new complexities for organizations in managing risk, threats, and compliance. In virtualized environments, static, physical perimeters give way to dynamic, logical boundaries defined by information and transactions. Information, virtual machines (VMs), and entire networks relocate in the blink of an eye in virtual environments, so GRC measures must be just as adaptive and closely monitored.
Increasing Regulatory Demands
An increasing number of regulations and industry requirements are being imposed on companies globally to ensure that they safeguard the data they process and store and follow the required processes. Non-compliance is no longer an option, as enforcement entities are imposing penalties, sometimes for multiple millions of dollars, and even imprisonment for those in responsible positions. More frequently, these regulations and requirements are defining outcomes instead of outlining the methods to achieve them.This leaves companies with the task of developing compliance programs, documenting how to achieve these outcomes, and producing evidence to that end.
As companies move through their action plans to satisfy their compliance objectives, they are expected to integrate with risk management practices. The days of a simple checklist are fading quickly.
IT GRC as the Foundation
Historically, IT’s role was to take charge of what needed to be done to meet internal, regulatory, and industry requirements. Faced with today’s new and ever-changing requirements, IT is expected to manage the technical and compliance challenges to align with company strategy. The daunting task of mapping the governing policies and standards to technical controls and processes are falling increasingly on IT.
The IT GRC domain focuses on the management of IT-related controls. This ability to ensure oversight and report on security controls (such as firewalls, hardening configurations, and identity access management) and non-technical controls (such as consistent use of processes, employee background checks, and regular review of policies) is paramount to the success of the organization in ensuring the security and compliance demanded by customers.
By extending practices and solutions into additional domains, organizations can build a strong IT GRC foundation into enterprise GRC.
VCE and RSA Approach to Implementing IT GRC
This section examines the VCE security and RSA solution-enabled approach to implementing IT GRC for the VMware components of Vblock Infrastructure Platforms.
VCE Security Management Approach
VCE addresses information security management comprehensively. By using an iterative, methodical approach to both overall product security and the development of each solution, VCE ensures a holistic approach and a complete solution to address its customers’ security and compliance challenges and requirements.
The VCE multi-phased approach of Architect, Implement, Validate, and Govern is based on the industry-proven quality control cycle of Plan, Do, Check, Act (Deming Cycle), as used in the
internationally accepted standard ISO 27001. This ensures a consistent, standardized approach in the management of security and compliance for Vblock platforms.
Figure 1. VCE Security Approach
This cycle consists of four phases, defined as follows. Phase Description
Architect Clearly identify the business need or challenge needing to be solved. Design an
approach to align and prioritize business requirements with centrally documented policies, standards, and procedures.
Implement Implement a solution to solve the business need of the challenge. Configure the
solution to discover VMware devices and check VMware-based controls with both automated measurements and electronic questionnaires.
Phase Description
Validate Regularly monitor the VMware-based controls and manage non-compliant findings
through remediation or exception management processes.
Govern Use the dashboard and reporting features to provide transparency and visibility to
both IT administrators and the business decision makers on the security and compliance posture of the Vblock platform.
RSA Solution for Cloud and Security Compliance
RSA has developed a solution that enables organizations to meet their security and compliance requirements as they move toward virtualization and the cloud. The RSA Solution for Cloud Security and Compliance enables end-user organizations and service providers to orchestrate and visualize the security of their VMware virtualization infrastructure and physical infrastructure from a single management console. The solution includes software that discovers new virtual infrastructure devices and substantially automates the assessment of whether security controls have been implemented correctly.
By mapping both the controls found in the VMware vSphere Security Hardening Guide and additional controls based on RSA best practices to global regulations and industry standards, organizations can quickly assess their Vblock platform against the requirements mandated by today’s ever-changing regulatory requirements.
The solution provides a security management process, simplified by a cycle that includes VMware security-policy implementation and management, security and compliance measurement, issue remediation, and reporting – all from a single console.
Integrated VCE and RSA Approach to IT GRC
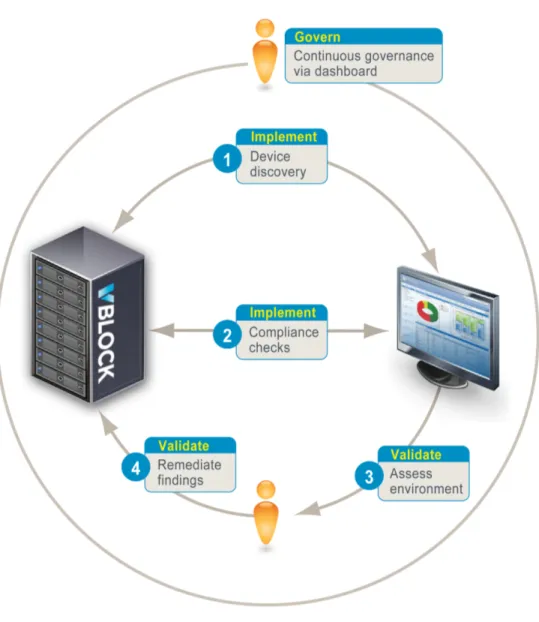
VCE and RSA have collaborated to provide a tightly integrated approach to security compliance, management, and governance. The approaches from each company complement and align with the other to address the need for a standardized, compliance-ready solution. Figure 3 shows how each phase of the VCE iterative approach maps to the RSA solution-enabled approach.
Architect Phase
This section looks at the Architect phase.
Define Policies
It is vital to have a clear understanding of the policies and requirements to which the environment must be governed. Organizations must comply with different regulatory requirements, based on their industry, business, and the data being processed and stored. The RSA Archer Library supports these regulatory requirements by providing more than 130 control procedures written specifically against RSA best practices and the VMware vSphere Security Hardening Guide and mapped to security policies and authoritative sources such as PCI-DSS, COBIT, NIST, HIPAA, NERC, Basel II, and EU Privacy Regulations.
The VMware-specific control procedures provide instructions for configuring and hardening the VMware infrastructure in the following areas:
§ Access control § Platform security § Information security § Operational security
RSA Archer can simultaneously evaluate the automated and manually collected compliance data against multiple authoritative sources, allowing for management against different requirements using the same data.
Establish Structure
To ensure transparency on the security and compliance posture of the VMware environment, it is important to define clear ownership of the various devices. The RSA Archer eGRC Suite provides the ability to map business data to the technical data collected automatically by the solution. This
business data helps ensure accountability and provides the foundation for the reporting structure used in the Govern phase. By populating RSA Archer with the appropriate business units, owners, and so forth, new devices will associate with their respective business data upon import.
Implement Phase
This section looks at the Implement phase.
Discovery and Compliance Check Configurations
After defining the policies, regulatory requirements, and business structure within RSA Archer eGRC, use the information to configure the RSA Automated Measurement Agent.
Install and configure the Automated Measurement Agent on a device having access to the VMware components of the Vblock platform. As this device has read-only credentials and network connectivity to the environment, it is important that it be controlled to maintain the confidentiality and integrity of the information.
N
Noottee:: The Automated Measurement Agent output files must be stored locally to the RSA Archer eGRC Suite to ensure successful import of the collected data.
Once the Automated Measurement Agent is creating output files, use the Data Feed Manager within the RSA Archer eGRC Suite to schedule the import of the collected data. Analyze the time required for each Automated Measure Agent to finish to ensure the Data Feed Manager import schedules allow time for the Automated Measurement Agent to complete.
Validate Phase
This section looks at the Validate phase.
Assess the Environment
With the Automated Measurement Agent configured and scheduled to run against the VMware environment, new devices and compliance findings against the devices will be automatically added to the solution.
N
Noottee:: It is recommended to run the discovery and compliance checks on a daily basis to ensure continuous visibility into the environment.
Newly populated devices require assessment against all the controls. Some cannot be assessed through automated means. Facilitate a manual assessment against each device by creating a web-based VMware questionnaire within RSA Archer to be answered by the device owners. Based on the responses to the questionnaire and the settings collected through automated means, RSA Archer automatically presents the status of the device as compliant or non-compliant.
Remediate Findings
After completing the questionnaire and populating the devices with the compliance issues found by the automated checks, generate Findings to engage the technical subject matter experts to remediate. Findings provide the subject matter experts with consistent, detailed information to remediate the compliance issues through step-by-step instructions and validation processes. RSA Archer tracks the completion progress of these Findings on the dashboard reports, providing transparency to those in the governance role.
Govern Phase
This section looks at the Govern phase.
Report and Govern
The RSA Solution for Cloud Security and Compliance provides Archer dashboard graphs and detailed reporting for those in the governance role. The RSA Archer eGRC Suite allows for customization of the reports and graphs and the addition and removal of reports, graphs, and so forth to meet the needs of those in the responsible role. The dashboard graphs and reports provide real-time access to the compliance status of the environment.
Technology Overview
Together VCE and RSA offer a robust and flexible solution based on industry-leading technology to business users needing visibility into the security and compliance posture of their virtualized infrastructure.
Vblock™ Infrastructure Platforms
Vblock Infrastructure Platforms are enterprise- and service provider-class IT infrastructure units that are pre-engineered, tested, and validated with pre-defined performance, capacity, and availability service levels. The standardized converged infrastructure of the Vblock platform is a foundational building block for cloud computing that helps customers to realize the benefits of applications running in a virtualized environment.
Vblock platforms are characterized by:
§ Repeatable units of construction based on matched performance, operational characteristics, and discrete requirements of power, space, and cooling
§ Repeatable design patterns that facilitate rapid deployment, integration, and scalability § An architecture that can be scaled for the highest efficiencies in virtualization
§ An extensible management and orchestration model based on industry-standard tools, APIs, and methods
§ A design that contains, manages, and mitigates failure scenarios in hardware and software environments
N
Noottee:: Refer to the Vblock Infrastructure Platforms Technical Overview for detailed information on the Vblock platform architecture.
RSA Components
RSA components include:§ RSA Archer eGRC Suite (Enterprise, Compliance, and Policy Management modules) § RSA Solution for Cloud Security and Compliance
RSA Archer eGRC Suite
The RSA Archer eGRC Suite supports business-level management of governance, risk, and
compliance with a customizable and flexible solution. Organizations derive significant value from being able to apply governance policies and control standards to VMware infrastructure, performing
continuous compliance monitoring, simplifying workflows, and centrally viewing their compliance posture within the context of business risk.
The RSA Archer eGRC Suite provides a comprehensive library of policies, control standards, procedures, and assessments mapped to current global regulations and industry guidelines. Control procedures are written specifically against the VMware vSphere Security Hardening Guide and mapped to security policies and authoritative resources such as PCI-DSS, COBIT, NIST (FIPS, FISMA, and so forth), HIPAA, and NERC.
When compliance issues are identified, the Archer library provides the technical details and step-by-step remediation and assessment instructions to successfully bring the device back to a compliant state.
Using automated workflow with RSA Archer eGRC, a project manager can distribute security policies and control procedures to appropriate administrators for both physical and virtual infrastructure and then track the implementation of those control procedures from a single dashboard interface. The RSA Archer eGRC Suite consists of three logical layers that are deployed on two physical tiers.
Logical Layers
The RSA Archer eGRC Suite architecture is divided into three logical layers:
§ Interface: A collection of ASP .NET pages that invoke the application layer to retrieve and manipulate data.
§ Application: A collection of C# objects that communicate with the database through a common database object that encapsulates stored procedure calls.
§ Database: A collection of stored procedures that act upon the underlying data model of the platform.
Physical Tiers
The RSA Archer eGRC Suite architecture is deployed on two physical tiers. Depending on the needs of your organization, these tiers can be hosted on a single server or deployed across multiple servers.
§ Web tier: Hosts the logical interface and application layers. The application server is installed on Microsoft Windows Server and requires Microsoft Internet Information Server (IIS) and .NET Framework.
§ Database tier: The database server is Microsoft SQL Server and consists of the framework database for platform content and the configuration database for web server configuration information.
Configurations
Organizations can deploy the RSA Archer eGRC Suite in a variety of configurations, based on the expected user load, utilization, and availability requirements. As business needs evolve, the environment can adapt and scale to meet the new demands.
The following table describes the most common deployment configurations. Configuration Description
Single host In a basic deployment scenario, the Archer eGRC Suite is run on a single
server, with the application and database components running on the same server. This configuration is suitable for organizations:
§ With fewer than 50 concurrent users
§ That do not require a high-performance or high-availability solution
Multi-host The multi-host configuration separates the database and web application on
different servers. This configuration provides greater flexibility, as the database layer can be scaled out separately from the application layer. In many instances, organizations can leverage existing SQL servers or clusters. For enhanced security, the multi-host configuration can incorporate a double-firewall. This configuration places a firewall in front of the web server and another between the web and database servers.
High-availability
multi-host For high-availability environments, the Archer eGRC Suite deploys on a minimum of two web/application servers and two database servers. Incoming HTTP(s) requests are directed across the web servers via a load balancer, using a “sticky” session load balancing approach that distributes loads based on server availability.
RSA Solution for Cloud Security and Compliance
The RSA Solution for Cloud Security and Compliance enables end-user organizations and service providers to orchestrate and visualize the security of their virtualization infrastructure and physical infrastructure from a single console. The solution extends the Enterprise, Compliance, and Policy modules within the RSA Archer eGRC Suite with content from the Archer Library, dashboard views, questionnaires, and continuous compliance monitoring to provide a solution for cloud security and compliance. It features an easy to use dashboard based on the RSA Archer eGRC Suite; the dashboard integrates with a library of more than 100 VMware-specific controls that map to the most current global regulations to ensure best practices for deployment.
Solution Architecture
VCE and RSA have collaborated to provide a solution architecture that is scalable and easy to deploy. Although the solution was validated on Vblock Series 700, it applies to all Vblock Infrastructure Platforms.
Creating the RSA Solution for Cloud and Security Compliance
After installing and configuring the RSA Archer eGRC Suite using the deployment approach best suited for your organization, the next step is to create the RSA Solution for Cloud Security and Compliance using the solution package available from RSA Archer Customer Support to licensed RSA Archer customers. This package contains all files and instructions required to successfully create and configure the solution in the RSA Archer eGRC Suite. An RSA SecurBook provides guidance for deploying and operating this solution.Organizations that require assistance with creating the RSA Solution for Cloud Security and
Compliance or that want to customize the solution to meet business requirements should contact RSA Sales (https://www.rsa.com/go/contactsales.asp) to schedule RSA Archer Professional Services. N
Noottee:: It is recommended that the RSA Archer eGRC Suite and RSA Solution for Cloud Security and Compliance be deployed in a manner supporting segregation from the infrastructure being monitored and managed. VCE vArchitects and RSA Professional Services can help determine the best manner for deployment to meet an organization’s requirements.
Hardware and Software Resources
The following table lists the hardware and software resources used to validate this solution.
Resource Description
Vblock 700 § Cisco UCS blade pack (2 chassis)
- 16 x B200 M1 (2 blades with 96 GB RAM, 14
blades with 48 GB RAM)
- 4 x 4 port UCS Extender card
§ Cisco Fabric Interconnect 6140
§ Cisco MDS 9506
§ EMC Symmetrix VMAX
§ VMware vSphere (version 4.1)
§ VMware vCenter Server (version 4.1)
RSA Archer eGRC Suite: Enterprise,
Compliance, and Policy modules Version 5.xxxx.xxx
RSA Solution for Cloud Security and
Compliance Version 1
Microsoft SQL Server 2005
Microsoft PowerShell Version 2
Configuration Details
In this validated solution, each VMware vSphere Hypervisor (ESXi) server was configured using service profiles on the Cisco UCS, per standard Vblock platform configuration practice. Additionally, nearly 50 virtual machines were configured based on different virtual machine templates and requirements.
Figure 4 shows a logical representation of the validation environment.
Figure 4 Validation Environment Diagram
The Automated Measurement Agent was installed and configured within the RSA Archer virtual machine to query the Vblock platform VMware vCenter servers – for the Advanced Management Pod (AMP) and for the Vblock platform, itself. The Automated Measurement Agent was configured to use read-only credentials in the VMware vCenter servers.
User accounts were created within RSA Archer and provided with rights and permissions through role-based controls. To categorize the VMware infrastructure components during discovery by the Automated Measurement Agent, several business units were created under the fictional company IT Unicorn, Inc. The business units and accounts are shown in the organizational chart in Figure 5.
Solution Validation: PCI-DSS Compliance Use Case
This solution demonstrates how the RSA Archer eGRC Suite manages and governs the VMware components of the Vblock Infrastructure Platforms using VCE’s four-phased approach of Architect, Implement, Validate, and Govern. By following the iterative approach outlined in this paper,
organizations can achieve continuous compliance against regulatory requirements such as PCI-DSS. The following scenario uses the fictional company IT Unicorn, Inc. and the business units and
accounts created during validation to show the automated solution described in this document. The scenario illustrates the ease with which devices can be brought under inspection for continued compliancy against PCI-DSS requirements, and how issues can be easily identified and remediated. N
Noottee:: The Architect phase was addressed during the set up of the organization structure and the defining of policies, as described in Configuration Details.
The scenario uses three roles, each with their own level of access and responsibilities in the IT GRC program.
Role Scenario
Name Description
Responsible leadership Tom Fergus C-level leader responsible for ensuring security and
compliance of the Vblock platform.
Security project manager Matt Wolfe Responsible for the administration and management of the
RSA Archer GRC framework. Ensures the collection of data into the solution and engages the appropriate system administrators for non-automated collections.
Virtualization administrator Sam Avery Responsible for the administration and management of the
VMware infrastructure for the Vblock platform. Figure 6 shows the steps performed in the validation process.
Figure 6. Validation Process
Step 1: Implement Phase – Device Discovery
During a scheduled query of the VMware vCenter Server managing the Vblock platform, the device Automated Measurement Agent discovers a newly created virtual machine named GlobalFin-Server1.
This device is identified as “Not Assessed” until the automated and manual assessment processes begin.
Step 2: Implement Phase – Compliance Checks
The configuration Automated Measure Agent queries the virtual machine and identifies settings found in the VMware vSphere Security Hardening Guide. The agent writes the findings of these compliance checks to an output file ready to be imported into the RSA Archer eGRC Suite and associated with the virtual machine.
Figure 7 shows the raw data findings for the GlobalFin-Server1 virtual machine.
Figure 7. Raw Data Findings
Step 3: Validate Phase – Assess Environment
The security program manager, Matt Wolfe, logs into the RSA Archer eGRC Suite and sees a new, non-compliant device in the Finance business unit. He begins the manual portion of the assessment by creating a VMware Questionnaire against the GlobalFin-Server1 virtual machine and assigns it to the device manager, Sam Avery, as shown in Figure 8.
Step A: Govern Phase - Dashboard View of Compliance
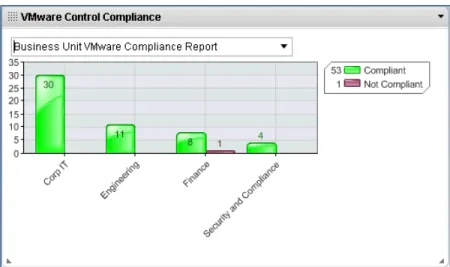
To ensure transparency and oversight of the process, Tom Fergus, the executive responsible for the GRC program for IT Unicorn, Inc. views the progress at both a granular and high-level view by business unit from the dashboard within the RSA Cloud Security and Compliance workspace. With the ability to view the compliance process as it progresses, Tom is able to understand the state of the
GlobalFin-Server1 virtual machine at any point in time.
Figure 9. Dashboard View of Compliance Findings
Step 4: Validate Phase - Remediate Findings
The final configuration item to bring GlobalFin-Server1 to a fully compliant state is the remediation of CP-107551 Remote Administrator’s Console Privacy. If left unattended, this non-compliant
configuration setting would allow a non-administrator to connect to the virtual machine console and observe an administrator’s session and actions.
Figure 10. Checking the Archer Library
Matt Wolfe engages the device manager, Sam Avery, with a remediation task. Sam Avery follows established change management processes and obtains the appropriate approvals; he then logs into the VMware vCenter Server and accesses the configuration parameters of the GlobalFin-Server1
virtual machine. He corrects the configuration values, as shown in Figure 11. Shortly after, Sam Avery completes the VMware Questionnaire for the GlobalFin-Server1 virtual machine.
Step B: Govern Phase - Dashboard View of Compliance
The next scheduled run of the Automated Measurement Agent reports the configuration setting for
GlobalFin-Server1 as Pass, which updates the status of the device to “Compliant.”
During his daily review of the environment, Tom Fergus sees that the VMware infrastructure for the Vblock 700 is in a compliant state against PCI-DSS requirements.
Conclusion
Organizations are undergoing a transformation to cloud computing. Brought on by the introduction of virtualization, this transformation is leading enterprises to reengineer their GRC management programs and methodologies to meet the demands and increasingly stringent expectations of both regulating authorities and a more informed public. At the same time, shareholders expect a reduction in capital and operating expenses as these requirements are being met.
Risk and compliance burdens are not going away. The globalization of business introduces significant risk with more points of vulnerability and exposure. The time is now for organizations to define and implement an eGRC strategy that drives accountability, consistency, security, and transparency. By selecting VCE as the vendor for converged infrastructure and RSA as the vendor for GRC, organizations can embrace virtualization knowing they can maintain compliance and manage risk through the consolidated, comprehensive, transparent approach this solution provides. With an easy to use web-enabled interface, the RSA Solution for Cloud Security and Compliance (based on the RSA Archer eGRC Suite) provides a consolidated framework to manage the security and compliance of the Vblock platform. With 130 virtualization-specific controls mapped to industry regulations, providers operating a Vblock platform can successfully monitor and manage their environment against different business requirements and regulatory mandates to satisfy the security and compliance concerns of their customers.
The need for automated and timely assessment of the virtualized infrastructure’s compliance to regulatory requirements has never been greater. The ability of the RSA Solution for Cloud Security and Compliance to regularly assess the environment for new or changed devices fills this need by enabling IT organizations to quickly provision virtualized devices in a matter of minutes versus days. With this business challenge met, organizations can now leverage their investments in the deployment of mission critical applications.
Next Steps
To learn more about this and other solutions, contact a VCE representative or visit http://www.vce.com.
Additional References
For additional information, see the documents listed below. § Vblock Infrastructure Platforms Technical Overview
http://www.vce.com/vblock/
§ RSA SecurBook: RSA Solution for Cloud Security and Compliance: A Guide for Deploying and Administering the RSA Solution for Cloud Security and Compliance
http://www.rsa.com/go/Securbook/Securbook_cloud_land.htm § VMware vSphere Security Hardening Guide
© 2011 VCE Company, LLC. All Rights Reserved. ABOUT VCE
VCE, the Virtual Computing Environment Company formed by Cisco and EMC with investments from VMware and Intel, accelerates the adoption of converged infrastructure and cloud-based computing models that dramatically reduce the cost of IT while improving time to market for our customers. VCE, through the Vblock platform, delivers the industry's first completely integrated IT offering with end-to-end vendor accountability. VCE's prepackaged solutions are available through an extensive partner network, and cover horizontal applications, vertical industry offerings, and application development environments, allowing customers to focus on business innovation instead of integrating, validating and managing IT infrastructure.
For more information, go to www.vce.com. ABOUT RSA
RSA, The Security Division of EMC, is the premier provider of security, risk, and compliance management solutions for business acceleration. RSA helps the world's leading organizations succeed by solving their most complex and sensitive security challenges. These challenges include managing organizational risk, safeguarding mobile access and collaboration, proving compliance, and securing virtual and cloud environments. Combining business-critical controls in identity assurance, encryption and key management, SIEM, Data Loss Prevention and Fraud Protection with industry leading eGRC capabilities and robust consulting services, RSA brings visibility and trust to millions of user identities, the transactions that they perform and the data that is generated.
For more information, go to www.rsa.com.
THE INFORMATION IN THIS PUBLICATION IS PROVIDED "AS IS." VCE MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND WITH RESPECT TO THE INFORMATION IN THIS PUBLICATION, AND SPECIFICALLY DISCLAIMS IMPLIED WARRANTIES OR MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE.
Copyright © 2011 VCE Company, LLC. All rights reserved. Vblock and the VCE logo are registered trademarks or trademarks of VCE Company, LLC. and/or its affiliates in the United States or other countries. All other trademarks used herein are the property of their respective owners.